I had a dream, a crazy dream, that we stopped responding to ridiculous email messages demanding that a wire be sent immediately. Also in that dream, all the bad guys were caught and had to pay restitution and go to jail.
While that second part may never happen, there has been definite progress toward the dream goal and there are definite steps to take to ensure that you – and others in your company – do not fall victim to a BEC email.
Coordinated by the National Cyber-Forensics & Training Alliance (NCFTA), contact information and incident details are being swapped quickly in the business and financial communities, allowing wires to be successfully recalled from far-flung places, facilitating the identification of fraudster activity, and preventing additional victimizations. However, the typical scenario involves the disappearance of money into the hands of criminals much faster than the victim realizes that they have made a grave mistake in acting upon a fraudulent email message.
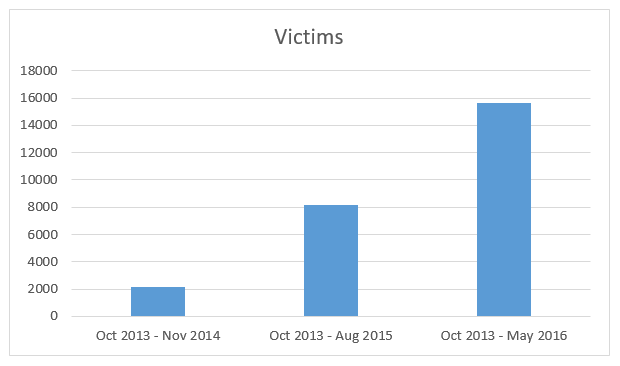
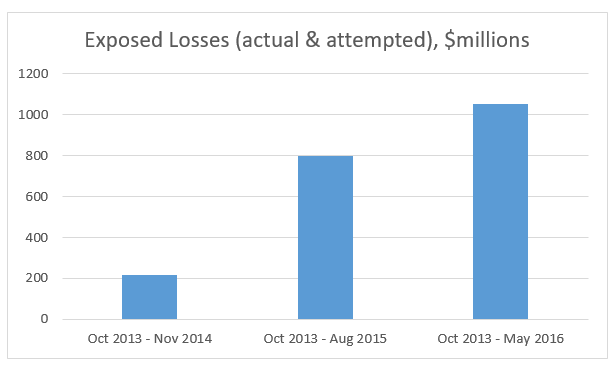
The FBI has now released three major advisories* regarding the Business Email Compromise scam. The below charts illustrate how the estimated number of victims and the estimated volume of dollar losses have increased dramatically with each Public Service Announcement.
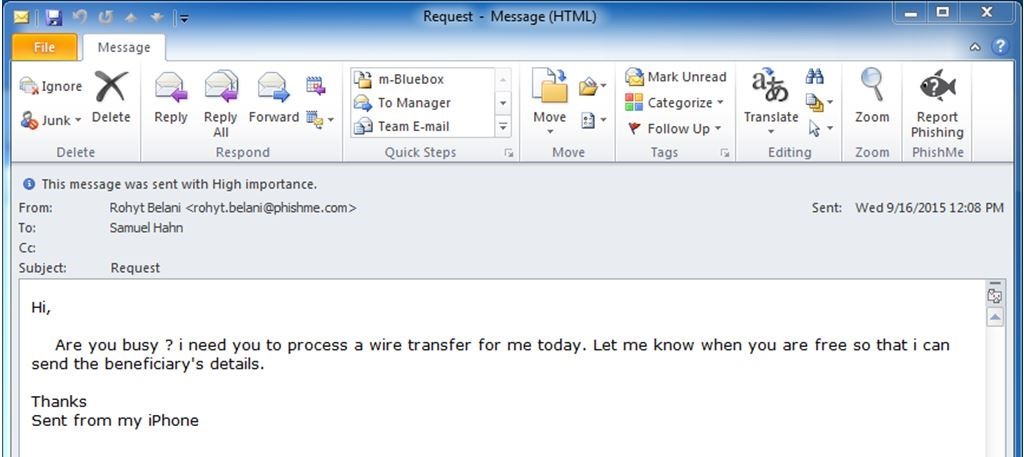
The most common sequence of events is that a C-level employee email address is either compromised or spoofed in order to send a convincing message to someone in the company with the authority to send a wire. It appears that oftentimes the fraudsters have done their homework on who’s who also, gleaning names, titles, and even travel schedules of executives from social media accounts. We have shared examples before; just over a year ago, PhishMe CTO, Aaron Higbee, described an attempt against PhishMe.
Also around this same time last year, Centrify CEO, Tom Kemp, detailed EIGHT different attempts against his company, which itself provides multi-factor authentication services.
Unfortunately, the number of victims continues to rise. Think about it…every business is a potential victim; so, until everyone knows how to spot this scam, we will keep hearing more horror stories.
The following are some things to keep in mind when you review an email asking you to move money on behalf of your company:
- Is the message really from the person that it appears to be from? Review the headers carefully. What is the reply-to address? Was the message actually sent from a lookalike domain name, such as PHlSHME.com with the letter L in place of the letter I?
- Does the tone and writing style of the author match what you know of the purported sender of the message?
- Are you being asked to reply directly to the message, instead of crafting a new email message? Are you being pressured to keep the transaction to yourself for some reason? Does the email message have a strong sense of urgency?
- Is there a link to click or an attachment to open, supposedly containing the wire instructions? As part of this scam, wiring instructions are typically sent to the victim in a subsequent message, after they have initially hooked you into responding. Usually they are in the body of the follow-up message, but sometimes they are in a PDF attachment.
- Don’t think that the receiving bank will necessarily be overseas. Money mules in the United States are operating domestic bank accounts, helping to launder the money while sometimes thinking they are performing a legitimate work-from-home service.
- Be willing to stand your ground when something seems ‘off’ about a request. Demand that you personally speak to the person requesting the urgent wire transfer. When you save the company millions, the CEO will be glad you bugged her for a moment.
And below are some Action Items that you can take today to help prevent becoming the next victim:
- Enable two-factor authentication on your email account. If your email provider does not offer this, change providers.
- Establish a DMARC record on your company domain so that messages spoofing your real domain do not get delivered.
- Use different passwords for each online service; use a password manager if needed.
- Require dual approval and out-of-band authentication for all wires. Understand that wire transfers are one of the most risky transactions and usually cannot be recalled because they are designed to provide immediate access to and an irrevocable settlement of funds.
- The PhishMe Simulator/Reporter combination conditions your employees to spot and submit fraudulent email messages. Contact PhishMe to sign up for Simulator and Reporter so that you can start shoring up your first line of defense.
If you realize that you may have fallen for this scam, call your bank immediately. Also call your local FBI office and ask for assistance (Find contact information here.) Even if you never wired the money, report the attempt by filing a complaint form with IC3 because this helps the NCFTA track and correlate attacks, improving the likelihood of an eventual prosecution.
*Links to the full FBI PSAs: