By Aaron Riley, Cofense IntelligenceTM
The Agent Tesla keylogger is an increasingly widespread piece of malware in the phishing threat landscape, targeting multiple industries and using multiple stages within its infection chain. Currently, threat actors prefer archived files or weaponized Microsoft Office productivity documents to deliver this malicious software to the endpoint. Agent Tesla is sold as a commercial subscription license and offers a 24/7 support team. With an easy to use and abundant feature set—like a document exploit builder embedded into the malware management web panel—this keylogger lends itself to all levels of threat actors.
A typical theme for these campaigns revolves around finances, orders, and shipments. The most common way for this keylogger to make it to the endpoint is by archiving the executable and attaching it to a phishing email. This delivery vector can be successful if the email security stack does not have a standard in place for allowed archival types, does not conduct archive file analysis, or determines the file to be an unknown archive type.
For the infection chain, there are numerous methods a threat actor can choose. Most notably, Agent Tesla leverages a document exploiting an equation editor vulnerability documented in CVE-2017-11882 as the first stage loader. Exploiting this vulnerability allows for the attached document to download and execute a binary on the victim’s endpoint once opened. Although a patch has been out for this vulnerability, threat actors continue to utilize it for exploits.
An Office macro-laden document is the second most popular ‘stage one’ loader for this keylogger. This is somewhat surprising, given the fact that the macro builder is embedded into the Agent Tesla web panel as a feature, thus making it easier than the CVE-2017-11882 exploit to capitalize on. As such, this keylogger demonstrates features that fit closer in line with a Remote Access Trojan (RAT), including the capability to take screenshots or control the webcam. Agent Tesla adds to its robustness with the ‘File Binder’ option which links a selected file on the endpoint to the Agent Tesla executable and executes the keylogger at the same time as the selected file. This is done to keep the keylogger up and running without interaction needed from the victim.
Unlike most RAT suites, Agent Tesla’s preferred exfiltration method for the stolen data is the use of email. The web panel allows for a threat actor to set an email address as the recipient or the sender and has the ability for the email traffic to be SSL encrypted. This exfiltration technique can be avoided by blocking all traffic using SMTP that does not match organizational or enterprise standards. Agent Tesla, however, can also exfiltrate the stolen information via FTP or an HTTP POST. Each of these exfiltration methods can be defended against with proper firewall, content filtering, and alerting rules in place.
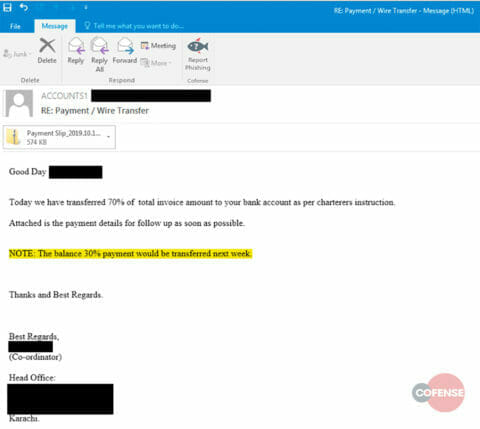
Figure 1: An example phishing email with Agent Tesla keylogger attached.
Agent Tesla’s recent rise to the top of the phishing threat landscape shouldn’t be a surprise, given the ease of use, options, and technical support from the creators. Network safeguards can help stop the exfiltration of data from a successful infection. Patching and updating user endpoints can combat at least one of the delivery mechanisms used within these phishing campaigns. Educating users on company standards for file extensions and Office macro use can combat the other two delivery mechanisms.
HOW COFENSE CAN HELP
89% of phishing threats delivering malware payloads analyzed by the Cofense Phishing Defense CenterTM bypassed email gateways. Condition users to be resilient to evolving phishing attacks with Cofense PhishMeTM and remove the blind spot with Cofense ReporterTM.
Quickly turn user reported emails into actionable intelligence with Cofense TriageTM. Reduce exposure time by rapidly quarantining threats with Cofense VisionTM.
Easily consume phishing-specific threat intelligence to proactively defend your organization against evolving threats with Cofense IntelligenceTM.
Thanks to our unique perspective, no one knows more about REAL phishing threats than CofenseTM. To understand them better, read the 2019 Phishing Threat & Malware Review.
All third-party trademarks referenced by Cofense whether in logo form, name form or product form, or otherwise, remain the property of their respective holders, and use of these trademarks in no way indicates any relationship between Cofense and the holders of the trademarks. Any observations contained in this blog regarding circumvention of end point protections are based on observations at a point in time based on a specific set of system configurations. Subsequent updates or different configurations may be effective at stopping these or similar threats.