In October of 2017 we blogged about a phishing campaign specifically targeting Brazilian Portuguese- speaking users.
Back then, the campaign distributed a malicious Chrome browser extension. More recently, we have observed a wave of emails that have remarkably similar characteristics. This time around, the malware of choice is a banking trojan.
In the image below, we see an email suggesting that it delivers a resume from a job-seeker. This message content may seem familiar as it has same characteristics we saw in the emails distributing the malicious Chrome extension. Each message contains a photograph of a woman with an identical text in both campaigns.
Image 1: Mail message received by users
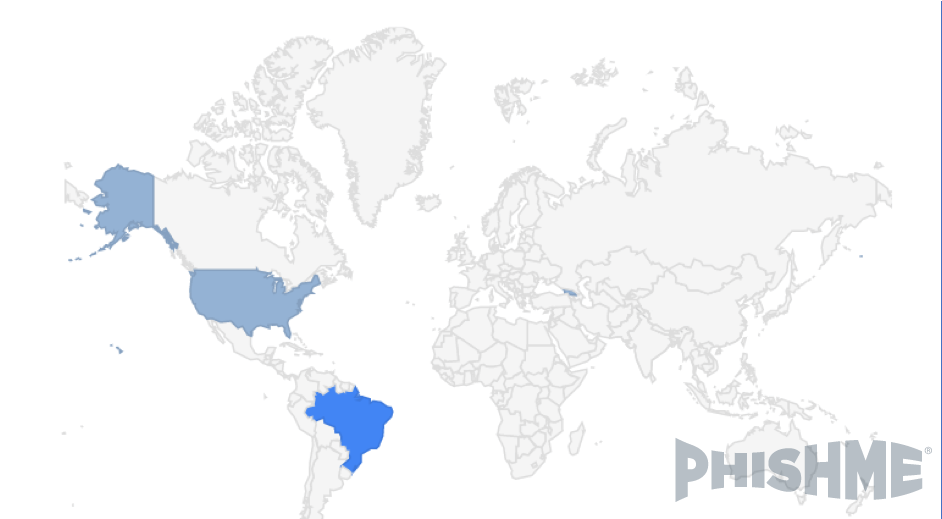
The message presents two links abusing the goo.gl URL shortening service. One points to the photograph that is shown in the message and the other enables the download of the malware. An analysis of the downloads made through these links, using the tools provided by the URL shortener service provider, reveals the impact by country.
Different shortened links were used in each wave of messages sent by these phishers. These URL shorteners usually point to a redirector, which in turn leads to the link that serves the first phase of the malware.
Sample redirector:
hxxps://julietemuoura[.]com[.]br/XgwK6iK.php?669651322
First malware stage:
hxxps://cld[.]pt/dl/download/588c9523-cf45-44b1-8dd6-55fe247af7c9/CURRICx002017.zip?download=true
This link provides victims with a ZIP archive. Inside, is the malware responsible for downloading the next stage.
Filename: CURRICx002017.zip
MD5: 17893B7BDE7C12BE81957DFA0179CAE7
SHA256: 1B2D13A8A6D8F9FB46892A1497A3408A57BC0BB575DFDE2866B3B203EAFA9129
Size: 17,200 bytes
Filename: CURRICx002017.exe
MD5: CCA79892602584CAD97EF588052BC8AF
SHA256: 09EC7EF8A22CA694186A2CEF068B75EECED4FB82A217B01A0773CD809878FC10
Size: 38,912 bytes
Upon execution, this malware pretends to be an instance of the Adobe Reader application. Meanwhile, in the background, the malware downloads its next component.
Image 3: Window shown by the first stage executable
The next component is a VBS script, downloaded through an HTTP request to the following URL:
hxxp://joguesix[.]com[.]br/fgtegerg2/load1.php
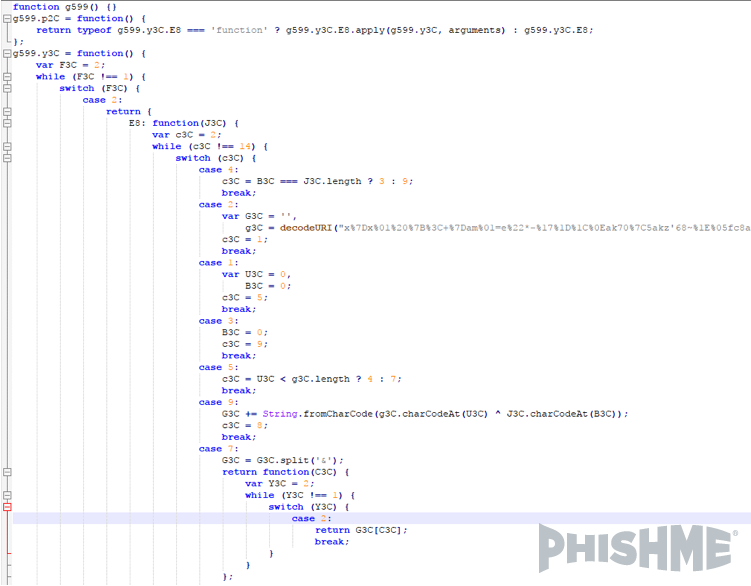
Image 4: Second stage encoded VBS script
Once deobfuscated, this script demonstrates the ability to perform a number of system inspection operations. These checks are performed to determine whether the machine is considered suitable to the attacker.
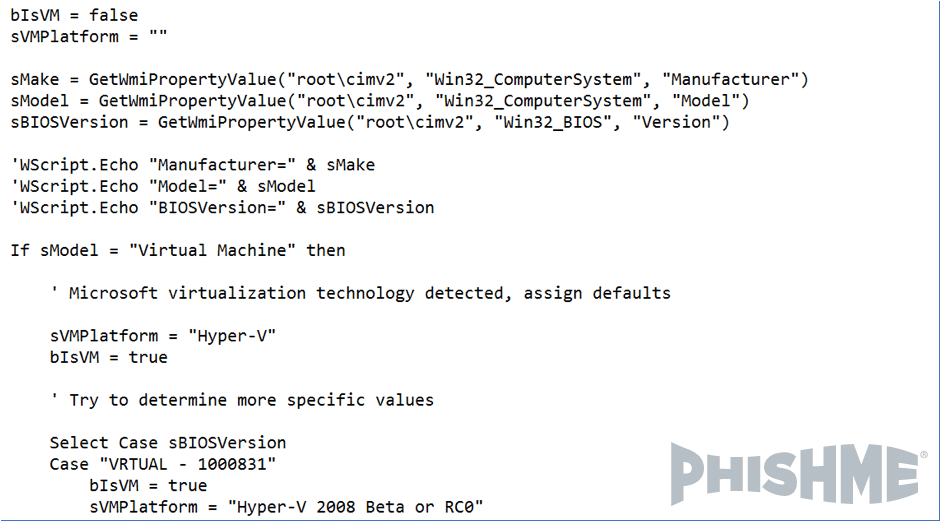
Image 5: Code used to detect the presence of virtualization
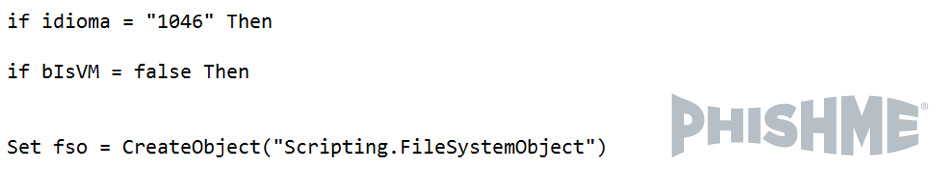
The script is designed to detect the language of the system. It also checks whether the machine is virtualized. These checks are performed as a means of evading analysis as well as to ensure the attack impacts computers that suit their preferences and needs. The malware will only continue with its execution if no virtualization has been found and the language is Portuguese (Brazil).
Image 6: Code used to detect the system language settings
The final result is the download of a last stage component from the following URL:
hxxp://joguesix[.]com[.]br/fgtegerg2/shta.klu
This component is a ZIP archive of names with a “.klu” extension:
Filename: shta.klu
MD5: 5525ED000EFE72910D3DC7F7FAEA1912
SHA256: 603CB8DE20803CC7E97643FAB4B50A709F9E9FC21F822EF2D1D7F5ABD8B751CA
Size: 232,875 bytes
Which contains the following file:
Filename: sht
MD5: 634F7F1262D71DAAE5890CC36AFF6952
SHA256: EE169075E79A5BFB9BA2BA13217484516E910652FDDD07768382EFE17615C724
Size: 275,456 bytes
This is a 32BIT DLL file written in DELPHI. Its initialization code is not present in the DllEntryPoint procedure. Instead, the DLL exports a function with the name SHTE443G11, which the previous component calls to continue with the infection process. Upon execution, it makes various requests to its control panel:
hxxp://joguesix[.]com[.]br/fgtegerg2/shta1.klu
hxxp://joguesix[.]com[.]br/fgtegerg2/shta9.klu
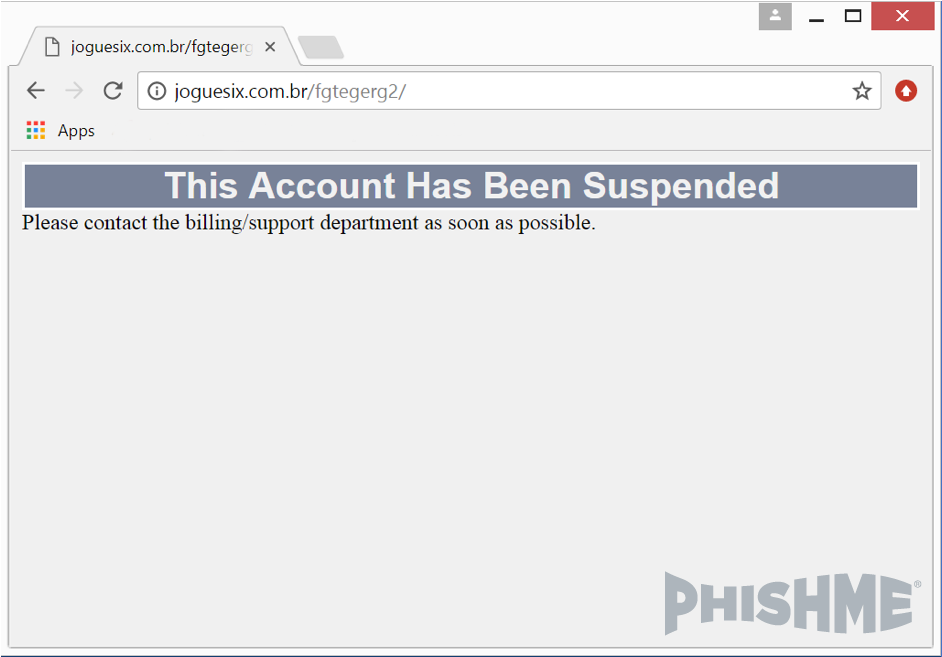
It is noteworthy that manual access to these links show us a “suspended account” page. In spite of this, the malicious components are present and downloaded without problems. This indicates that the “suspended account” message may be an intended decoy to mislead researchers.
Image 7: Manually accessing the control panel
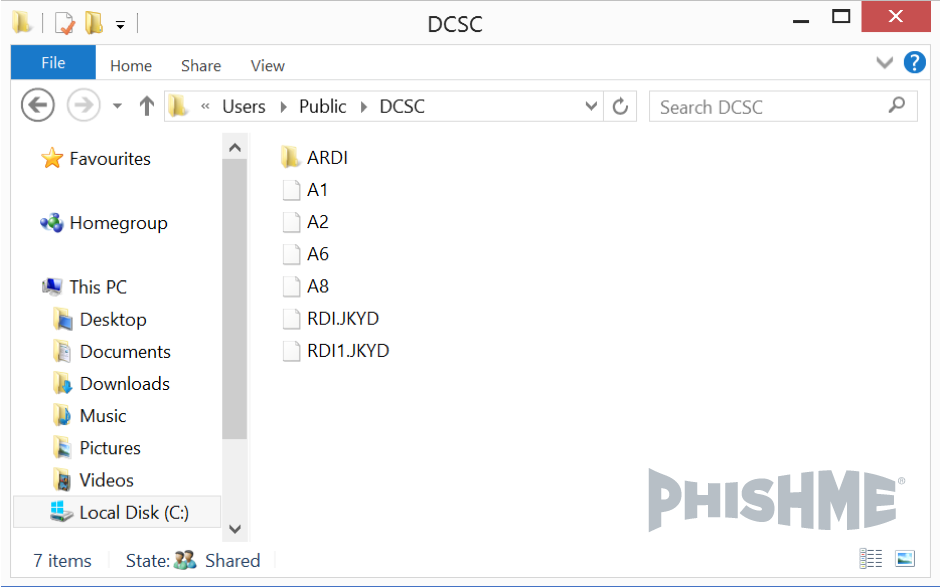
The process concludes with the installation in the system of this latest component, creating the following structure on the user’s PUBLIC folder.
Image 8: Structure of malware files installed on the system
The threat actors have developed a complex system consisting of multiple stages for downloading their malware. The campaign is addressed only to users based in Brazil, not only for the content of the message but also the different checks that their authors have placed in the different phases.
This campaign’s coincidences, like ones we have revealed in the past, underscore that cyber criminals employ different malware families in their different campaigns.
Sign up for free threat alerts from PhishMe Intelligence™ and PhishMe® Research.