CISO SUMMARY
Ancient Babylon defeated its enemies with chariots, horses, and archers. Now Cofense IntelligenceTM has analyzed a phishing campaign delivering the powerful Babylon Remote Administration Tool (RAT). This malware is an open-source tool that can handle many tasks: encrypt command-and-control communication, hide from network security controls, trigger denial of service (DOS) attacks, and last but not least, steal data. Used skillfully, Babylon RAT would make the armies of Hammurabi proud.
Full Details
Cofense Intelligence has analyzed a phishing campaign delivering a multi-feature open source Remote Administration Tool (RAT) named Babylon RAT. Babylon RAT’s Command and Control (C2) communication is encrypted, allows for dynamic domains, and can turn a client into a reverse SOCKS proxy for further obfuscation. This weaponized RAT has many real-time client interaction methods and is capable of information theft. The administration panel has features that can allow for lateral propagation across end points on a network. This tool has enough features that, if used correctly, could devastate any organization.
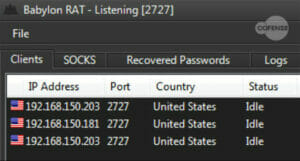
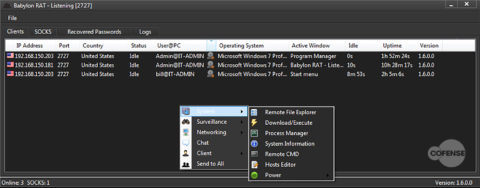
Babylon RAT’s client code is written in C# and is dependent on .NET 4.5. The administration panel (shown in Figure 1) is written in C++, and provides the functionality to manage multiple server configuration options. One option is the port number in which the administration panel will open and listen in when the server is started. Another option is a network key for authentication of the infection to the administration panel. Lastly the configurations allow for the setting of the IP version in which it will connect. The File drop down at the top provides access to the server, configurations, and the payload builder.
Figure 1: The administration panel and the management tabs for Babylon RAT
C2 Details
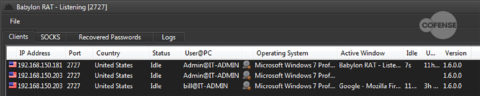
The initial C2 connection the client binary makes after being executed is hardcoded into the binary when it is built. The building process suggests dynamic domains so that the IP address can be changed without interruption to the communication. This connection is encoded and contains fingerprinting information about the infected host. This information includes IP address, Country, Username, PC name, Operating System (OS) details, and which program window is active for the end user. After initial communication with the C2, the infected endpoint will update the administration panel every 5 seconds by default. The check-in notice sent to the server from the client consists of very small network packets, only about 4-8 bytes in size. Figure 2 shows the administration panel with the details listed above.
Figure 2: The administration panel and the fingerprinted information as listed above for Babylon RAT
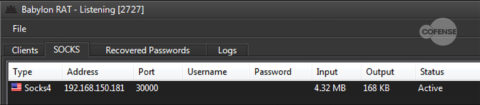
Babylon RAT has the ability to turn an infected machine into a SOCKS proxy, specifying between version 4 or 5. The main difference in the versions: version 5 provides authentication from the client to the proxy, which helps negate abuse from unwanted parties. By creating a SOCKS proxy, the threat actors create an encrypted tunnel and can have all of the infected hosts use it as a gateway, which allows for network capturing. This can also allow for a threat actor to need only one exit point within a network, while maintaining the infection of multiple machines. Meaning, if a threat actor can maintain communication with one endpoint in a network, he can then propagate laterally and have all the traffic from the infected clients’ C2 network flow back out the one endpoint. With access to the command prompt and stolen credentials, this would be trivial to do. This technique would also bypass email and URL filtering of unwanted binaries. Figure 3 shows the SOCKS proxy endpoint details and the amount of traffic flowing through it.
Figure 3: The SOCKS proxy tab and the details associated
The client builder gives the option to use two different C2 domains for redundancy. When combining the ability to use multiple dynamic domains with a proxy server, a threat actor could effectively create layers of obfuscated traffic between the endpoint and the client through multiple channels.
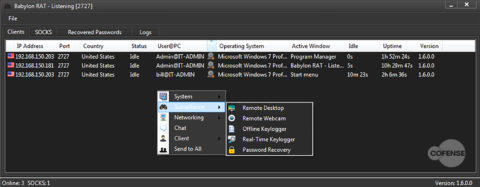
Figure 4: The surveillance options that are available to the operator
Notice in Figure 4 the option for password recovery. The password recovery module looks through applications, including web browsers, and harvests credentials but does not gather the OS user credentials. Although one could surmise that with the username above and a couple of passwords harvested, the OS user credentials could be compromised. If the OS user credentials are compromised, it would be easy for the operator to open the remote command prompt and attempt to log in to other network machines using those credentials. If successful at logging into another machine, it is then possible for the operator to have the second machine download/execute another payload. This would need to be automated, but it does reflect a propagation method for the RAT. Figure 5 shows the system options including the remote command prompt option.
Figure 5: The system options that allow for further interaction and detail of the infected system
Weaponized
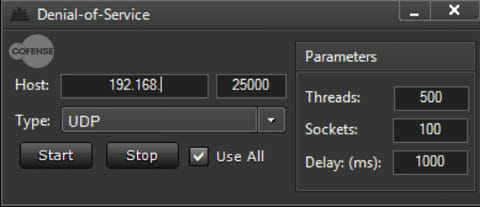
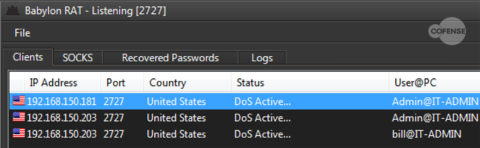
Adding to its already long list of functions, Babylon RAT has the ability to produce Denial of Service (DoS) attacks to targets from the infected hosts. The DoS feature can be set to a hostname or IP range and allows for multiple protocols to be initiated. The protocols all have thread and socket parameters that are adjustable. A threat actor can select to have the attack come from an individual protocol or all of the protocols available. Once this command is sent to a single host, the operator can easily replicate the command to the other infected hosts, effectively creating a larger Distributed Denial of Service (DDoS) attack. Figure 6 shows the configuration for the DoS attack and Figure 7 shows the machines status change to DoS.
Figure 6: The parameters available for the DoS attack
Figure 7: The administration panel and the multiple infected hosts carrying out a DDoS attack
In the End
Babylon RAT is an open-source platform that allows for various misdeeds. The encrypted traffic and the ability to create SOCKS proxies can help negate network security measures. The client builder allows for Anti-Virus bypassing which helps the binary get to the endpoint safely. The processes allowing for network propagation means an infection is not limited to one endpoint. Combined with the ability to perform a DoS attack, Babylon RAT can be highly effective in the proper environment. Babylon RAT campaigns can be avoided with proper technology in place and by educating end users to recognize and report suspicious emails.
To stay ahead of emerging phishing and malware threats, sign up for free Cofense Threat Alerts.
All third-party trademarks referenced by Cofense whether in logo form, name form or product form, or otherwise, remain the property of their respective holders, and use of these trademarks in no way indicates any relationship between Cofense and the holders of the trademarks.