Author: Tonia Dudley
Over the years we’ve seen the evolution of topics and content related to Business Email Compromise, CEO Fraud or whatever you want to label this category of phishing. We like to just call it what it is – conversational phishing – no links or attachments – just trying to get the recipient to interact in a conversation leading to a task. The threat actor is constantly adjusting their lure and context to avoid any AI/ML detection configuration. As of late their tactic is to quickly move the conversation to another communication channel – SMS or WhatsApp for example.
I was recently catching up with a friend and as we wrapping up our conversation, she said “oh speaking of cybersecurity, I had this really strange email yesterday.” I knew exactly where she was going with this conversation and just allowed her to tell me her story. As you read her story, keep in mind that she is a C-Suite executive reporting directly to the CEO, that has only been in her role for a month. It went something like this:
As she was wrapping up her Friday, she did one last check of her email on another platform used by a peer organization. She saw an email from her CEO asking for her cell. At first glance, she knew he was on a personal vacation and maybe he only took his personal cell with him, and he didn’t have my cell phone number. She quickly reached out to her peer, but no response – it was late Friday afternoon – nor did Mark respond when she texted him.
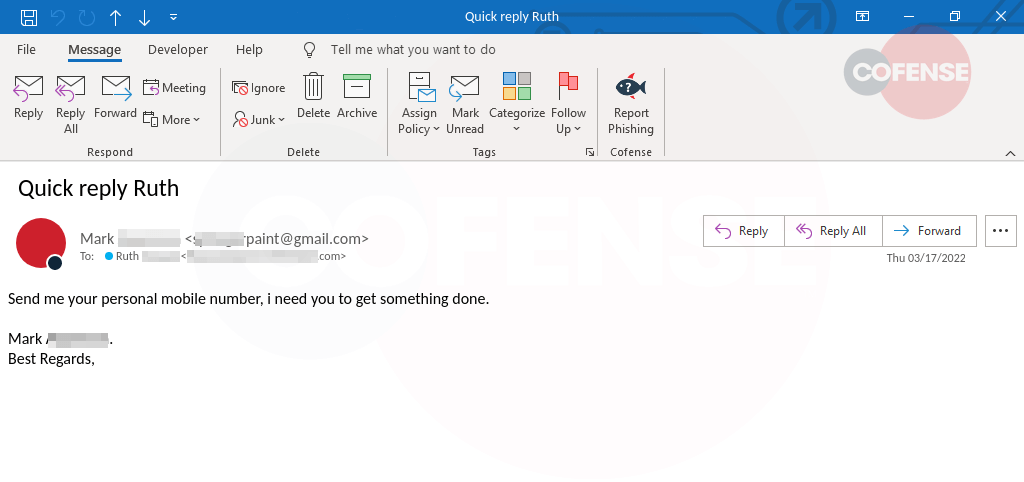
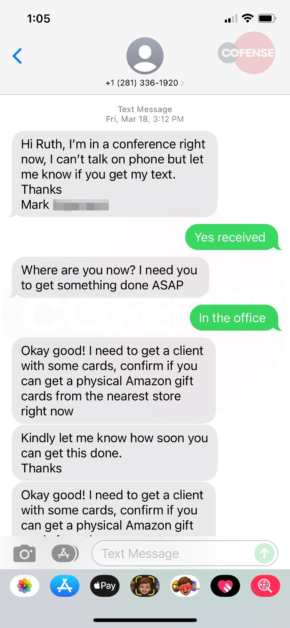
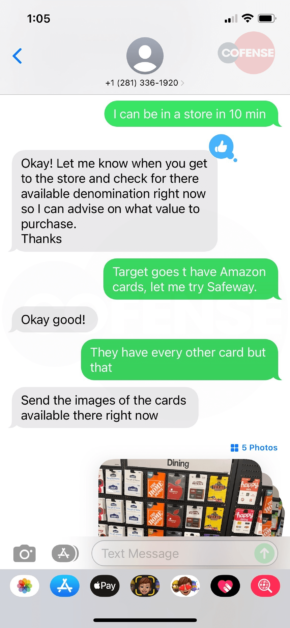
Since she couldn’t get ahold of anyone to validate, she responded and began the text exchange in Figures 2-5. And then headed off to buy the requested gift cards. As you can see in the exchange, it’s clear she thought she was chatting with Mark and making every effort to meet the demands of the request. As she made the final step to text a picture of the code, she decided to do one last check with her CEO. It was then that she decided to try one last time to call him directly. He explained to her that he is on vacation and would never ask her to buy gift cards. While she had scratched off the cover to get the code – in the parking lot after making the purchase – she was able to walk back into the store and get a refund of her personal money.
 |  |
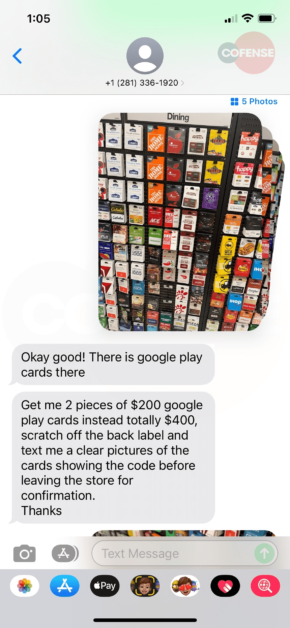 | 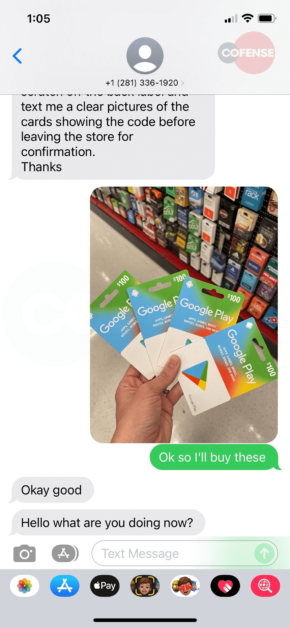 |
Figure 2-5: SMS Message Exchange
In this scenario, Ruth was lucky to be able to get a refund for the purchase she just made, many are not. Because the dollar amount of these losses tend to be low cost, very rarely are these reported to law enforcement.
In our Annual Report webinar series, we break down the various types of tactics seen in these scams and how these have evolved. We also cover some ways that you can protect your organization by making your employees aware of these tactics. On May 25, we will be providing in-depth insights on BEC and best practices on how to educate your employees to prevent situations like the above.



