Cofense was one of the first to report on the risk of COVID-19 themed phishing threats and launched its Coronavirus Infocenter on March 12, 2020. Since that time, we’ve seen no slow down. Every day we see new examples. And while the tactics and schemes may differ, one thing remains consistent: phishing attacks are bypassing secure email gateways, and gateways are not stopping the attacks.
Malicious emails continue to reach user inboxes, increasing the risk of account compromise, data breach, and ransomware attack. Cofense solutions enable organizations to identify, analyze, and quarantine email threats in minutes.
SEE THE PHISHING THREATS THAT ARE SLIPPING BY YOUR EMAIL GATEWAY
FREE FOR 90 DAYS!
Are phishing emails evading your Proofpoint Secure Email Gateway? The following are examples of phishing emails seen by the Cofense Phishing Defense Center (PDC) found in environments protected by Proofpoint – detected by humans, analyzed with Cofense Triage, and quarantined by Cofense Vision.
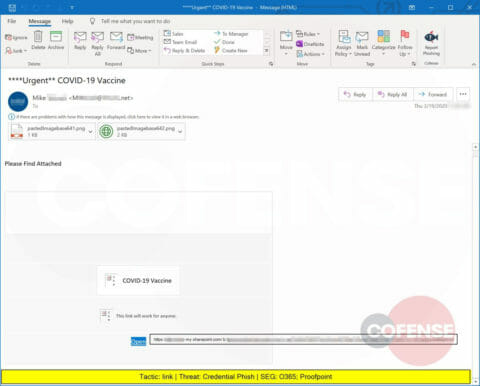
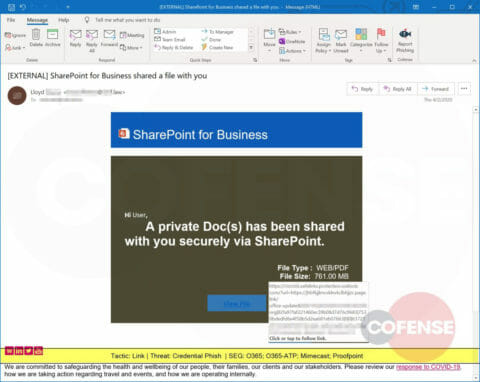
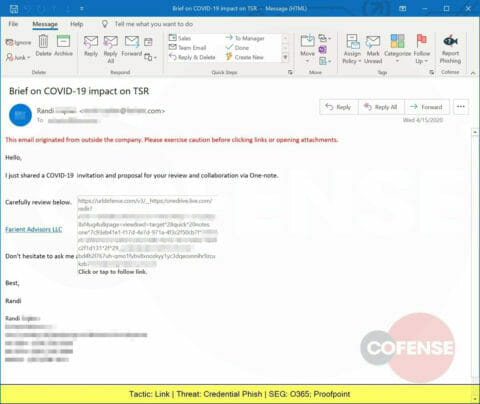
A Credential Phish promising information about a COVID-19 vaccine that includes .png attachments and delivers a URL leading to a sharepoint.com site.
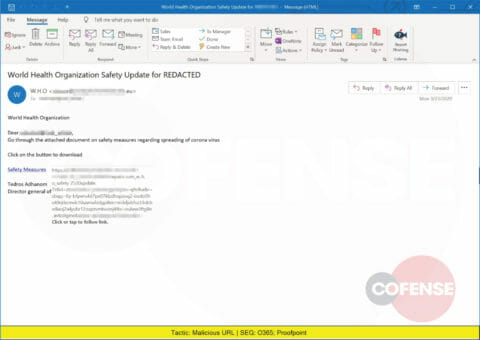
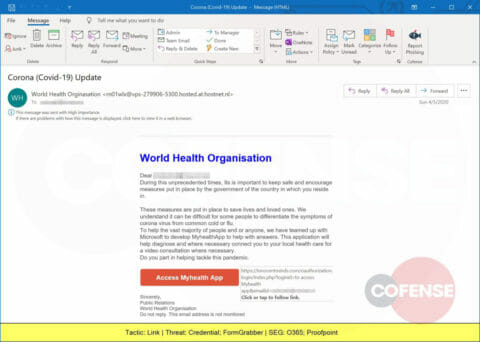
A spoofed email pretending to be from the World Health Organization delivers a malicious URL.
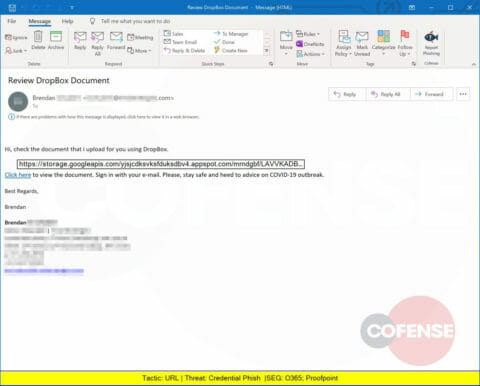
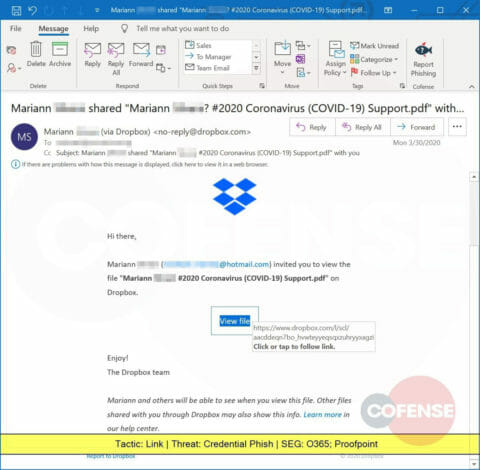
A Credential Phish crafted to look like a Dropbox-hosted document actually leads to storage.googleapis.com. Cofense has seen Dropbox phish since 2014.
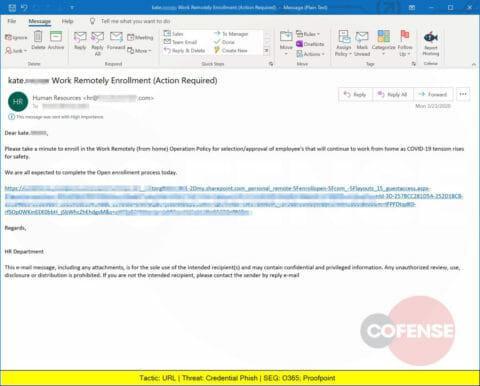
Another Credential Phish that spoofs an organization’s Human Resources department and delivers a link to a login page designed to steal corporate credentials.
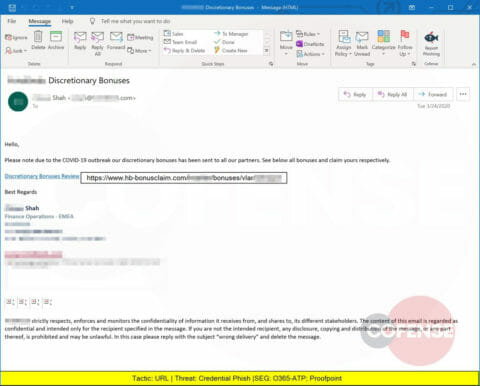
A Credential Phish crafted to look like a corporate communication provides a link to hb-bonusclaim.com and a login page designed to steal corporate credentials.
A Credential Phish with an apparent PDF attachment is actually an image linked to a Microsoft Sway-hosted page and eventually to a page designed to steal corporate credentials. Sway usage in phishing campaigns has been increasing.
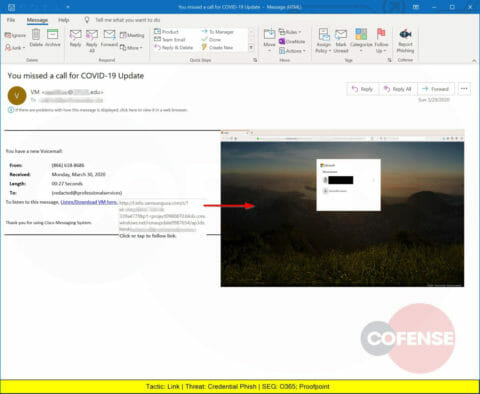
A Credential Phish that appears to be a voice mail with a COVID-19 message but leads to a URL hosted on samsungusa.com.
A Credential Phish containing a link to a Dropbox-hosted resource, supposedly a PDF document, but that leads to a web page designed to steal corporate credentials.
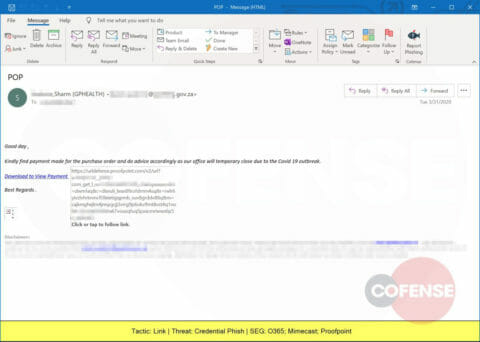
Another Credential Phish requesting payment and prompting for corporate credentials.
A Credential Phish using a Microsoft Word attachment that redirects the victim to a Microsoft OneNote document, eventually leading to a page designed to steal corporate credentials. Read more about the use of OneNote in phishing attacks.
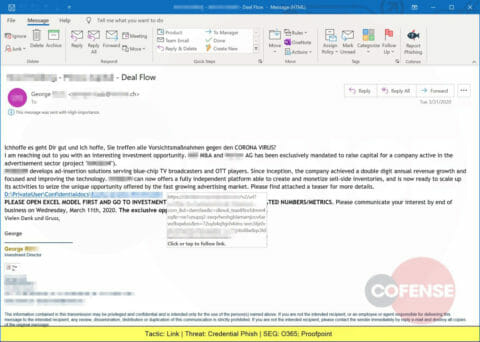
Another Credential Phish, this one offering an investment opportunity but delivering a link that leads to a web page designed to steal corporate credentials.
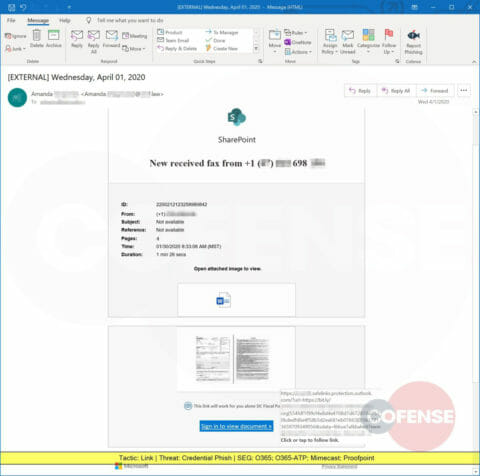
A Credential Phish designed to look like a fax transmission delivers a link leading to a web page designed to steal corporate credentials.
A Credential Phish that spoofs Microsoft SharePoint but leads to a web page designed to steal corporate credentials. Phishing attacks using SharePoint continue to be a problem for all SEGs.
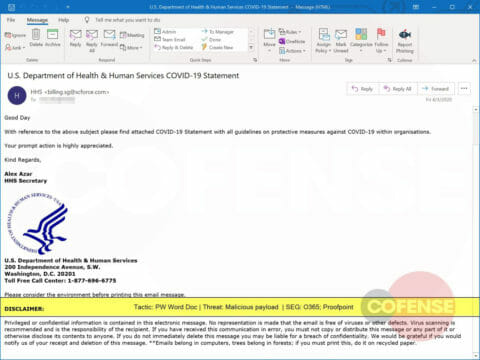
A spoofed email pretending to be the US Department of Health and Human Services delivers a password-protected malicious Microsoft Word document.
A spoofed email pretending to be the World Health Organization provides a link to innocentminds.com that leads to a web page designed to steal corporate credentials.
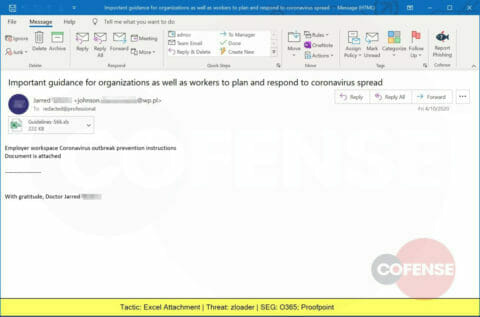
A spoofed email pretending to be a healthcare professional delivers a Microsoft Excel document containing ZLoader, a malicious loader first seen in 2016. Read how Cofense Triage stopped a ZLoader attack.
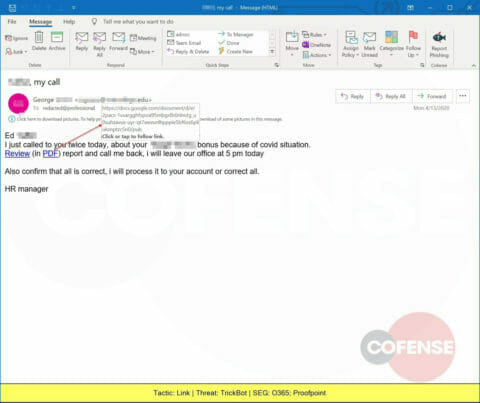
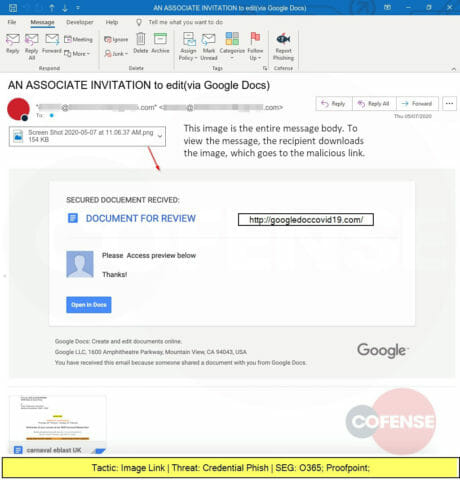
A spoofed email pretending to be Human Resources delivers a link to a Google Docs-hosted page that leads to the installation of TrickBot, a banking trojan developed in 2016 and still seen reaching inboxes.
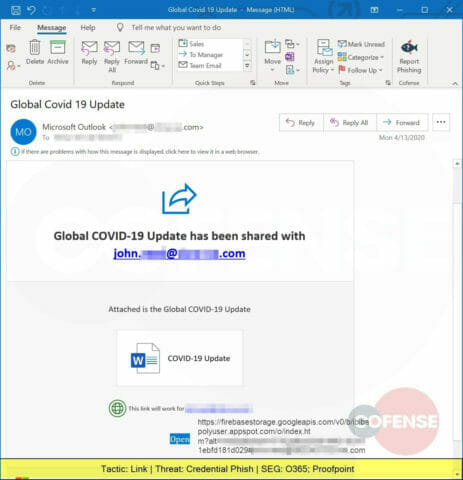
Another phish leveraging Google services (FirebaseStorage), this one is a Credential Phish with a URL that leads the victim to a web page designed to steal corporate credentials. Read more about attacks leveraging Google infrastructure.
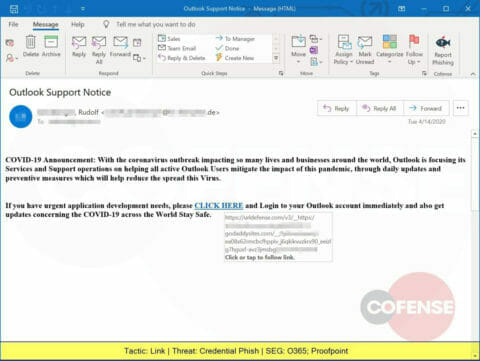
A Credential Phish spoofing Outlook (Microsoft) delivers a link to a godaddysites.com hosted page, leading the victim to a web page designed to steal corporate credentials.
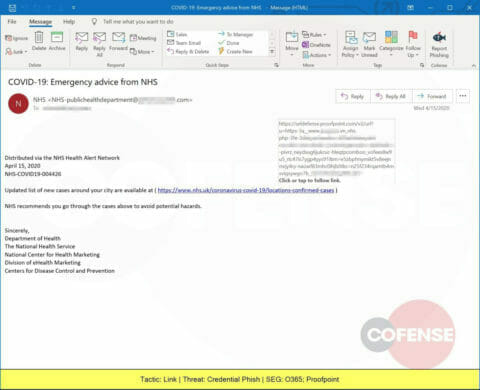
A Credential Phish spoofing the National Health Service promises a document noting confirmed cases of COVID-19, but leads to a web page designed to steal corporate credentials.
A Credential Phish crafted to appear like a corporate communication that leads to a Microsoft OneDrive site. The link leads to a web page designed to steal corporate credentials.
A spoofed email pretending to be a business leader is actually an attempted Business Email Compromise (BEC), seeking to trick the victim into replying.
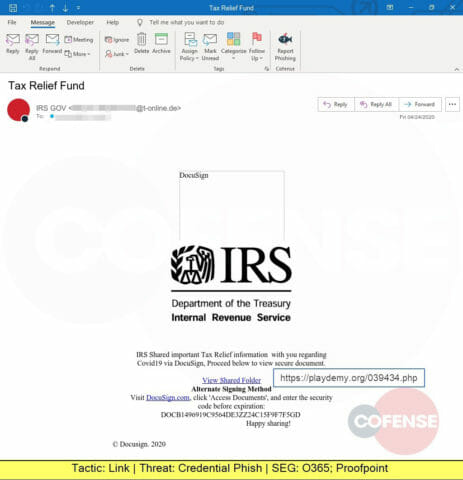
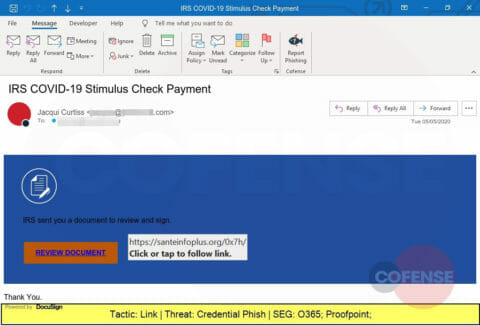
A Credential Phish spoofing the Internal Revenue Service and promising tax relief information hosted in DocuSign. The actual link leads to playdemy.org and leads to a web page designed to steal corporate credentials.
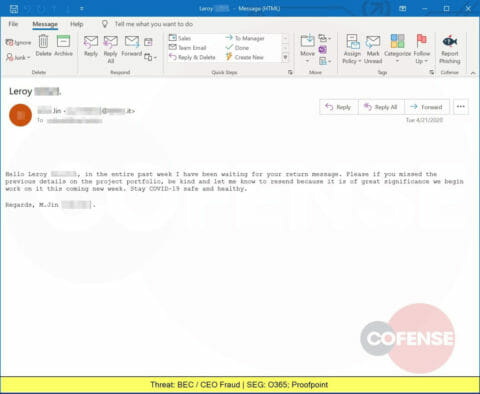
Another spoofed email that is actually an attempted Business Email Compromise (BEC) attack using a COVID-19 theme. BEC attacks have been growing for years and SEGs still aren’t blocking them.
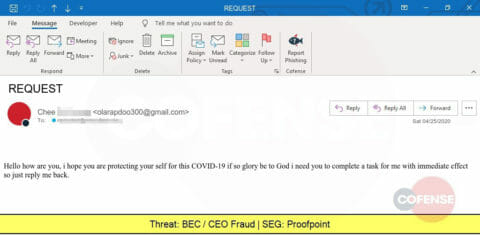
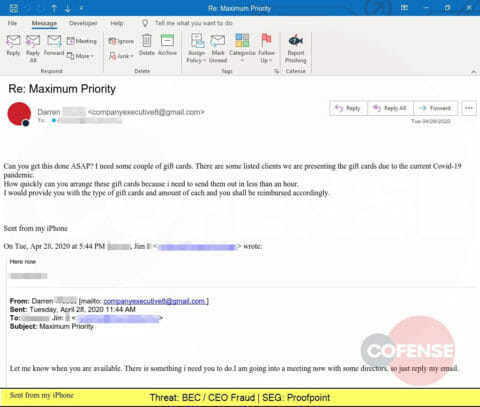
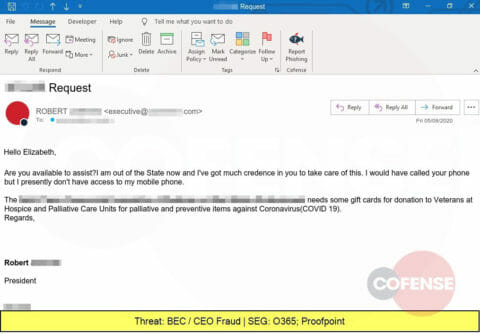
Yet another BEC attempt, this time from a business executive using an email reply strategy and needing gift cards.
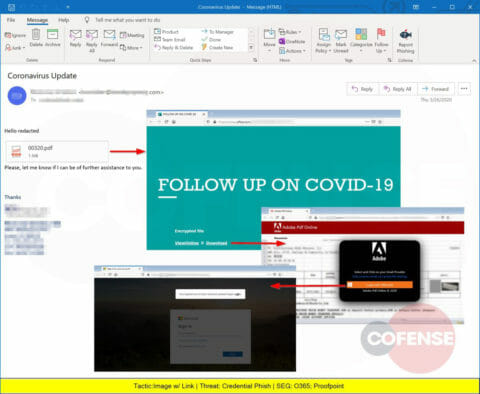
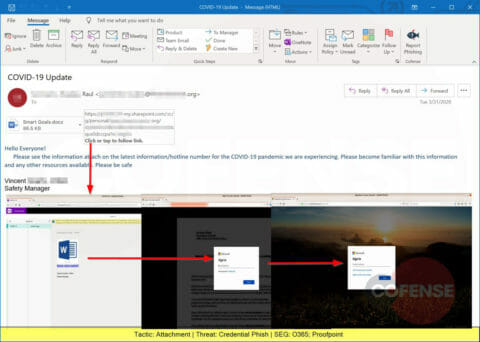
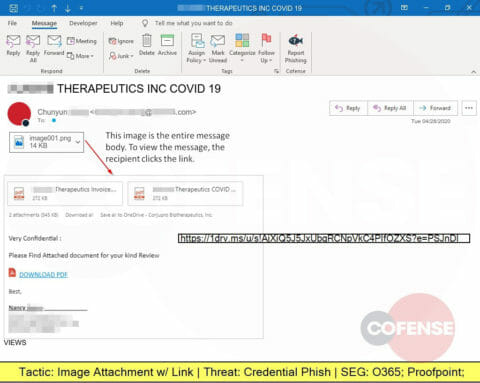
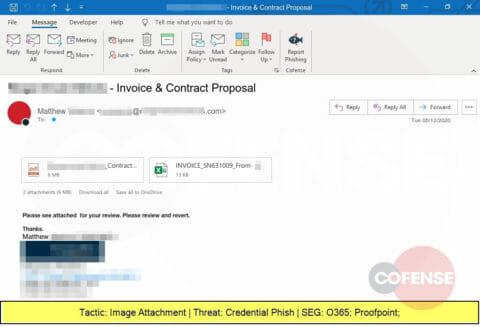
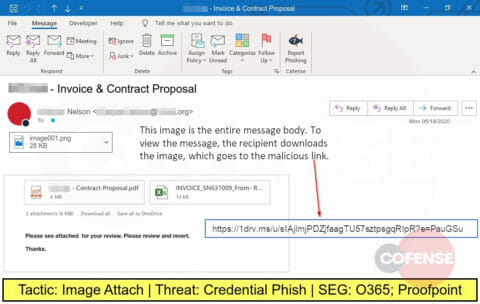
Another COVID-19 themed phishing attack, this one embeds an image that looks like PDF attachments but actually is linked to a website designed to steal corporate credentials.
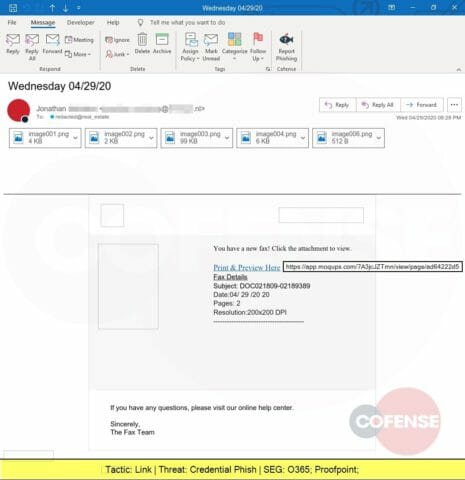
Claiming to be a link to an electronic fax from “The Fax Team”, the embedded link actually leads to a website designed to steal corporate credentials.
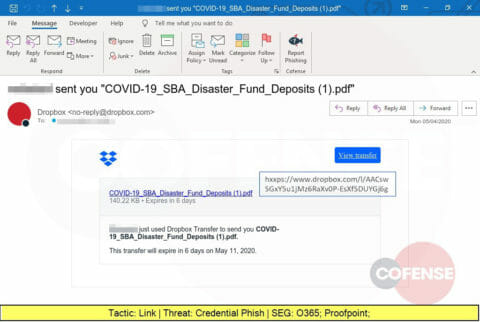
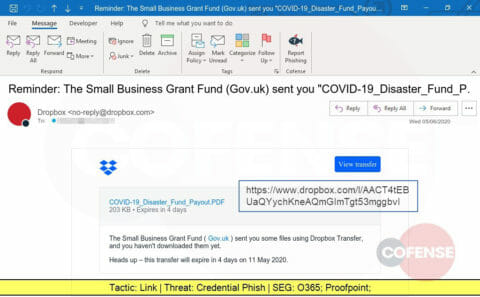
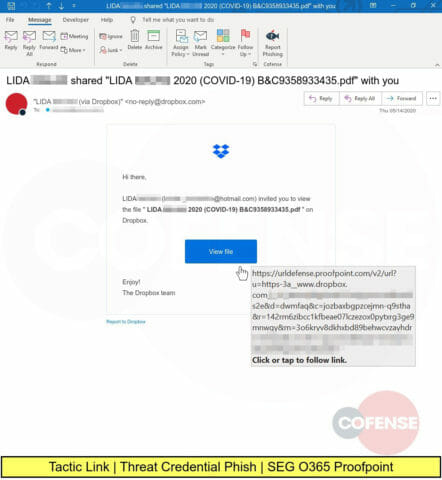
More COVID-19 themed phishing attacks, this one providing a link to a trusted Dropbox source. The victim is led to a website designed to steal corporate credentials.
Spoofing the Internal Revenue Service, this phishing attack delivers an embedded link that leads to a website designed to steal corporate credentials. Read more in the Cofense Blog.
Another phishing attack using a Dropbox link to lead the victim to a website designed to steal corporate credentials.
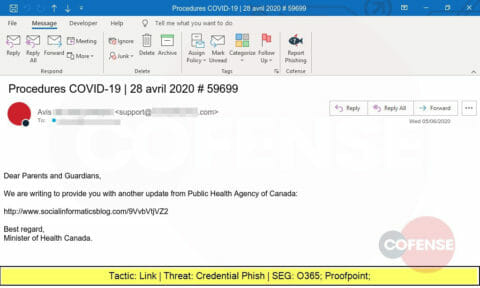
This phishing attack spoofs the Public Health Agency of Canada and delivers a link that will lead the victim to a website designed to steal credentials.
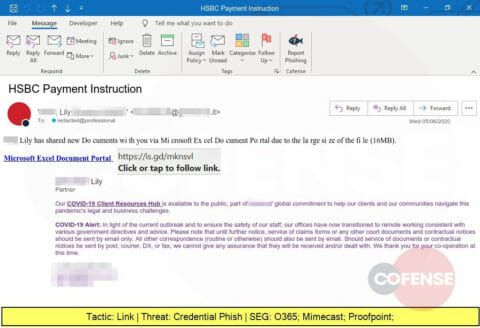
Spoofing a well-known bank, this phishing attack purports to have a large file needing to be downloaded from a Microsoft Excel Document Portal but will lead the victim to a website designed to steal credentials.
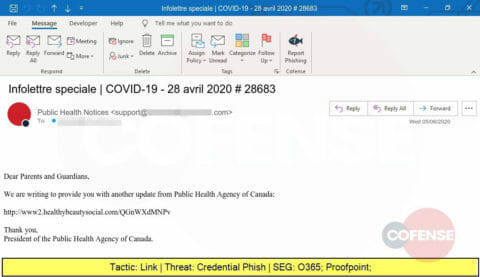
Another spoof of the Public Health Agency of Canada, this one also delivers a link that leads to a website designed to steal credentials.
This phishing attack embeds an image that looks like email content. Clicking it leads the victim to a website designed to steal credentials.
Combining a COVID-19 theme with an emergency request by an executive, this Business Email Compromise attempts to lure the victim into purchasing gift cards.
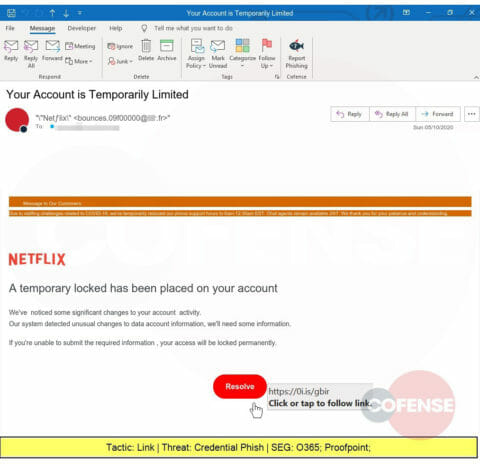
Looking to capture Netflix credentials, this phish may take advantage of people’s propensity for password re-use, putting corporate credentials at risk. Netflix spoofs aren’t just for consumers anymore.
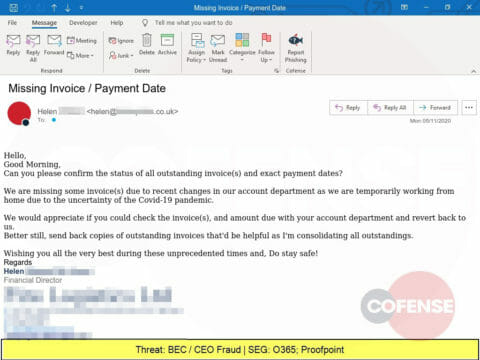
Another BEC, this one pretending to be the financial director, tricks the victim into sending the attacker outstanding invoices, which can be used in attacks against 3rd parties.
Another embedded image designed to look like attachments but actually lead to a credential-stealing website.
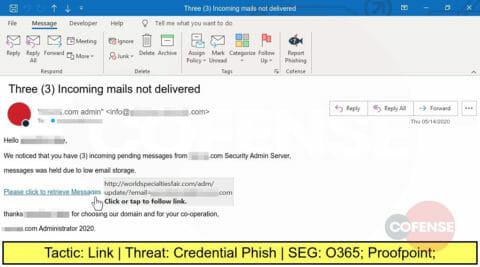
With some organizations offering a spam filtering service to their employees, phishing threat actors are taking advantage to mask their attacks as pending deliveries. This link, however, leads to a website crafted to steal credentials.
Cloud sharing platforms like Dropbox are often trusted by organizations and employees alike. This phishing attacks exploits that trust to direct the recipient to a malicious website designed to steal credentials.
Another phishing email that embeds an image designed to look like an attachment. Clicking the image takes the victim to a website designed to steal credentials.
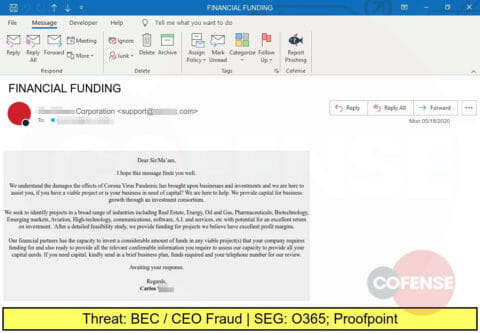
This spoof of a financial “partner” is actually a Business Email Compromise attempt seeking to lure the victim into a financial transaction.
The problem of malicious emails evading secure email gateways is not going away. No perimeter control can keep up with the velocity of shifting techniques used by attackers. That’s why a well-conditioned workforce and a security operations team equipped with the tools needed to rapidly detect and quarantine threats is imperative.
Want to discover more about the phishing attacks your SEG is missing? Sign up for 3 free months of Cofense Intelligence, the best human-vetted phishing intelligence in the world.
SIGN UP