The CofenseTM Phishing Defense CenterTM analyzes suspicious emails reported by customers’ users and alerts their security teams when they need to take action. Because we live and breathe phishing analysis and response, and because we operate 24/7/365, we have visibility into threats most teams can’t see.
Here’s a Real Example Involving Compromised Email Accounts
A few months back, an organization exploring our services did a proof-of-concept trial, during which we analyzed emails its users found suspicious and reported for inspection. Soon enough, we saw emails sent from compromised email accounts within the organization.
In fact, they utilized a technique known as the Zombie Phish, so called because it revives a dormant email conversation the user had had to disarm the user and lure him into clicking. We provided the indicators of compromise to the customer’s point of contact, plus included a link to a Cofense blog about the Zombie Phish.
We Found Over 2000 Malicious Emails—in Just 3 Days
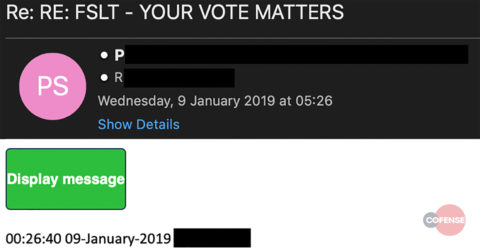
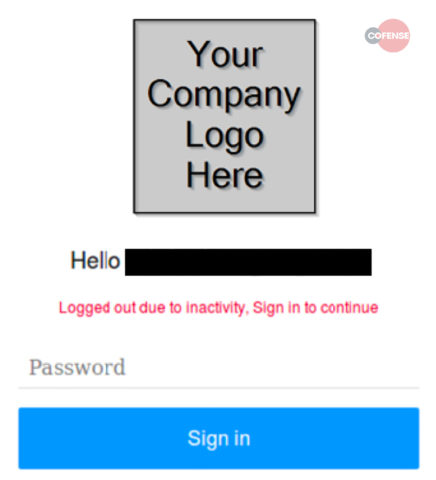
A couple of weeks passed uneventfully. Then, we saw a new batch of reported emails from compromised accounts, followed the next day by a spike in similar messages. In a 3-day period, we found 2053 malicious emails sent through 77 internal accounts. Subject lines varied, but every one of these emails contained a link to “Display Message,” which redirected to a login page spoofing the customer’s actual page. It asked users to enter the password for their company account.
The techniques in these emails seemed to be part of a global phishing campaign targeting UK organizations. The target’s email address was encoded in the link. When someone clicked, the login page displayed the organization’s logo. The links’ behavior varied, sometimes redirecting to a fake site instead of the spoofed login page, other times displaying a message that the URL was unavailable.
The team in the Cofense Phishing Defense Center was glad to be of assistance. Learn more about our phishing defense services.
All third-party trademarks referenced by Cofense whether in logo form, name form or product form, or otherwise, remain the property of their respective holders, and use of these trademarks in no way indicates any relationship between Cofense and the holders of the trademarks.