You’ve read it on this blog before. It’s not enough to simulate phishing emails and raise employees’ awareness. At the end of the day, you need to be able to stop real attacks. One key: basing simulations on phishing threats you actually see in your organization.
Following is a real example of one CofenseTM customer that took these words to heart. This company is global. It operates in an extremely data-rich industry that stores Social Security numbers, email addresses, credit card information, and more. In other words, they have a lot to protect.
First, the company leveraged information from a real credential phishing attack.
This company trains its employees to recognize and report phishing. The team responsible for the anti-phishing program took advantage of a monthly report from the Cofense Phishing Defense Center (PDC), which analyzes and escalates user-reported emails to alert customers immediately to verified phishing threats.
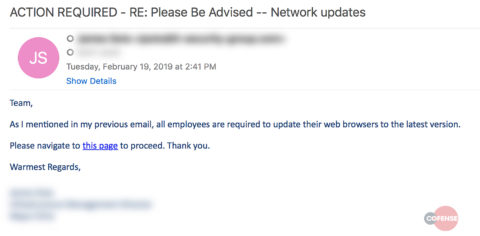
The monthly report described a phishing email, one seen in a different industry, that asked users to perform an urgent network upgrade. “Action required”—just click a link. Upon clicking, users would be taken to a site where they would enter their network credentials.
The Cofense PDC sees hundreds of thousands of similar emails targeting customers each year. Here’s a sample:
Next, they simulated the attack to educate employees.
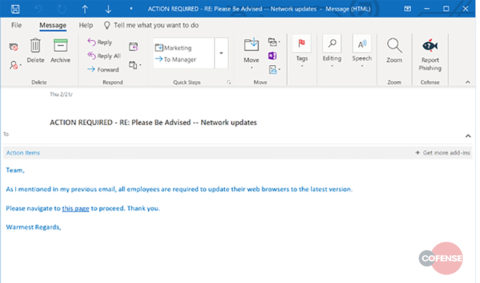
Credential phishing is an epidemic. To help their employees spot a credential phishing attack, the company decided to use this real attack to craft a simulation. Here’s what the simulated email looked like:
As you can see, the simulated phishing email used a header very similar to the email seen in the wild.
Armed with other details from the real phish, including the full body of the message, the company sent this simulation to high-value targets—employees with elevated credentials, the “keys to the kingdom.” It’s smart to focus on these employees, just like attackers do.
The results were encouraging. The ratio of employees reporting the simulated phish versus those that fell susceptible was greater than 1:1. It was a good start. With continued simulations, the rate should increase and show better resiliency to credential phishing.
To repeat, it’s good to condition employees to report phishing emails. It’s even better to have them practice against the real deal, so they can help stop it before real damage is done.
To learn more about the growth of credential phishing, view the Cofense State of Phishing Defense 2018 report.
All third-party trademarks referenced by Cofense whether in logo form, name form or product form, or otherwise, remain the property of their respective holders, and use of these trademarks in no way indicates any relationship between Cofense and the holders of the trademarks.