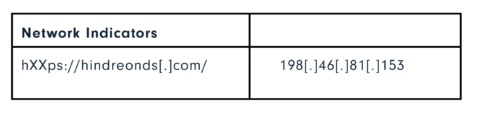By Milo Salvia, Cofense Phishing Defense CenterTM
The Cofense Phishing Defense Center (PDC) has observed a phishing campaign that aims to harvest credentials from Stripe, the online payment facilitator handling billions of dollars annually, making it an attractive target for threat actors seeking to use compromised accounts to gain access to payment card information and defraud consumers. The phish prevents email recipients from seeing the destination of an embedded link when they try to hover over the URL. Instead, what they see is a bogus account message. Here’s how the campaign works.
Email Body
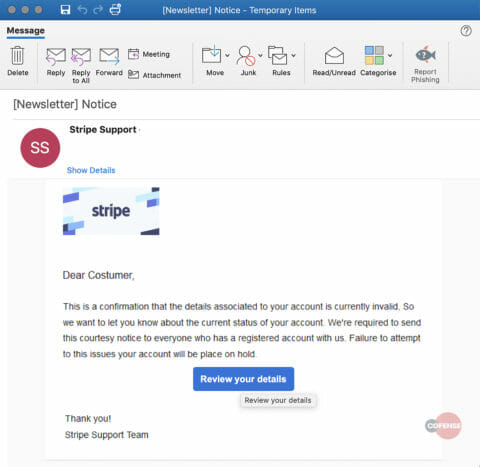
The email pretends to be a notification from “Stripe Support,” informing the account administrator that “Details associated with account are invalid.” The administrator needs to take immediate action, otherwise the account will be placed on hold. This is cause for panic among businesses that rely solely on online transactions and payments. Fear and urgency are the most common emotions threat actors play on, spurring otherwise rational people to make irrational decisions.
Figure 1: Email Body
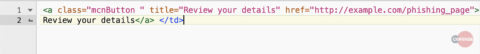
The email body contains a button with an embedded hyperlink, as seen above: “Review your details.” When clicked, the recipient is redirected to a phishing page. Usually one can check the destination of the hyperlink by hovering over it with the mouse curser. The true destination of this hyperlink is obscured by adding a simple title to HTML’s <a> tag, which shows the recipient the title “Review your details” when the recipient hovers over the button instead of the URL. Potentially this is a tactic to mask the true destination from a vigilant recipient.
Figure 2: Malicious Button
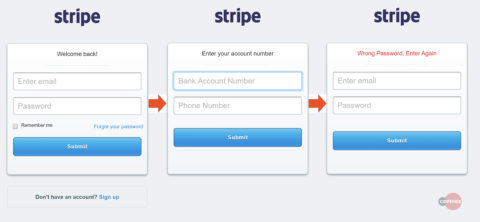
The phishing page is an imitation of the Stripe customer login page. In fact, it consists of three separate pages. The first one aims to harvest the admin’s email address and password, while the second page asks for the bank account number and phone number associated with the account. Lastly, the recipient is redirected back to the account login page which displays an error massager, “Wrong Password, Enter Again.” This leads the recipient to believe an incorrect password has been entered and redirects back to the legitimate site, so the recipient doesn’t suspect foul play.
Figure 3: Phishing Pages
IOCs:
Cofense ResourcesHOW COFENSE CAN HELP
Cofense PhishMeTM offers a simulation template, “Stripe Account Notification,” to educate users on the campaign described in today’s blog.
75% of threats reported to the Cofense Phishing Defense CenterTM are credential phish. Protect the keys to your kingdom—condition end users to be resilient to credential harvesting attacks with Cofense PhishMe.
Over 91% of credential harvesting attacks bypassed secure email gateways. Remove the blind spot—get visibility of attacks with Cofense ReporterTM.
Quickly turn user-reported emails into actionable intelligence with Cofense TriageTM. Reduce exposure time by rapidly quarantining threats with Cofense VisionTM.
Attackers do their research. Every SaaS platform you use is an opportunity for attackers to exploit it. Understand what SaaS applications are configured for your domains—do YOUR research with Cofense CloudSeekerTM.
Thanks to our unique perspective, no one knows more about the REAL phishing threats than Cofense. To understand them better, read the 2019 Phishing Threat & Malware Review.
All third-party trademarks referenced by Cofense whether in logo form, name form or product form, or otherwise, remain the property of their respective holders, and use of these trademarks in no way indicates any relationship between Cofense and the holders of the trademarks. Any observations contained in this blog regarding circumvention of end point protections are based on observations at a point in time based on a specific set of system configurations. Subsequent updates or different configurations may be effective at stopping these or similar threats.