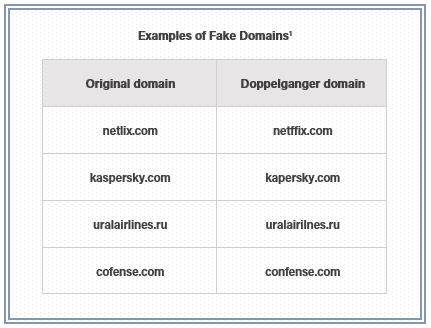
Does your company have an evil twin on the web? Threat actors may be leveraging a lookalike version of your company’s name to deliver malware through phishing that plays off your brand. Say the company name is Cofense, with the internet domain name cofense[.]com. What would happen if someone registered a copycat domain name using, for example, Confense, with the domain confense[.]com? Wouldn’t the search engine just route users to the real deal, or wouldn’t it be obvious quickly that the name was misspelled?
Cofense, Confense. Big deal, right? Wrong. Here’s why.
Every day, attackers are busy registering lookalike, or doppelganger, domains that mimic reputable brands to lure users through phishing emails, malware delivery and more. The domains are designed to trick users into believing they’re engaging with a bona fide enterprise. The associated costs are minor for threat actors. Not so your business, which can face astronomical losses, beyond the purely financial, to include critical brand compromise and data theft.
How do they do it?
One way criminals get around domain-registration norms and standards is to use characters that look like those in the English language. An example often cited is trading English-alphabet characters or letters for those in another alphabet, such as Cyrillic. In this case, the letter “a” looks almost the same in English as Cyrillic.
Once the domain is registered, it can be used to create a website designed to closely resemble that of the legitimate company. It’s not a pricey or difficult endeavor. Match the copycat website with doppelganger email, and you have a solid starting point for scamming countless unsuspecting consumers.
Why do they do it?
Sometimes the sites are designed to pick off a portion of an established brand’s audience and sales. Other times, those registering lookalike domains seek to sell the domain to the copied brand’s owners, an exchange that can prove very profitable for the imitators. The real enterprise’s owners will often pay handsomely to safeguard brand integrity and reputation.
Far too often, however, the objective is phishing. Users, believing the site is authentic, will click on a link, enter their credentials on a fake website, and lose control of online accounts to thieves. They may also unleash malware in the form of viruses, keyloggers, worms, trojans, ransomware, botnets, spyware or rootkits.
Doppelganger domains can be particularly effective for BEC, or business email compromise, campaigns. An unsuspecting recipient who has regular business with, for example, Cofense, may receive an email from confense[.]com, rather than cofense[.]com. The email may contain a link to a “special offer.” When the link is clicked, malware may be launched or a phishing landing page may open that requires authentication – user name and password. Once the information is entered, the threat actor has a far easier path to successfully carry out a wide range of crimes, from account takeover to financial theft.
What can you do about doppelganger domains?
You can decrease the likelihood of becoming a victim by preemptively registering variations of your domain name. Github can be a useful resource for identifying variations you should register. If you’ve discovered that a lookalike has already been registered, you may have to take legal action against the owner. Your efforts are more likely to succeed if you hold a trademark and can make a case for infringement or damage to your mark’s value.
If the lookalike domain is being used for criminal activity such as phishing, report the domain to services such as Google Safe Browsing or Netcraft. This may result in the domain’s delisting in search engines, or being pulled offline.²
At the end of the day, doppelganger domains – and those who register them – should be taken seriously. They can ruin your reputation, your profitability and your credibility. When you know what’s at stake, you can better protect your brand.
We’re the leading provider of phishing detection and response solutions designed for enterprise organizations. The Cofense Phishing Detection and Response (PDR) platform draws upon our global network of more than 27 million people actively reporting suspected phish, combining that with advanced automation to stop phishing attacks faster and stay ahead of breaches. While we can’t wipe out the doppelgangers, we can help you stay safe from phishing exploits. We’re here to help. Contact us at any time to find out what we can do for your business.


