Google Workspace (formerly G Suite) By Dylan Main, Cofense Phishing Defense Center
With widespread financial uncertainty and talks of further stimulus funding in the news, many are desperate for some form of monetary relief. Threat actors have begun taking advantage of this desperation by creating campaigns tailored to these uncertain times. The Phishing Defense Center (PDC) has discovered a phishing attack that attempts to obtain personal information by exploiting hopes for economic relief.
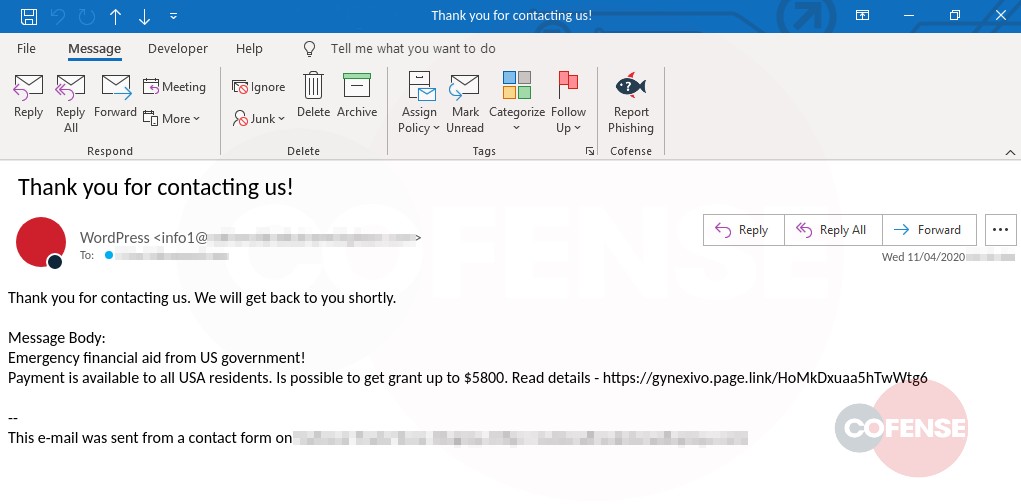
Figure 1: Email Body
The email itself presents itself as a reply to a filled-out contact form and attempts to get the recipient’s attention through a tone of familiarity. By beginning with “Thank you for contacting us,” the threat actor has made it appear as though the recipient had previously expressed interest in a third party by filling out the form with their email address. The message body then lures the victim with a link to details of an emergency grant of $5,800 available from the U.S. government. By appealing to the current fiscal concerns of many Americans, the threat actor wants to entice the target into clicking the “Read details” link.
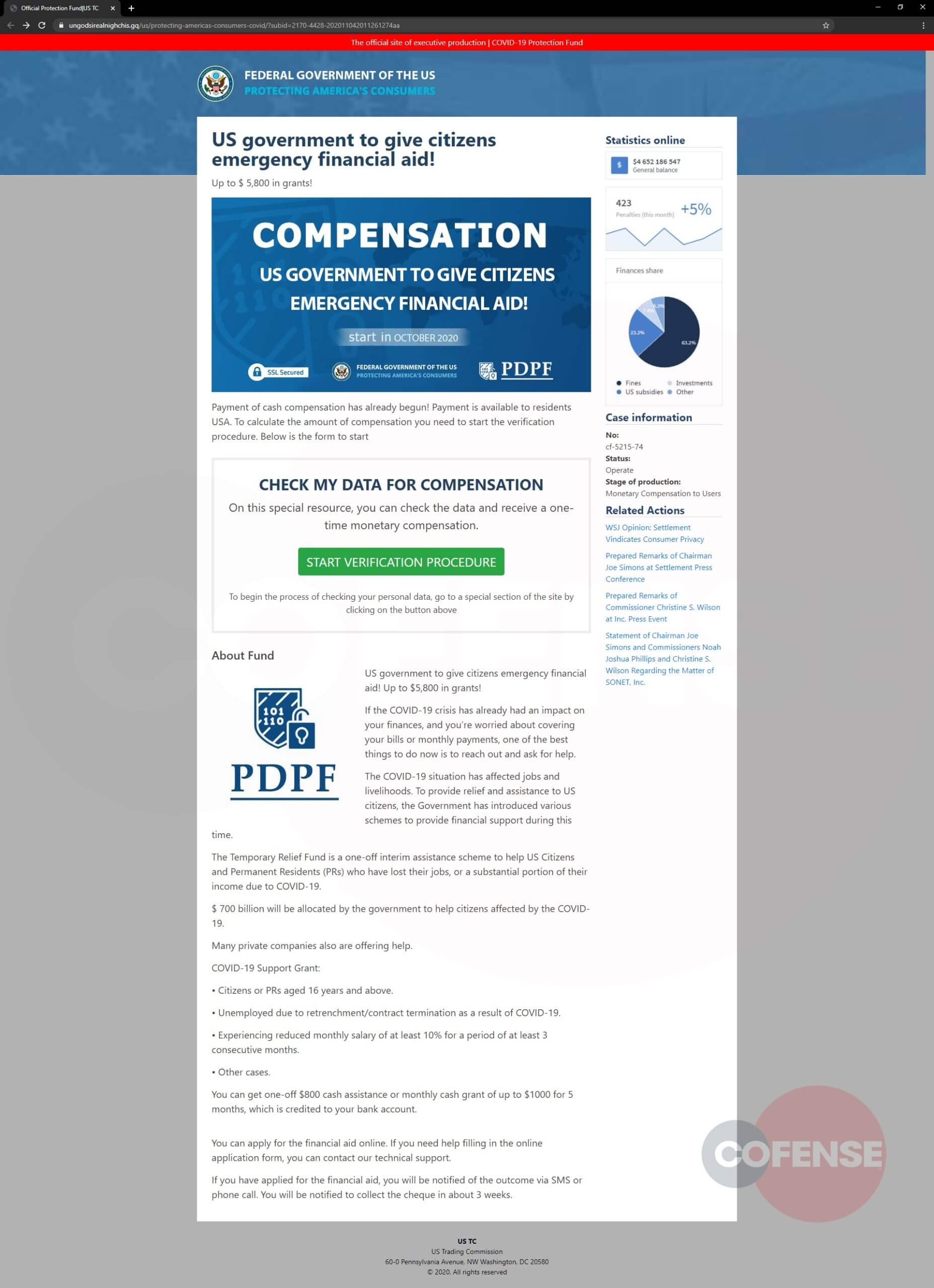
Figure 2: Landing Page of Phish
Clicking the link redirects to a detailed page that appears to be a legitimate federal government website (Figure 2). Unlike many campaigns, this one goes a step further in terms of attention to detail to make it look like a real government page. The threat actor has added several items to advance its validity, including financial statistics and a detailed outline of this “Emergency Financial Aid.” The page also has a button that allows the person interacting with it an option to verify their data to collect funds.
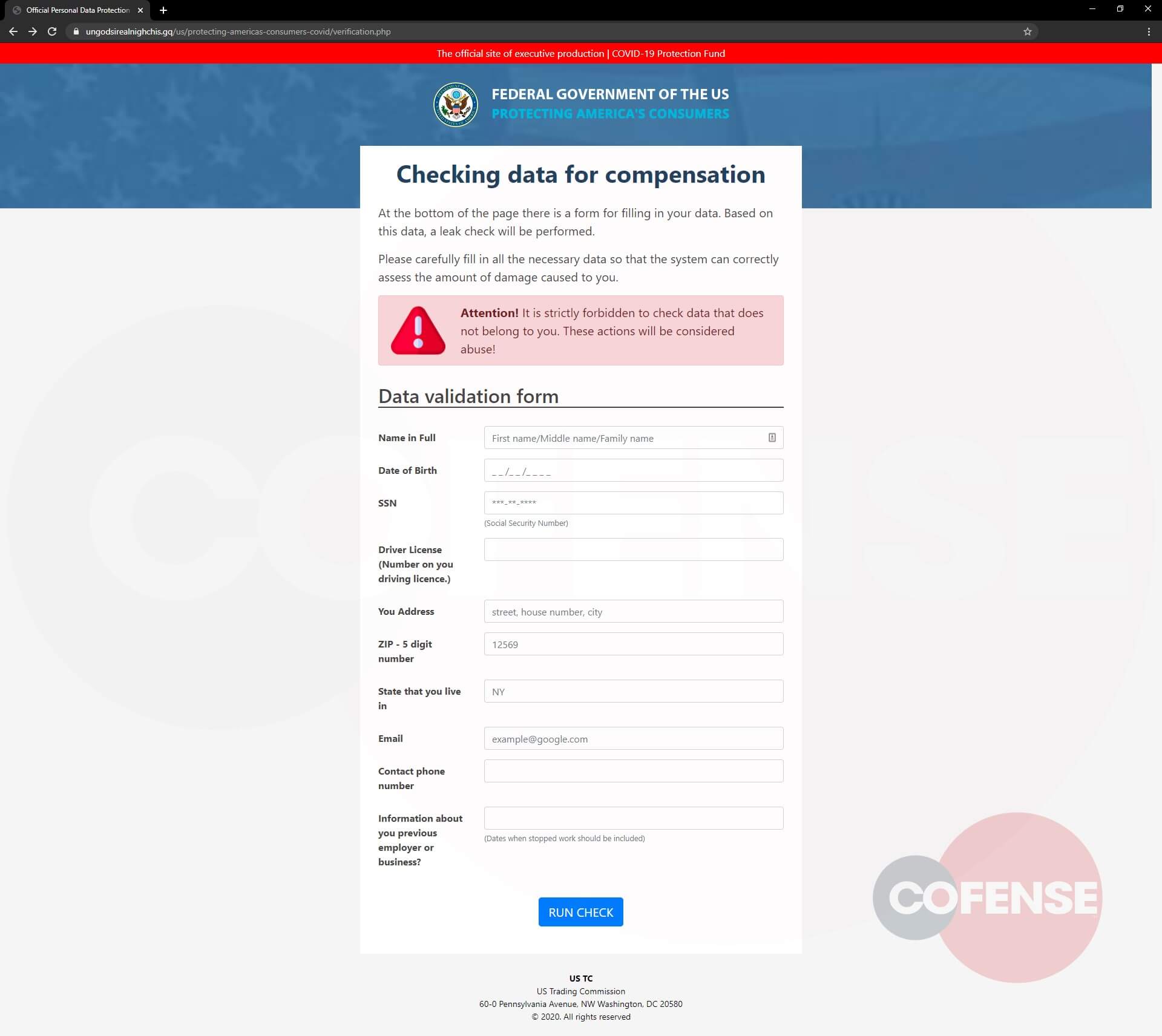
Figure 3: Second Step of Phish
Clicking the button takes the viewer to the actual phishing page, seen above in Figure 3. Much like the other page, it is detailed and is unlike generic phishing pages. This page asks the user to check compensation eligibility by providing their Social Security Number, address, date of birth and other personally identifiable information (PII). Another detail to note is the form gives a warning that checking another person’s data is strictly prohibited, adding to the seeming authority. By entering data into the requested fields and clicking the “Run Check” button, all of this private information is then sent to the threat actor.
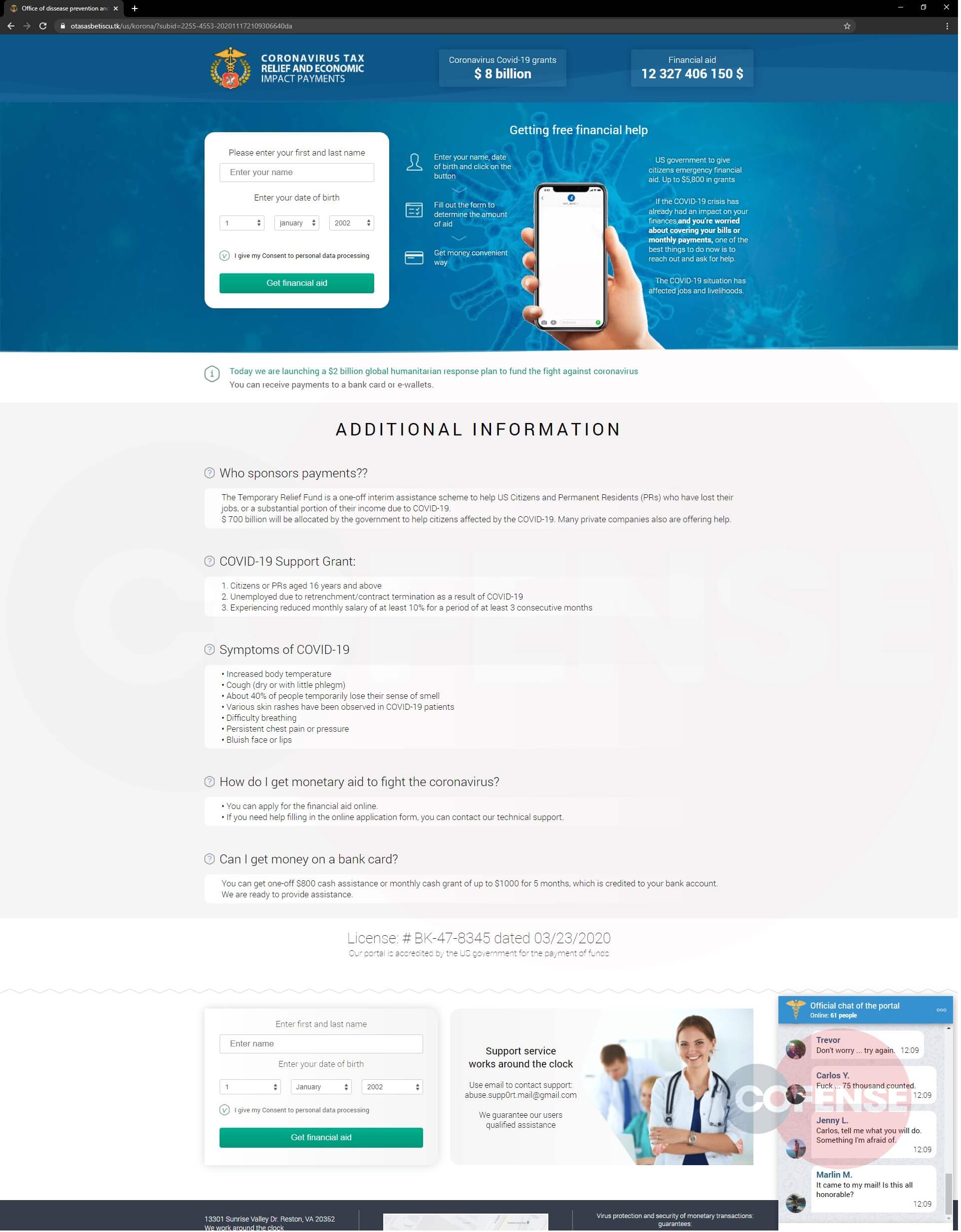
Figure 4: Phishing Page
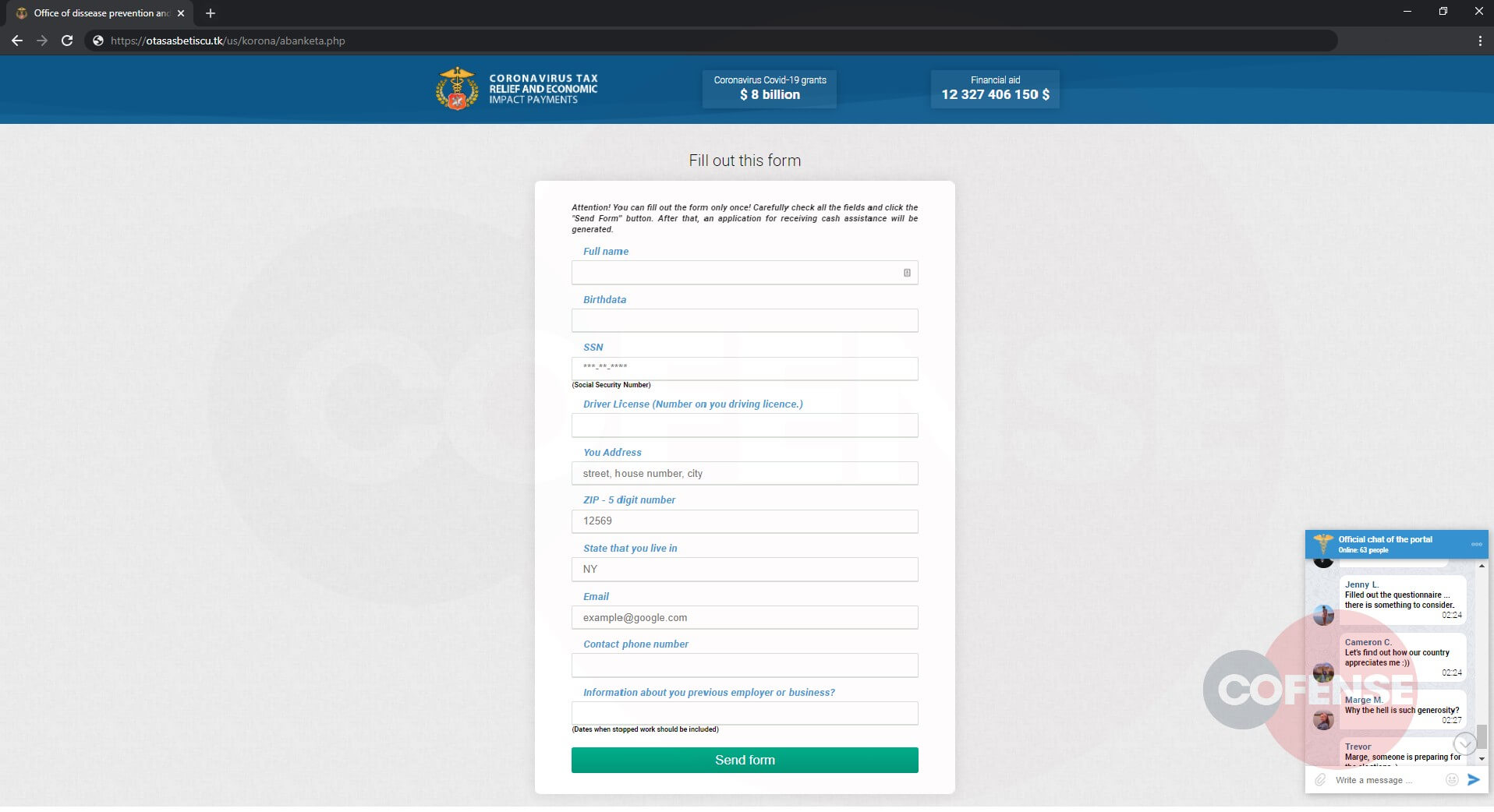
The Cofense Phishing Defense Center has also identified a new phishing page that redirects from the same infection URL (Figure 4). This page is similar to the original phish; however, it uses the allure of tax relief for the current coronavirus pandemic to lure people into giving their personal information.
Figure 5: Phishing Page
As you can see above, Figure 5 resembles Figure 3 in that it collects PII. However, on this page, a chat window at the bottom right appears to simulate actual conversations between other users apparently excited about the potential tax relief. This is an interesting tactic and adds to the illusion of authenticity.
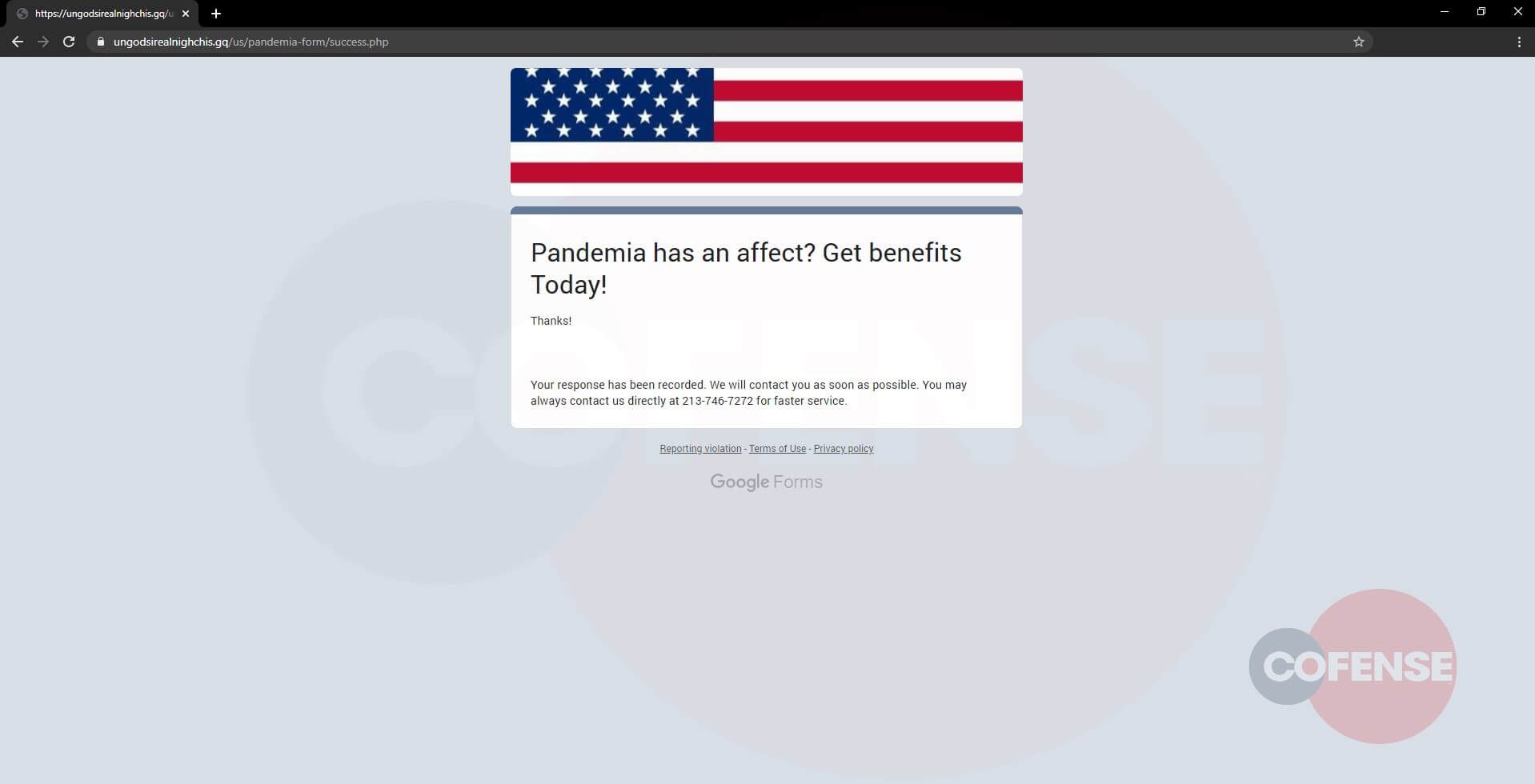
Figure 6: Final Confirmation Page
After data is entered into either of the two phishing pages, it redirects to a confirmation page thanking the victim for providing their information and promising them a prompt reply. This is just the last of many tricks the threat actor uses to trick the victim into believing that this application is legitimate. It shows that they will attempt to take advantage of any, and all, situations to gain confidential information.
Indicators of Compromise
| hXXps://gynexivo[.]page[.]link/HoMkDxuaa5hTwWtg6 | 172[.]217[.]15[.]110 |
| hXXp://ungodsirealnighchis[.]gq/us/protecting-americas-consumers-covid/ | 104[.]24[.]101[.]186 |
| hXXps://otasasbetiscu[.]tk/us/korona | 172[.]67[.]168[.]232 |