By Max Gannon
Emotet has consistently employed financial themes in its phishing emails, and attackers have previously exploited the arrival of the U.S. tax season to construct emails targeting users who need to file tax returns. The 2022 tax season is no different. As early as March 14, 2022, Emotet operators returned to their old tax-season hunting grounds with some new tricks, as Cofense Intelligence™ observed phishing emails using W-9 tax form lures to deliver Emotet payloads.
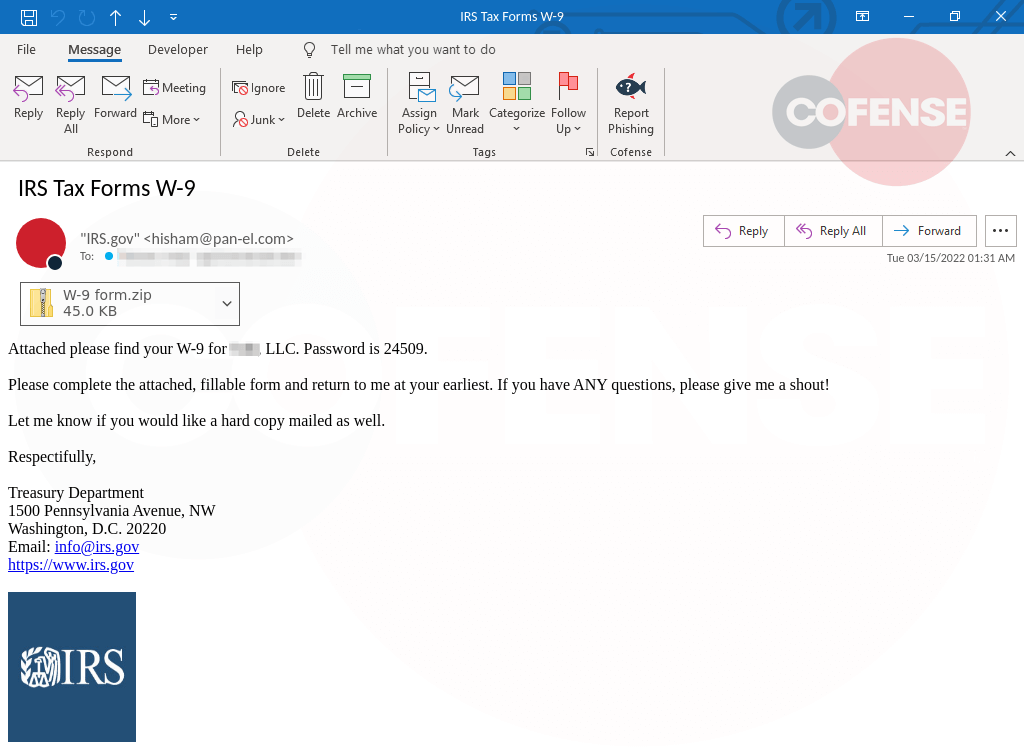
In past years, Cofense Intelligence has reported on Emotet taking advantage of tax season to deliver W-9 themed malicious documents but, this year, the tactic has been improved. Emotet operators have upped their game in this most recent campaign, now including the Internal Revenue Service (IRS) logo, a specific mention of the organization employing individual recipients, and a password with which to extract the attached password-protected archives. When the Office-macro-laden spreadsheets enclosed in the password-protected archives are opened, they request that macros be enabled. If macros are enabled, Emotet .dll files are delivered to the victim’s computer.
Figure 1: IRS-spoofing email delivering Emotet
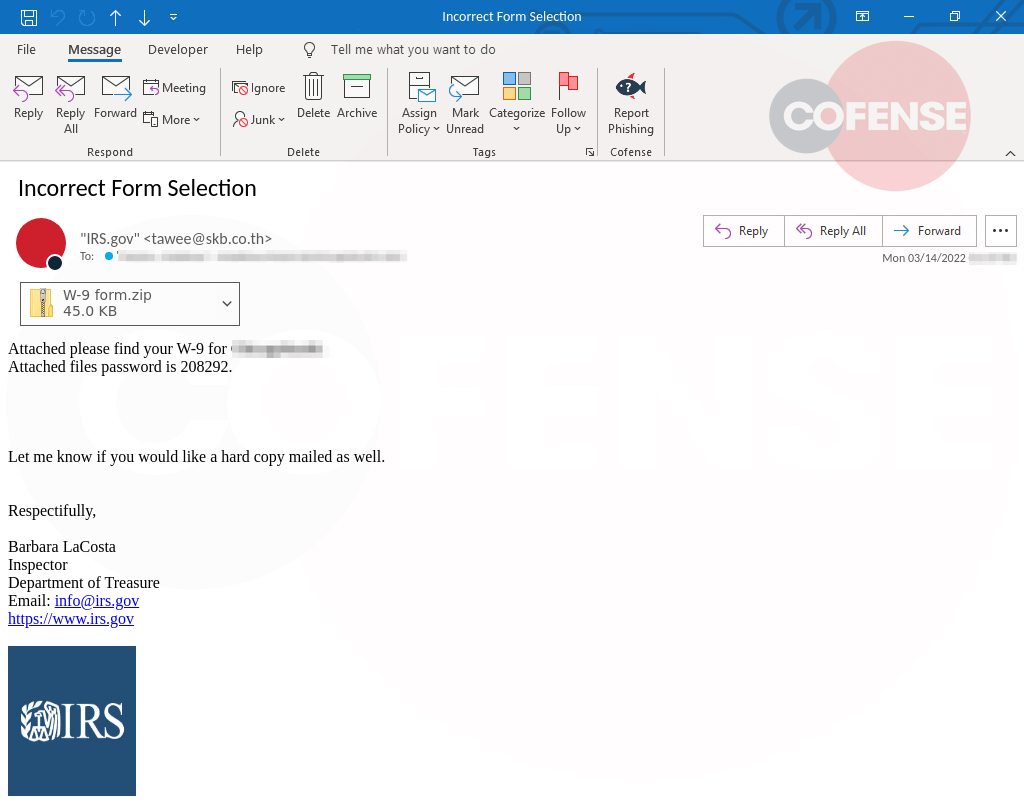
Emotet operators have inserted some variety into the text of these campaigns, likely to impede recognition by spam filters and secure email gateways (SEGs). A second example, in Figure 2, demonstrates these minimal changes, including a different subject line and signature block, with part of the body removed.
Figure 2: IRS-spoofing phishing email with some textual variety
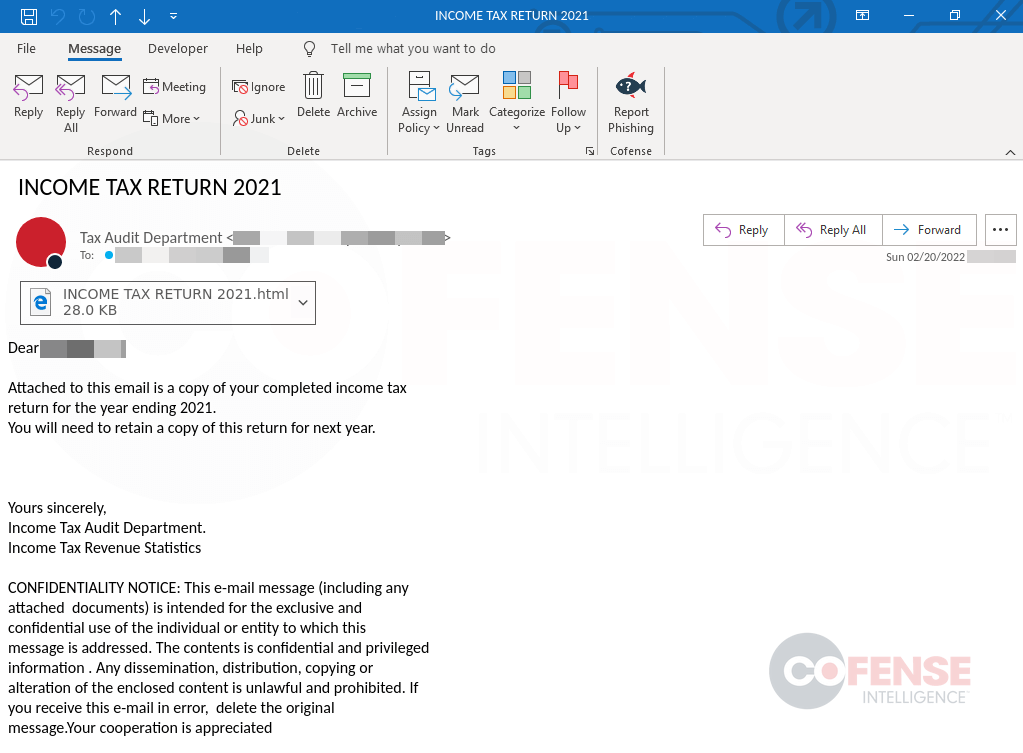
Phishing threat actors not known to be associated with Emotet have also attempted to take advantage of tax season, primarily in credential phishing campaigns. While some, such as the campaign depicted in Figure 3, actually apply the tax theme to the body of the phishing email, many simply use tax-themed subject lines, without tailoring the message body or lure documents. We expect phishing activity of this nature to continue throughout the U.S. tax season. Notably, the campaign shown below uses an HTML attachment. Many organizations have configured their SEG to block password-protected zip files as a mitigating control. However, blocking an HTML attachment can be far more difficult, based on the volume of legitimate emails containing this attachment type.
Figure 3: Credential phishing email employing tax-season theme
Organizations can better track, and fend off, attacks such as these with Cofense Intelligence and tools. Human-vetted phishing threat intelligence affords timely, accurate and actionable insights. Contact us to find out how we can help keep your systems more secure.
All third-party trademarks referenced by Cofense whether in logo form, name form or product form, or otherwise, remain the property of their respective holders, and use of these trademarks in no way indicates any relationship between Cofense and the holders of the trademarks. Any observations contained in this blog regarding circumvention of end point protections are based on observations at a point in time based on a specific set of system configurations. Subsequent updates or different configurations may be effective at stopping these or similar threats. Past performance is not indicative of future results.
The Cofense® and PhishMe® names and logos, as well as any other Cofense product or service names or logos displayed on this blog are registered trademarks or trademarks of Cofense Inc.