Last week, the FBI announced it had busted a business email compromise (BEC) racket that raked in millions of dollars in fraudulent wire transfers secured through email-based cyberattacks. The Bureau, along with federal and overseas partners, arrested 74 people, seized over $2M, and disrupted and recovered another $14M in phony wire payments.
My first reaction was, “Good, they nailed the crooks.” My second reaction was a Six Degrees of Separation moment. You see, just a few years ago our company demonstrated the fraudsters would fall for their own technique, phishing, subsequently exposing their infrastructure when they clicked. Granted, often times it was private hosting providers or VPN infrastructure, but if you do it enough times, attackers make mistakes. (…and you collect their bank account numbers).
Three Years Ago, We Broke New Ground in Dealing with BEC Fraudsters
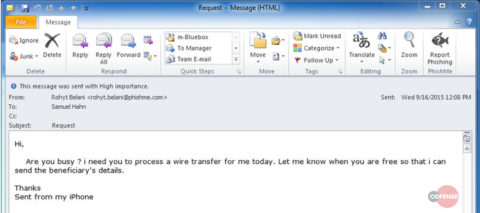
Back in 2015 PhishMe, as we were still called, received an especially egregious bit of BEC. It came to our then VP of Finance ostensibly from Rohyt Belani, our CEO. Complete with grammatical errors, the email requested a quick transfer of funds.
Figure 1: Phishing email appearing to be a wire transfer request from our CEO.
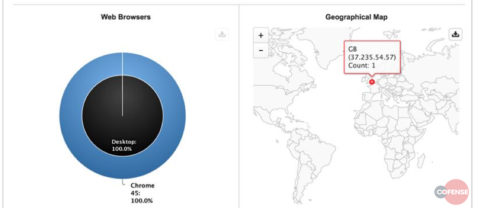
The short version: we are a phishing defense company and were not exactly amused to be targeted so brazenly. So, we phished the phisher, playing along to learn useful things like IP addresses and account numbers, which we were pretty sure law enforcement would want. They did. Here’s a blog we published, complete with details like these in Figure 2:
Figure 2: The attacker’s exit IP address.
This was the first instance of a phishing defense company turning the tables on the adversary. After our blog appeared, organizations and individuals ramped up efforts to tease information out of the email-based attackers, get them to click links, and give up their IP addresses.
Here’s What Else Can Help
One bust unfortunately won’t solve the problem of organized cybercrime and BEC threats. As some people commented since the FBI’s bust, the money it seized is a drop in the bucket. In the future, more of these aggressive law enforcement efforts would help combat the BEC threat landscape.
Organizations can help themselves by making sure their mail gateways are configured to the rigor needed, and by training users to report phishing, as our VP of Finance did. Quick sidebar: the FBI noted that one of the most common scenarios is phishing emails that come from compromised internal accounts. Those are especially hard to catch—the source looks totally legit. But with proper training and behavioral conditioning, users can help to stop these nuanced attacks.
At Cofense, we see our customers do this all the time. They have to. Perimeter security technology is a big part of defense in depth, but it’s hardly infallible. When emails get through, as they often do, your people had better be ready. We call it collaborative defense, where users feed real-time intelligence to incident responders, who in turn use automation to analyze and mitigate threats faster.
More broadly, collaborative defense means sharing intelligence and methodologies, among anti-phishing providers, industry groups, and law enforcement. It’s the kind of cooperation that laid the groundwork for the Wire-Wire bust.
Here’s hoping that we see more BEC fraudsters go to jail. If everyone does their part, it’s much more likely to happen.
For best practices to combat email fraud and more, view this Cofense-sponsored Osterman Research white paper.
All third-party trademarks referenced by Cofense whether in logo form, name form or product form, or otherwise, remain the property of their respective holders, and use of these trademarks in no way indicates any relationship between Cofense and the holders of the trademarks.