Google Doc Campaign Makes a Mark
In the process of managing phishing threats for our customers, our Phishing Defense Center and PhishMe Intelligence teams saw a flood of suspicious emails with subject line stating that someone has “has shared a document on Google Docs with you”, which contained a link to “Open in Docs”. The “Open in Docs” link goes to one of several URLs all within the https://accounts.google.com website.
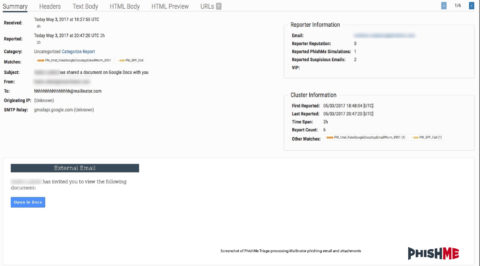
Example of PhishMe Triage in Fig 1:
Fig-1
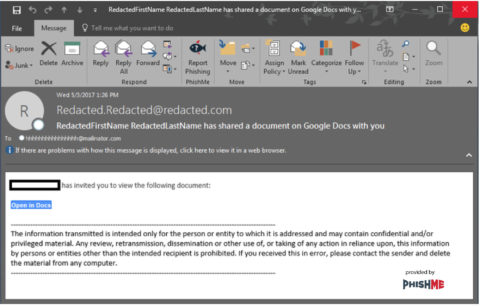
Example of Mailinator Phishing Email in Fig 1-2:
Fig. 1-2
“Open in Docs”
hxxps://accounts.google.com/o/oauth2/auth?client_id=1024674817942-fstip2shineo1l
sego38uvsg8n2d3421.apps.googleusercontent.com&scope=https%3A%2F%2Fmail.google.co
m%2F+https%3A%2F%2Fwww.googleapis.com%2Fauth%2Fcontacts&immediate=false&include_
granted_scopes=true&response_type=token&redirect_uri=https%3A%2F%2Fgoogledocs.g-
docs.pro%2Fg.php&customparam=customparam
The highlighted portion above can be any of the following:
googledocs[.]docscloud[.]download
googledocs[.]docscloud[.]info
googledocs[.]docscloud[.]win
googledocs[.]g-cloud[.]pro
googledocs[.]g-cloud[.]win
googledocs[.]gdocs[.]download
googledocs[.]gdocs[.]pro
googledocs[.]g-docs[.]pro
googledocs[.]gdocs[.]win
googledocs[.]g-docs[.]win
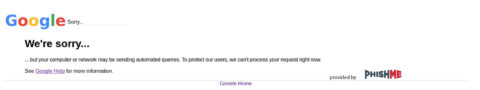
When our team attempted to access these URLs they were no longer functional. When we attempted to visit these sites, we received a Google Message indicating that to protect users they are unable to process any requests to these URLs as seen in Fig. 1-3.
Fig. 1-3
At the time of this write-up, it appears that Google has disabled the OAuth client that was being used for this campaign as seen in Fig. 1-4.
Fig. 1-4
However, prior to the Google cleanup several security teams, such as SANS Internet Storm Center, were able to provide a further look into the URLs: https://isc.sans.edu/diary/22372
Recommendation
PhishMe cautions its customers to be wary of emails containing suspicious links or attachments. Specific to this sample, we recommend that customers be observant for unexpected emails that contain subject lines referring to shared documents when not expected, and email bodies that ask you to visit a link to open a document you’re not expecting. PhishMe Simulator customers may consider launching simulations that follow this style of attack to further train their users to detect and report suspicious emails.