As with everything else this year, the holiday shopping season will be open to more cyber threats as we shift from hitting the brick-and-mortar retail outlets to the online store front. Threat actors have your wallet and credentials on their shopping list. When it comes to preparing your users, friends and family for the holiday shopping season, we’ll cover some basics to remind everyone to remain calm and protect their wallets and credentials.
Gift Cards
The ease of sending gift cards makes these a top purchase. While retailers have made it easier to purchase online and send electronically, threat actors too are leveraging this in their gift bag.
RISKY Behavior: Clicking on a link in an email without verifying the link or the sender.
SAFE Behavior: Hover over the link to see where you are being directed. Reach out to the sender directly via a separate email or text message. Many retailers will include the claim code in the message body. Navigate directly to the website to locate the Gift Card redemption page. Manually enter the claim code.
Shopping Sites
As the pandemic of 2020 began, we shifted our purchasing to online. We’ve become accustomed to navigating the online shopping world, making holiday shopping season shopping easier.
RISKY Behavior: Click a link via an email or an ad via another website.
SAFE Behavior: Navigate directly to the website for your product selection. While retailers and online banking sites proactively hunt for spoofed websites mimicking their brand, it’s a cat-and-mouse battle to find these. Ensure you are on a site that’s using encryption by verifying the lock in the address bar (URL). If the page allows you to use a secure payment method, such as PayPal, ApplePay or GooglePay, use these options to add a layer of protection to your bank account.
Shipping
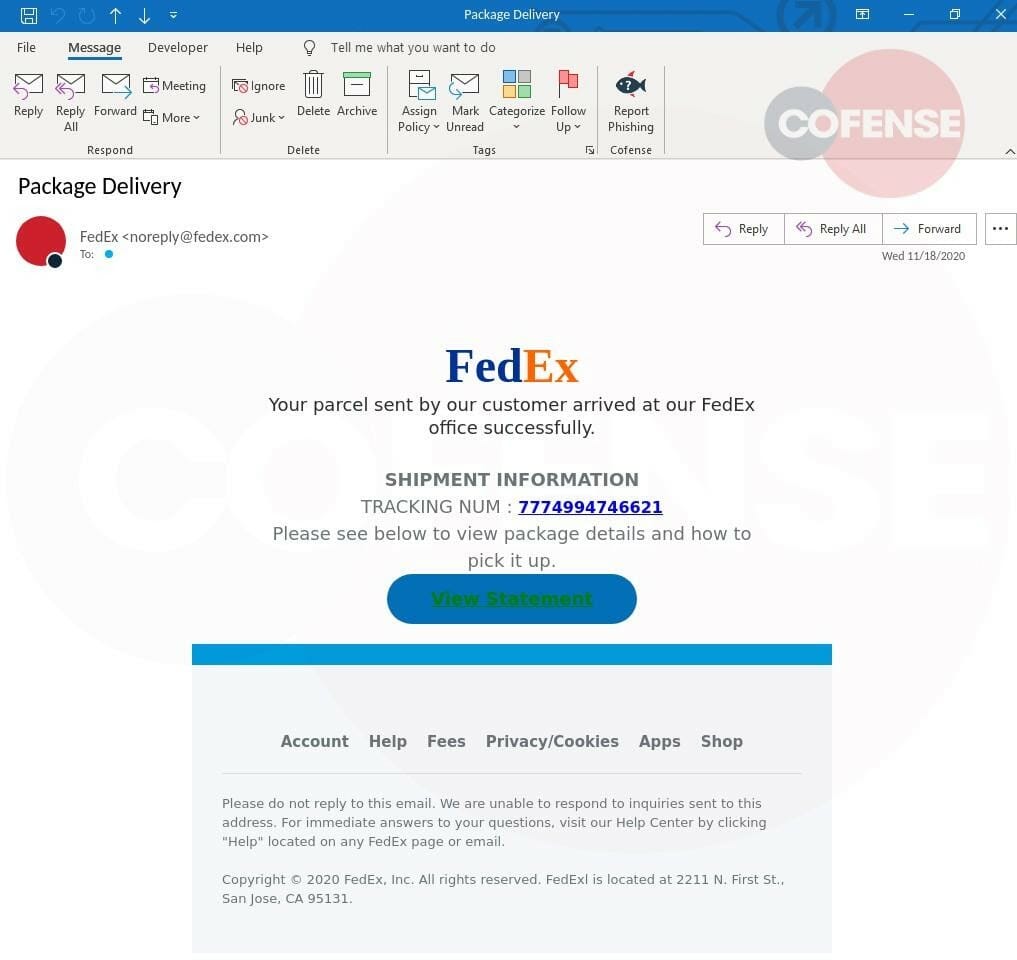
Expecting a package? Maybe you’re not expecting a package, but suddenly you have an email informing you that a special gift is on its way to your doorstep. It’s not uncommon for threat actors to spoof the popular brand, such as the phishing email sample seen below.
RISKY Behavior: Clicking the link in an unexpected email.
SAFE Behavior: Navigate directly to the website of the shipping company to get a shipping status. As with gift cards, manually enter the tracking code directly into the website’s tracking feature.
Charitable Giving
Tis the season to catch up on charitable giving to make the tax benefit cut-off for end-of-year donations. Threat actors follow the newsworthy events and leverage the theme to tug at your heart strings.
RISKY Behavior: Click on a link and providing your credit card information.
SAFE Behavior: Navigate directly to the charitable website and locate the donation giving page. Ensure you are on a site that is using encryption by verifying the lock in the address bar (URL). If the page allows you to use a secure payment method, such as PayPal, ApplePay or GooglePay, use these options to add a layer of protection to your bank account. If you receive a phone call asking for your donation for a worthy cause that you support, take down the name and inform the caller you’ll follow up at a later time. At that point, follow the same steps to navigate directly to the charitable website.
Enjoy a safe and cyber-secure holiday! Remember that Cofense is always here to help. Check out our phishing resource center for best practices and product information to fight phishing.