Author: Megan Horner
“Continued increases in the volume and success of phishing attacks and migration to cloud email require a reevaluation of email security controls and processes. Security and risk management leaders must ensure that their existing solution remains appropriate for the changing landscape.” *
Gartner®
You know that feeling? The one where you think you’re doing a good job. You feel like you’re doing okay. But the reality is you just aren’t quite 100% sure? A lot of security professionals we talk to feel the same. That feeling, when paired with guidance from companies to reevaluate their email security controls, usually leaves someone trying to answer the question of, “How do I objectively evaluate the efficacy of my email security controls against real, active threats?”
The team here is happy to announce the release of Cofense Validator to help answer exactly that. Cofense Validator helps organizations understand the effectiveness of their secure email gateways (SEGs) by testing them with active, live phishing threats.
With Cofense Validator, you can:
- Understand how your SEG will protect against real world email threats
- Understand how your SEG compares to other SEG solutions (including Microsoft) for different threat types
- Quickly evaluate how changes to your SEG’s configurations will affect efficacy
- Articulate email security control performance clearly and help make decision-making more objective
Let me walk you through some reasons why this is so valuable:
Assess performance against real, active phish
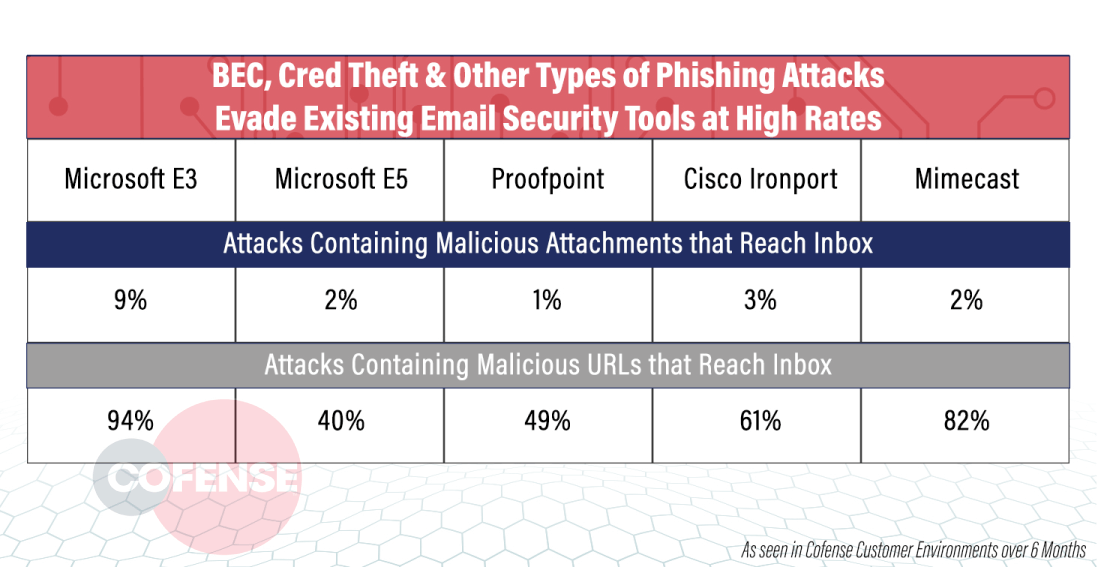
The ability to run an assessment using standard malware test files is a great first step, but what you really need to know is whether today’s active, real threats will make it to your users’ inboxes. Cofense Validator uses what we know about advanced phishing attacks from Cofense Intelligence to test SEG effectiveness against current, verifiable, live phishing threats – not older threats that are already found on commonly access deny lists or threats that are built specifically from intelligence you’d expect the email security vendors to already have access to. Email security controls are successful at catching traditional phishing tactics that utilize malicious attachments, but as you can see in Figure 1, most perform poorly when it comes to protecting against phishing attacks that contain malicious URLs, with most seeing well over 40% make it to the inbox. Spoiler Alert: This data came from real Validator customers!
Figure 1: Validator Results
Optimize SEG configuration to increase efficacy
Having data to work with is a great starting point but putting that data to work to make positive changes is what it is ultimately all about. Most security purchases are a considerable financial and time investment so ensuring they are performing at their tip top best is key. Validator enables you to set up multiple configuration profiles to test what specific changes could affect your inboxes when it comes to how many and what type of phishing attacks are successfully blocked. Think of it as a vulnerability assessment. But a vulnerability assessment with the ability to constantly tweak and improve your configuration to know instantaneously that you are better protected. Your SEG vendor just implemented an update to their product – did they change anything that impacts your risk? We’ve heard from customers this is a thing!
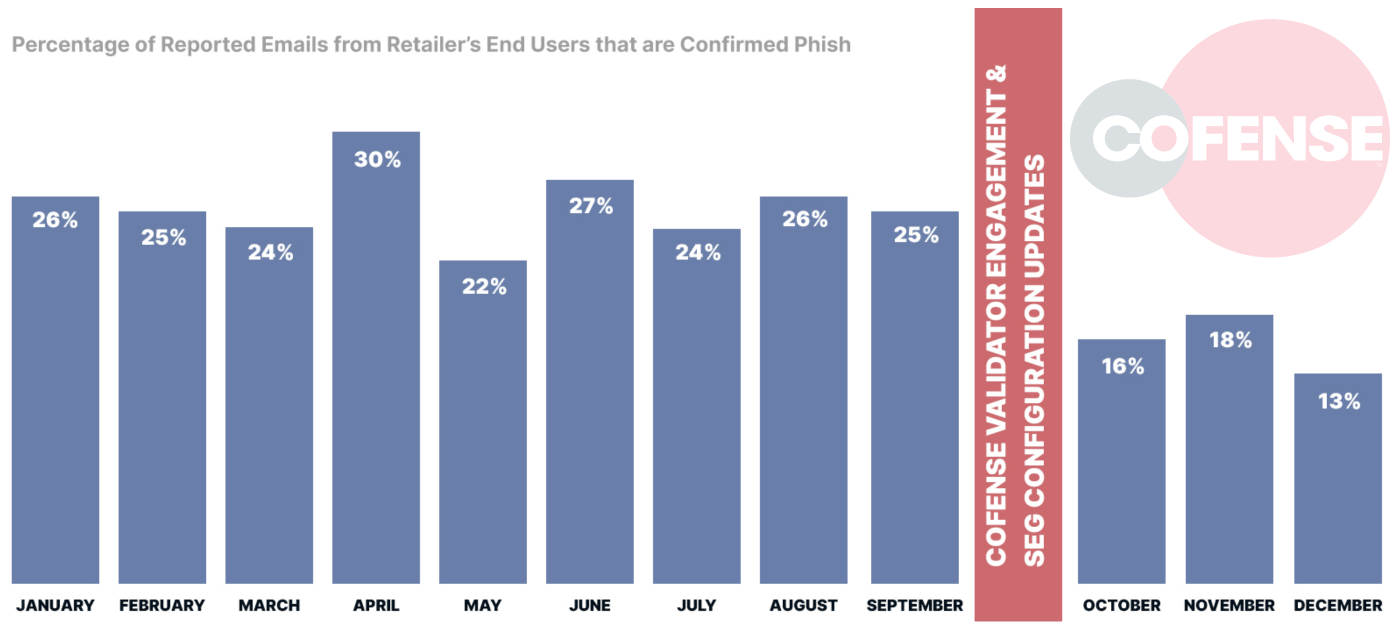
Recently, we worked with an electronic and building materials retailer to do exactly this – optimize their SEG configurations. Cofense Validator was able to quantitively show the efficacy levels of multiple configurations, providing this organization with clear insight into which was the right choice for them. Over time, we can understand the practical implications this has on security posture. Prior to making configuration changes to their email security controls, a retailer regularly saw around 25-30% of their reported emails were confirmed malicious. Immediately after updating the configuration post-Validator engagement, there was about a 10% drop to 15.8% confirmed malicious showing immediate impact to overall email security posture. This number continues to decrease which likely points to less malicious emails landing in the inbox resulting in less malicious emails being reported. Read the full case study here.
Figure 2: Retailer Sees 10% Drop in Malicious Email After SEG Configuration Changes
Make data-driven consolidation and purchasing decisions
The focus on digital transformation and vendor consolidation has all eyes on the performance level of technology and how it impacts the rest of the business. Having the responsibility of deciding where to reduce costs and where to consolidate is a heavy burden to bear unless you are making confident, data-backed choices. With Validator, compare SEGs against one another to understand the types of threats being blocked by each to reduce redundancy and unnecessary spend in your organization.
Organizations can even use this information when making initial purchasing decisions for an objective, third-party benchmarking assessment.
Although you certainly should trust us, we’re not the only ones who realize the impact that Cofense Validator can have on your email security posture.
“As an organization with multiple environments and controls, keeping email security in lockstep has always been challenging. Outside of traditional validation testing with dummy files, the only way we could gauge email security effectiveness would, unfortunately, be through triaging real threats that made it to our actual mailboxes. Without a way to continually evaluate our controls, drift was not possible to track. Validator has allowed us to get meaningful evaluations of how each of our environments stacks up in a way that reflects real-world attacks, helping us determine which controls we are lacking (or which controls are too tight). Validator has also provided us with an additional means of testing potential email security solutions against our current setup to make smarter purchasing decisions that have an actual impact on our organization’s security.”
— Financial Services Organization
Ready to see more? Request a demonstration of Cofense Validator today.
All third-party trademarks referenced by Cofense whether in logo form, name form or product form, or otherwise, remain the property of their respective holders, and use of these trademarks in no way indicates any relationship between Cofense and the holders of the trademarks. Any observations contained in this blog regarding circumvention of end point protections are based on observations at a point in time based on a specific set of system configurations. Subsequent updates or different configurations may be effective at stopping these or similar threats.
The Cofense® and PhishMe® names and logos, as well as any other Cofense product or service names or logos displayed on this blog are registered trademarks or trademarks of Cofense Inc.
* Gartner®, “Market Guide for Email Security”, Mark Harris, Peter Firstbrook, Ravisha Chugh, 7 Octoboer 2021. GARTNER is a registered trademark and service mark of the Gartner, Inc. and/or its affiliates in the U.S. and internationally and is used herein with permission. All rights reserved.