By Zachary Bailey, Cofense Phishing Defense Center
Using Cofense Vision, analysts at the Cofense Phishing Defense Center (PDC) were able to drill down into the targeting patterns of one phishing campaign that leveraged Verizon’s multimedia messaging service – Vzwpix. On its own, Vzwpix.com allows Verizon customers to send their texts as emails to recipients, which will then be delivered to their inbox rather than phone messages.
Most phone providers have a similar service offered, but the benefits of this utility go beyond just convenience. Threat actors can utilize these services to mass deliver texts that come from a phone number, but not show the name of the sender. This can leave recipients guessing who sent them if they do not recognize the number. Hesitant users have the option to report these messages to the Cofense PDC for further analysis to ensure they are benign.
In recent weeks, the Cofense PDC received hundreds of reports for Verizon’s Vzwpix service domain. Most of these are non-malicious texts or images, but reporters are always vigilant of potential threats. This week, customers in a variety of different industries were targeted by threat actors using Vzwpix.com
What is Vzwpix.com?
Vzwpix.com is a website associated with Verizon that allows customers to store, view, and share photos and videos. This makes it convenient for sharing pictures with family and friends by creating customized slideshows or linking them directly to social networks like Facebook, Twitter or Instagram.
It is free of charge and available to anyone with an active Verizon account.
Figure 1: Email body from Vzwpix.com
In Figure 1, it can be seen that the received message is a simple text without any styling or images. It references a new voicemail and uses a financial lure involving ACH transfers. The link is displayed as plain text, letting users know exactly where they will go. It was able to evade initial analysis from the secure email gateway (SEG) by using a legitimate survey application; however, some SEGs would be able to check the content of the survey via link-click.
Here, the threat actors leveraged Alchemer, a survey form builder that makes it easy to create a survey for users to fill out. Threat actors have used various survey sites to quickly generate simple quizzes/forms asking users for their account information. These templates allow custom backgrounds and images, speeding up the rollout of their new phishing pages.
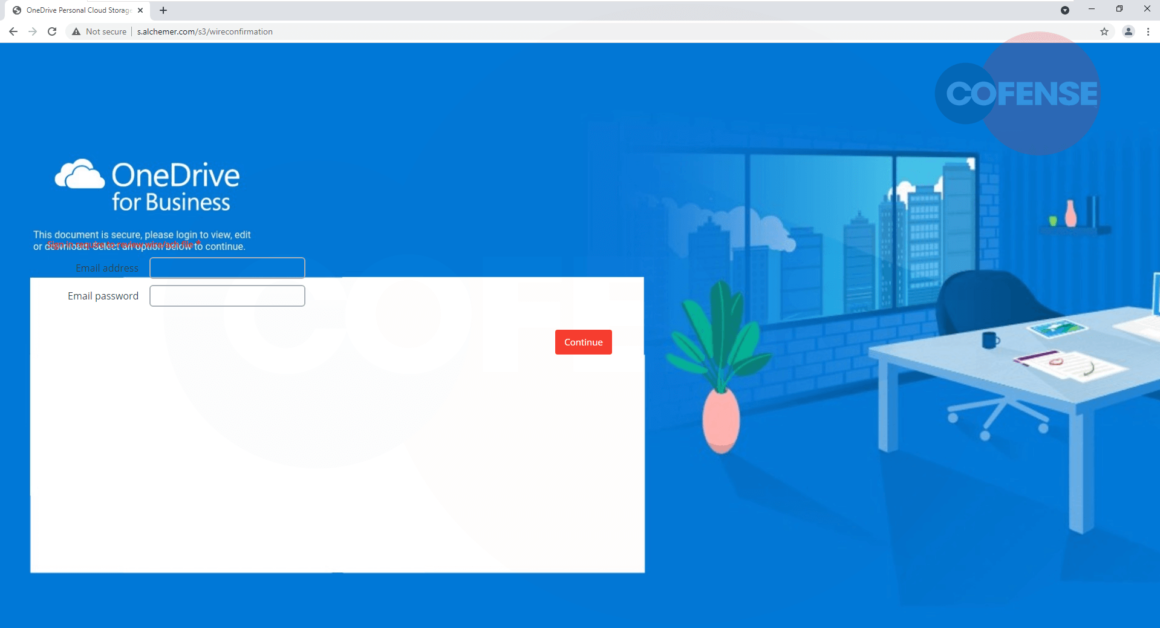 Figure 2: Phishing Page (Desktop View)
Figure 2: Phishing Page (Desktop View)
Figure 3: Phishing Page (Mobile View)
In Figure 2, the survey is incorrectly formatted as a OneDrive login page and most users would suspect this is not a legitimate Microsoft OneDrive login page. The continue button is also off to the side, making the page look like it was not designed to be viewed through a PC web browser. When switching to a mobile device, shown in Figure 3, there is a clear difference between the layouts of the form. The resized phishing page is drawn within the white box and the button is aligned with the entry fields.
A user on a mobile device might not notice this is not the Microsoft site at first given the ease in which they can interact with the form. However, typical indicators of phish remain such as an easily viewable wrong address in the address bar.
Figure 4: Targeted Companies
Using Cofense Vision, analysts were able to identify multiple employees who received the same message at their company. Even though each message came from the same phone number, they all had different message IDs.
In Figure 4, we can see a portion of the results found clustered by these unique indicators, which were exported from Cofense Vision. These message IDs are related to the Verizon phone number that sent out the messages. Each message ID corresponds to a different group of recipients that were in the “To” address of the email.
Figure 5: Industries Represented by Percentage for Manufacturing Customer
By analyzing these clusters, we can discover new trends in how these seemingly unrelated recipients were targeted. At first glance, each cluster had a minimum of ten email addresses including PDC customers and external domains. Several clusters had multiple emails targeting the same domain, indicating a possibility that these were likely not sent at random but were from a list of targets by industry. By stripping out just the unique domains, it can be determined that 50% of all recipients were in the food manufacturing industry, shown in Figure 5.
The PDC customer targeted in these clusters is in the manufacturing industry, but one of its primary subsidiaries is involved in food manufacturing. Supply chain and media companies make up another 25% of the targeted domains.
Figure 6: Industries Represented by Recipient for Financial Customer
The remaining PDC customers targeted by this campaign did not have Cofense Vision but reviewing the reports of one customer shows a similar trend. This customer is in the financial industry and, as shown in Figure 6, 60% of the other domains contacted are also in the financial industry, with 25% being in the legal industry.
When an organization leverages Cofense Vision, your SOC team can leverage these searches to identify if any of your business partners are also targeted and manually alert them. The Cofense network effect allows the actions of one reporter to shield our customers from threats, and since Cofense sits behind any SEG, a new tactic used that might slip into an employee’s inbox can be remediated with a single click before they know it is there. Reach out us to learn more about Cofense Vision and the PDC.
| Indicators of Compromise | IP |
|---|---|
| hXXp://s[.]alchemer[.]com/s3/wireconfirmation | 54.208.81.3 |
All third-party trademarks referenced by Cofense whether in logo form, name form or product form, or otherwise, remain the property of their respective holders, and use of these trademarks in no way indicates any relationship between Cofense and the holders of the trademarks. Any observations contained in this blog regarding circumvention of end point protections are based on observations at a point in time based on a specific set of system configurations. Subsequent updates or different configurations may be effective at stopping these or similar threats. Past performance is not indicative of future results.


