By Kian Mahdavi, Cofense Phishing Defense Center
The ever-increasing need to both access and store documents via the cloud has fueled the increased risk for Microsoft OneDrive credential-phishing attacks. Threat actors have subsequently used this to their advantage to socially engineer people to click on a link that results in harvested credentials. However, well-conditioned users quickly identify these suspicious emails and use Cofense Reporter to alert the security team.
The first stage of this attack utilized OneDrive’s legitimate cloud services and managed to slip past both Microsoft and Proofpoint secure email gateways (SEGs). Why? The current detection controls for both SEGs can’t detect the malicious site hosted in the second-stage URL redirects that had been wrapped into a hosted PDF document, as we’ll later learn.
The URL in Figure 1 had been shortened so, if the user were to hover over “bekijken,” (which translates to “view”), they would not be able to see the entire content. This might spark the user’s curiosity.
Figure 1 – Email body
Figure 1 showcases text that had been kept short, sweet and to the point. Once translated from Dutch, the email body read: “ shared a file via OneDrive”, followed by “Kind Regards.”
When users click the hyperlinked part of the text, they’re taken to the initial-stage phishing landing page. As previously mentioned, the PDF document was hosted within OneDrive’s cloud services.

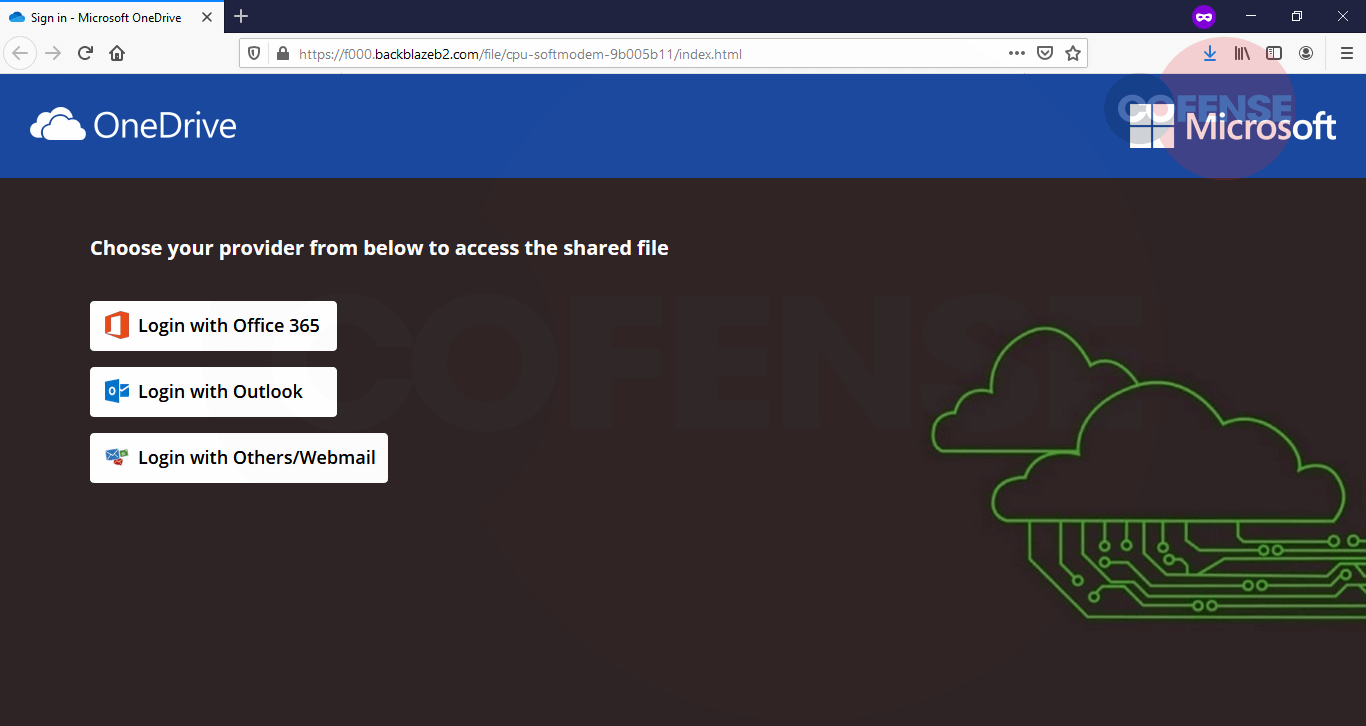
Once the user clicks “Access Document” as noted in Figure 2, the user is automatically redirected to a phishing page showcasing various login options. This is a common tactic used by threat actors to harvest as many credentials as possible.
Figure 3 – Second-stage phishing landing page
There’s a diverse set of mentioned services for user authentication. We clicked on “Office365” and “Outlook” and the following login webpages appeared.
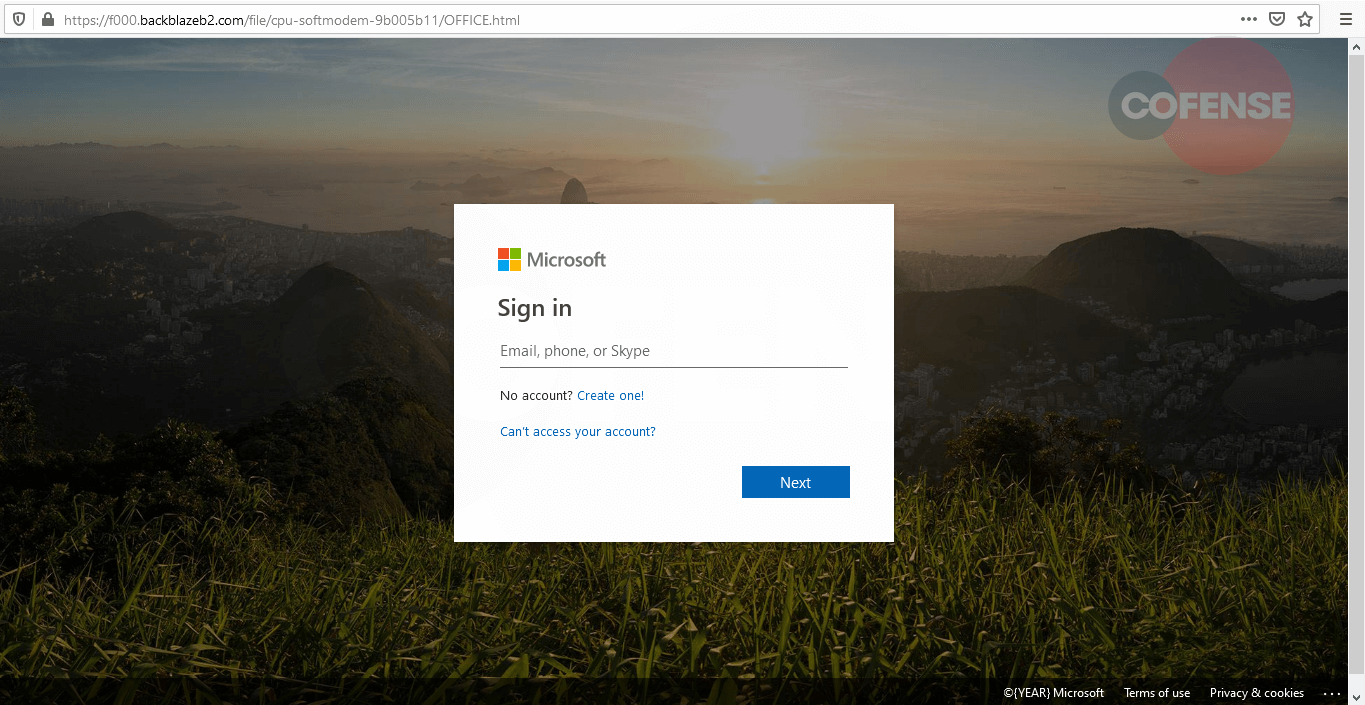
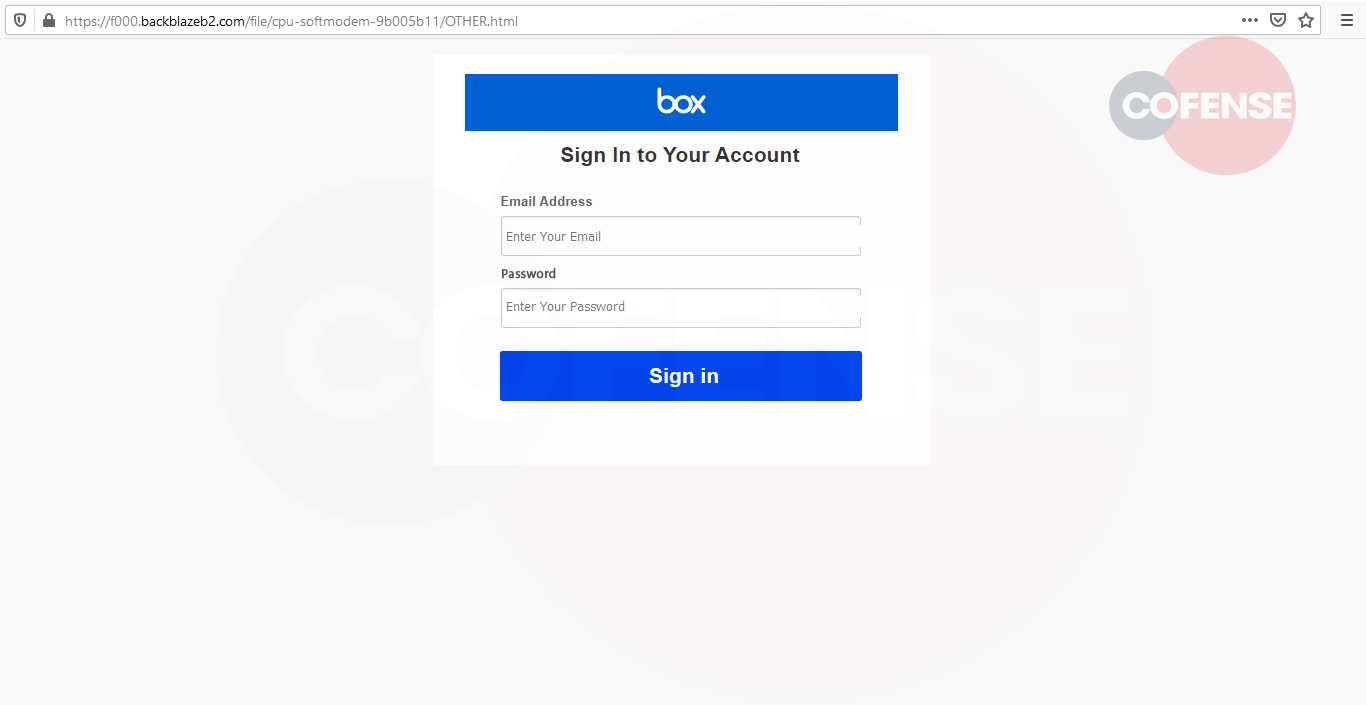
Both URLs within Figures 4 and 5 were hosted using the identical domain, apart from a slight change in the subdirectory domain toward the end. We noted from Figure 5 that the user was displayed with a “Box” login page as opposed to an “Outlook” webpage. We assume that this may have been a mistake by the threat actor.
If credentials had been supplied and entered, the users would immediately be taken to a well-known business’s research article to allay suspicions regarding the transaction’s legitimacy. If users entered their true credentials, their data would unfortunately be in the hands of the threat actor.
This credential-phishing scheme illustrates once again that threat actors will always find ways to gain a user’s trust and then use that trust to malicious ends. With Cofense, enterprises benefit from our complete view of real phish. We help businesses cut through the noise to catch and contain phish. Contact us today to find out how. We’re here to help.
Indicators of Compromise
| Network IOC | IP |
| hxxps//1drv[.]ms/b/s!AqiKtGK7_q5BhnXo7zkxqgHVPLWk | 13[.]107[.]42[.]12 |
| hxxps//onedrive[.]live[.]com/?authkey=%21AOjvOTGqAdU8taQ&cid=41AEFEB B62B48AA8&id=41AEFEBB62B48AA8%21885&parId=41AEFEBB62B48AA8%21107 | 13[.]107[.]42[.]13 |
| hxxps//f000[.]backblazeb2[.]com/file/cpu-softmodem-9b005b11/ | 104[.]153[.]233[.]177 |
| hxxps//jupitersmt[.]com/email-list/onedrive25/finish[.]php | 104[.]21[.]3[.]132 |
| hxxps//valvadi101[.]com/email-list/finish-unv2[.]php | 172[.]67[.]130[.]186 |