As phishing continues to spread, executive teams across the globe are asking: “How well does our company recognize, report and respond to the threat?”
To answer that question, it helps to have a framework for anti-phishing capabilities, including ways to measure them. PhishMe® Professional Services uses the model below.
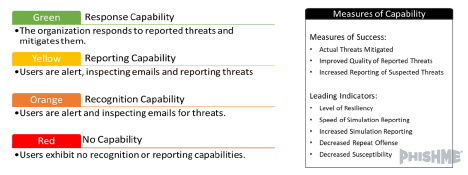
As you can see in the chart above, capability ranges from none (Red) to full ability to analyze and respond to reported phishing (Green). Likely, your organization has a scattered set of these capabilities that require further development.
There are three key factors in moving from Red to Green.
- First is the ability to develop malicious email recognition skills in your user base. This is most often accomplished via a well-run anti-phishing simulation program.
- Second is the addition of user reporting capabilities. This function is the lynchpin in getting users to act as “informants” of phishing intel for further analysis and mitigation.
- Third is automation of analysis and categorization of user-provided intel. Without an ability to analyze and respond in “near real-time,” you lose your advantage in closing the gap on malicious emails that have already penetrated perimeter defenses.
Once these capabilities are in place and you’re monitoring success measures, you’ll also want to simulate new threats your company faces, along with ones to which your employees are showing less resilience.
How should you measure anti-phishing program success?
As we can see in the model above, the key program-level measures of success and behaviors we wish to encourage are:
- Real phishing threats mitigated
- Indicating increases in organizational capabilities in incident response
- Higher percentage of reported phish that are malicious
- Indicating greater efficiency in identification of malicious email
- Increased reporting of suspected phish over time
Indicators of anti-phishing program progress:
As your anti-phishing programs mature over time, consider the following as leading indicators that your program is on the right track, but not as identifiers of ultimate success.
- Increase resiliency rate on simulations
- More users reporting than found susceptible on simulations
- Speed of reporting
- Are users reporting your simulations before others fall victim to them?
- Increased reporting of simulation scenarios
- Decrease in susceptibility and repeat offense rates across like themes, complexity and motivators
In short, users in your company need to be able to recognize and report active phishing threats, so that your incident response teams can analyze and respond prior to a breach and potential exfiltration of data. When you’ve got these 3 R’s covered, you’ll have clear and convincing answers to phishing questions from the C-suite.
Learn more about the role of organizational maturity in anti-phishing programs. View PhishMe’s 2017 Phishing Defense and Resiliency Report.