Author: Tonia Dudley
As we close out our 2022 Annual State of Phishing Report webinar series, we addressed ransomware as it relates to phishing. While we don’t see ransomware delivered in an email campaign, there are plenty of tactics used by threat actors as leading entry into the organization. As we have repeatedly addressed, we can’t stress enough that credential phish, at 67%, still remains the number one phishing threat today.
For those that missed our ransomware webinar, below are three key insights that we discussed as ways to address ransomware as an organization.
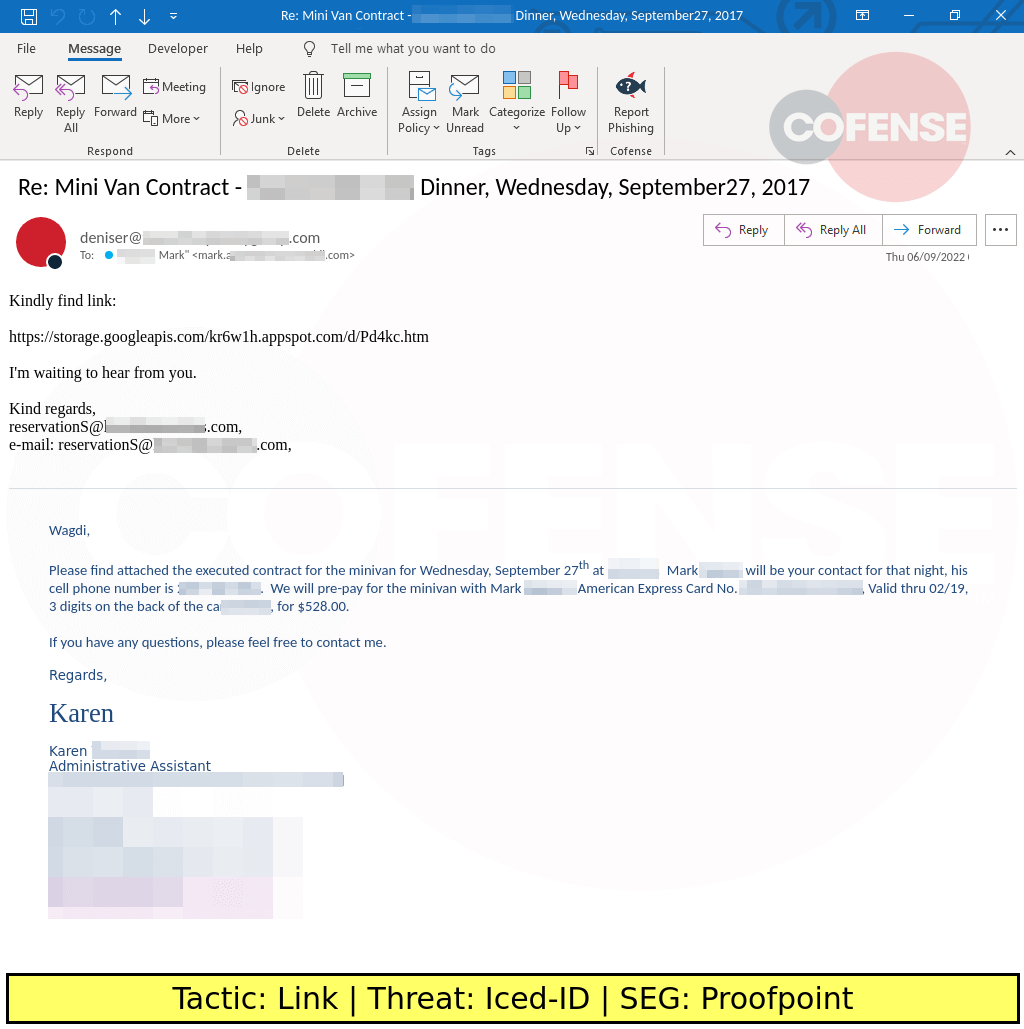
One of the highlights from this webinar was a tactic that has been seen by Cofense only twice in the past five months. This banking trojan, IcedID, is used to steal information such as credentials. What’s interesting about this email is the fact the threat actor leveraged an email from 2017, also using the reply-chain tactic. It’s no surprise the recipient thought this was suspicious and quickly reported this email to our Phishing Defense Center (PDC).
Key Takeaway #1 – Resiliency is key to defending against Ransomware
As we look at the attack chain specific to ransomware, there are several precursor steps that take place before the ransom note is delivered. The key to building a resilient workforce is providing them with relevant phishing simulation training that aligns to current threats hitting their inbox.
Key Takeaway #2 – Zero Days are in play.
As threat actors in the ransomware community have built up their resources, they are now able to step into the zero day arena to further their attacks. We briefly addressed the Microsoft zero day published in late May that has been weaponized by the QakBot group. For more on that specific threat, keep an eye out for our quarterly Threat Intelligence webinar to gain more insights.
Key Takeaway #3 – Credential Phish and HTLM attachments
We reported credential phish taking a 10-percentage point jump over the previous year in our annual report. Cofense continues to observe this as the top threat in the first half of 2022. While fewer attachments are landing in the inbox, the top file type that continues to be successful are HTML / HTM files. Organizations should look for ways to identify ways to mitigate this threat by tuning their controls.
For additional insights from our 2022 Annual State of Phishing Report webinar series: