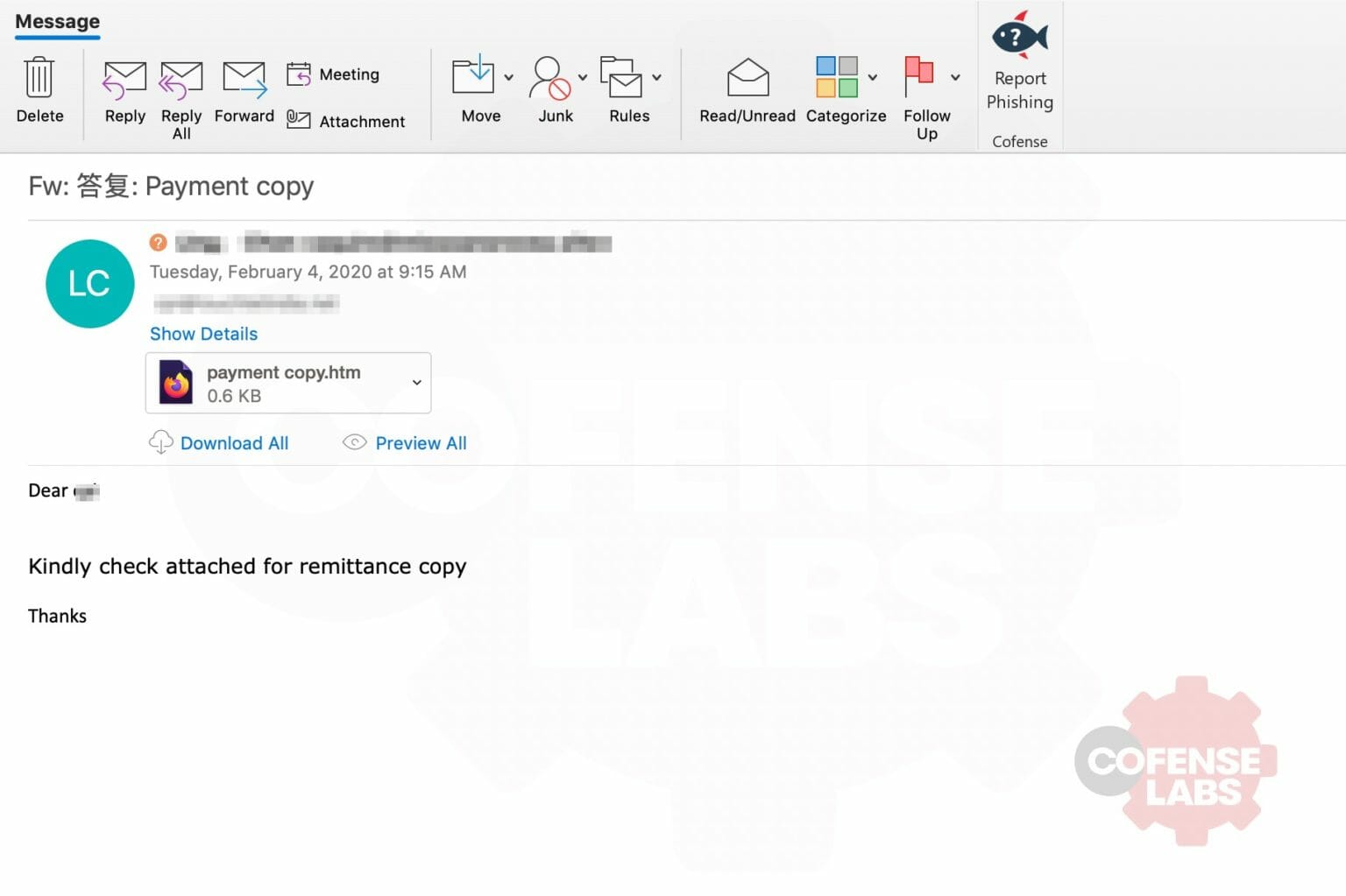
We were looking through some of our latest data and came across an interesting phish. It wasn’t extremely well crafted as can be seen in the image below.
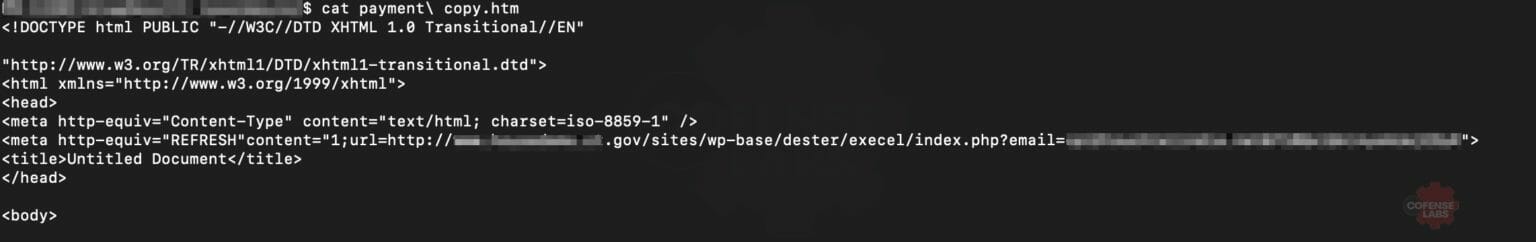
You might ask yourself why this is even worth looking at. Well it turned out that there was a very interesting URL within the attachment.
This phish was using a .gov domain to deliver its payload. I won’t go in to naming who it was as it appears that they’ve since caught the compromise and cleaned up the various spam and payload links that were nested within their domain. But as with any interesting phish, I took it as a cue to maybe have a look around and see if I could find anything similar or related to this.
Still one of the best hunting tools: Google Dorking
We took what we saw from the first phishing link and made it a tiny bit more generic:
Site:<redacted>.gov
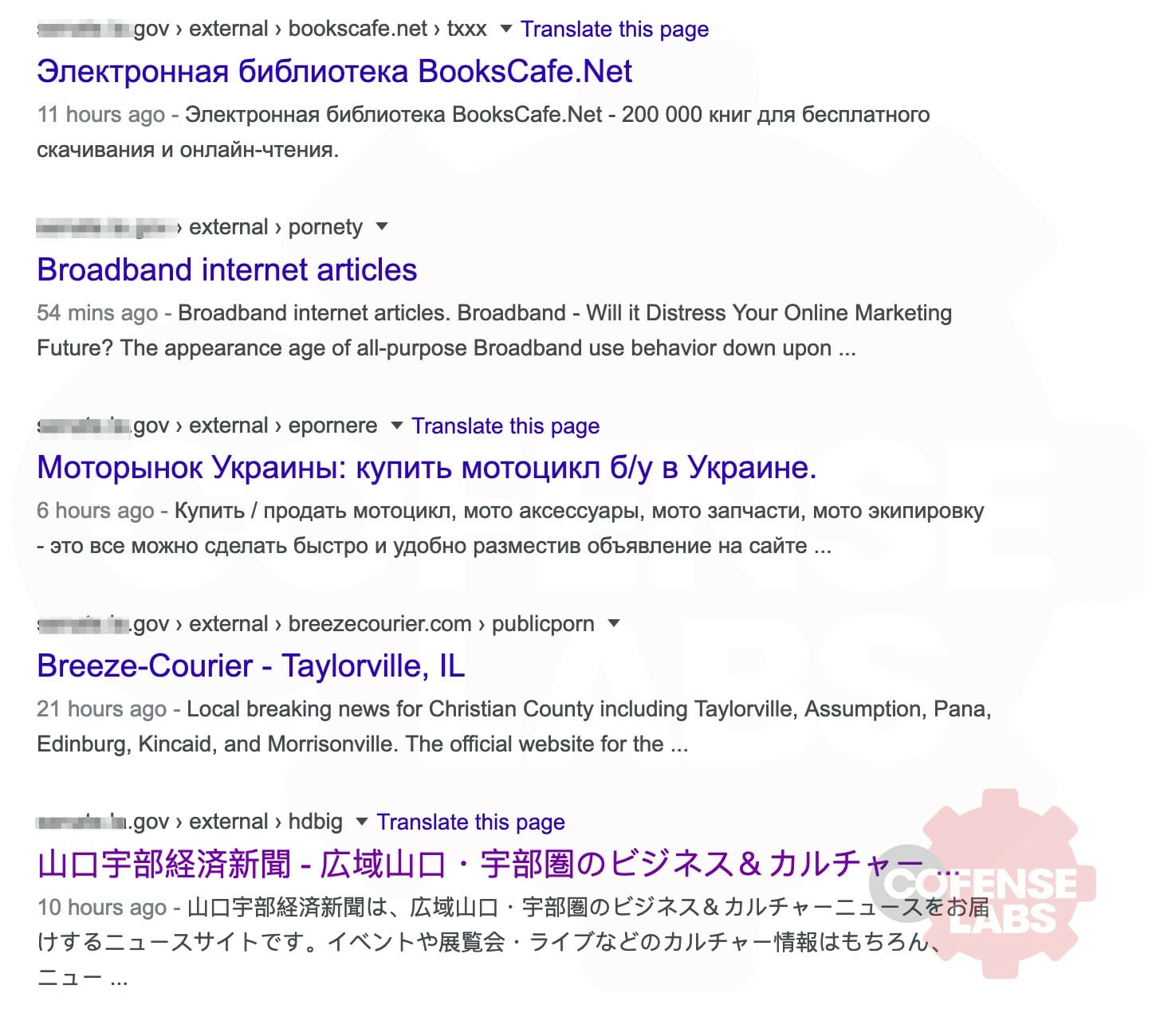
Well, that returned some interesting results. A number of links to what appears to be Chinese language pages selling random items like watches and hard drives hidden in there. We did some quick digging and it appears that they’ve since cleaned up that mess. But google had already indexed them and based on timestamps of when they were seen, we could infer that they dealt with this problem from late Dec thru late January of this year. At least we still had some insight in to what the pages held. By leveraging the text within the google results, we could expand our search a bit more.
Site:*.gov <keywords from old compromise>
Well would you look at that. Apparently, <redacted>.gov wasn’t the only one with a problem and there’s still some out there. A little bit of further digging reveals that at least one .gov is still allowing for open redirects.
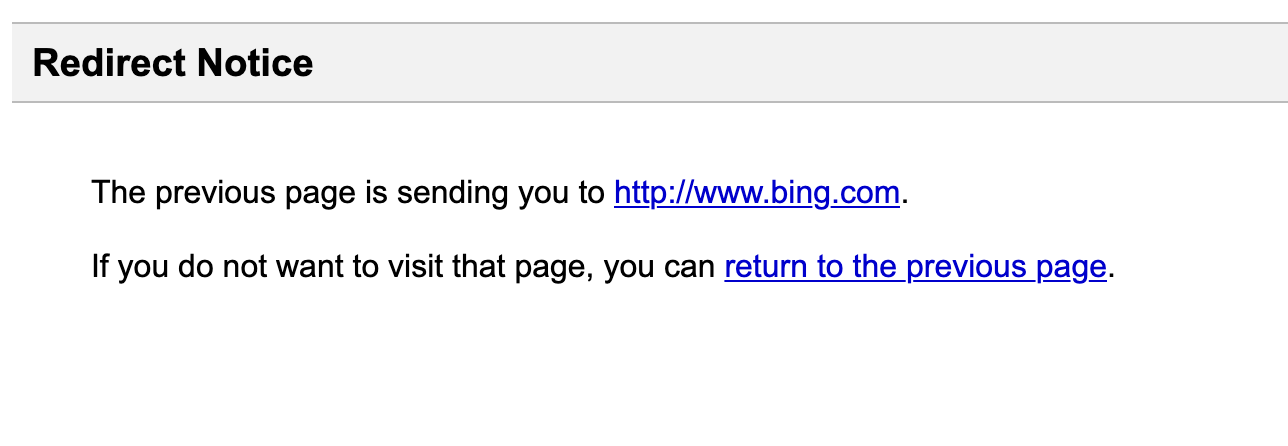
Now, I can understand that sometimes that may be needed, but it’s patently obvious that they are being abused by phishers. In fact, it appears that there have been multiple redirects chained together in some instances. For a normal end user, the quick review of this domain may lead them to believe that they are navigating to a legitimate site. Without a proper halt added to a redirect that notifies the person of the redirection, they may never notice. Google does an amazing job of this with their warning:
https://www.google.com/url?q=http://www.bing.com
This is why training people to really inspect what they are about to click on is so important. And if they aren’t sure, to just not click at all.
All third-party trademarks referenced by Cofense whether in logo form, name form or product form, or otherwise, remain the property of their respective holders, and use of these trademarks in no way indicates any relationship between Cofense and the holders of the trademarks.