In our 2017 Enterprise Phishing Resiliency and Defense Report, PhishMe® discusses the importance of moving past susceptibility as a key indicator of anti-phishing program success. We want to shift the conversation from vulnerability (susceptibility) to capability (resiliency).
That is, what are an organization’s current anti-phishing capabilities—and how is positive behavior increasing them over time to build resiliency?
The chart below tracks behavior among our clients’ users during phishing simulations. In it, resiliency equals users that “reported only” divided by “all that fell susceptible.” (The latter includes those that reported after falling for simulated phishes.)
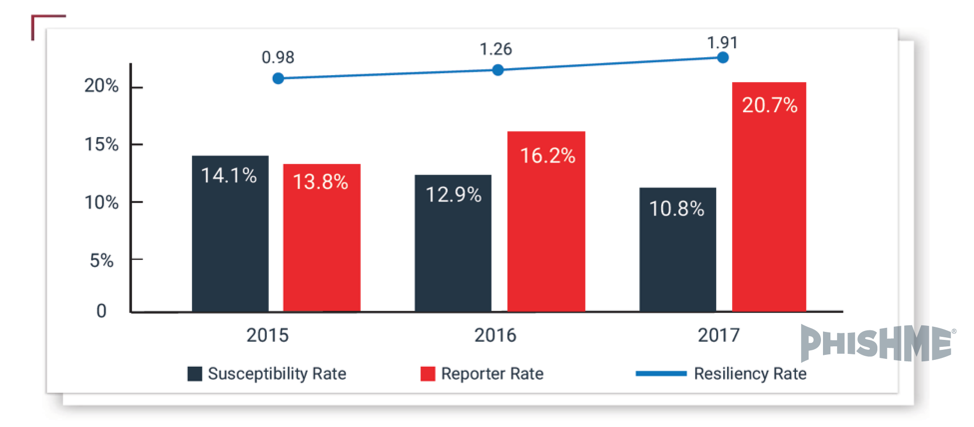
As you can see, PhishMe clients using PhishMe Reporter® show consistent gains in the capability to recognize and report phishing simulations. In other words, they are becoming more resilient to attack.
Using our formula…
Resilience = Users that Reported Only/All Susceptible
…we can determine the current level of resilience, to any specific phishing simulation or known active threat model. It’s a snapshot of the capability to recognize and report.
To see how this capability changes over time, let’s look at a chart that measures all the ways users behave in simulations.
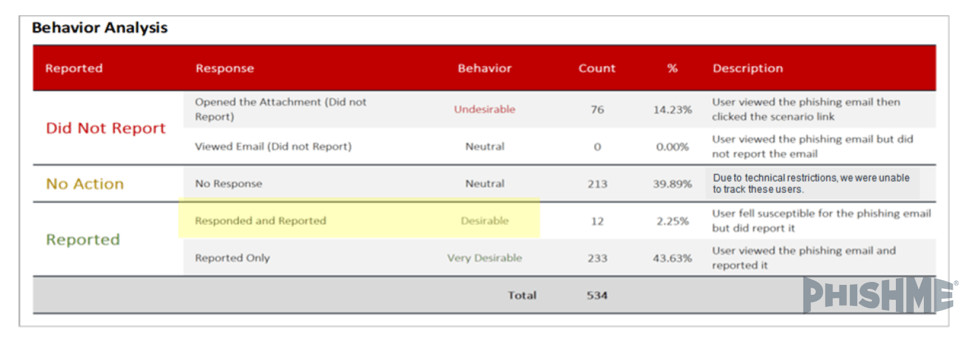
While the ideal outcome would be for all tested users to report only, that’s unlikely to happen. But, we can track two other key percentages shown above:
- Responded to Simulated Phish – Did Not Report
- Responded to Simulated Phish – Reported
Because the change you want to see is the reporting of suspicious emails, you expect to see a steady increase in “reported only” or “responded and reported.” Thus, if you were to run the simulation above again to the same user base, you would want an increase in the 43.63% of “reported only” and the 2.25% of “responded and reported.” You would also want a decline in the 14.23% of users that did not report.
This shows how the real goal of anti-phishing programs goes beyond finding vulnerabilities. The longer-term goal is to fortify capability—to build resiliency. Simply put, you want every user that interacts with a simulation to report it.
To learn more about successful anti-phishing programs, be sure to download the 2017 Enterprise Phishing Resiliency and Defense Report.


