The Cofense Phishing Defense Center (PDC) has observed a phishing campaign that aims to harvest Office365 (O365) credentials, masquerading as an Outlook Security update email from the IT Security department to entice employees to open a “New Policy” PDF.
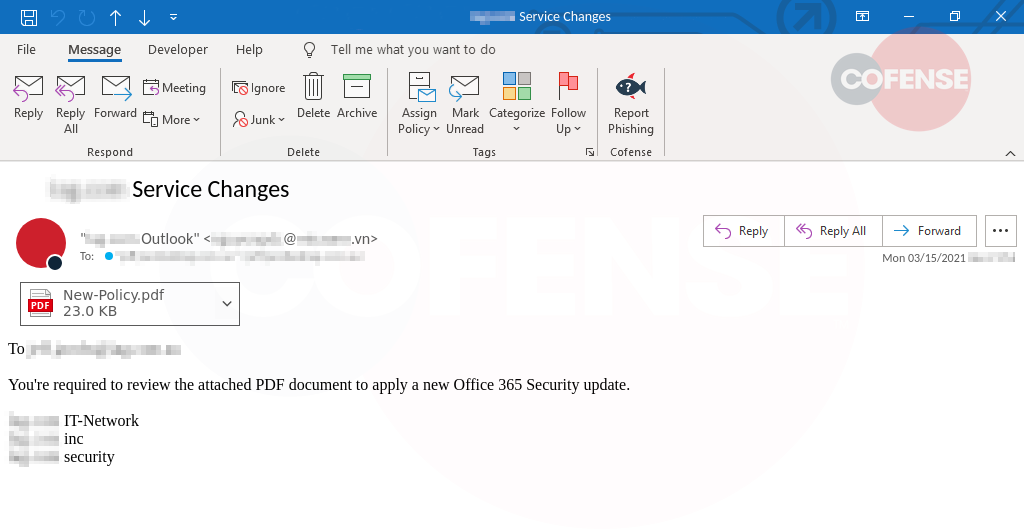
Figure 1: Email Body
The subject of the email immediately lends credence by including the company name: “ Service Changes.” In addition, the threat actor has spoofed the sender name to appear as “ Outlook.” With the personalization of the subject and sender information, users are more likely to open the PDF.
Cofense continues to see PDFs leveraged to deliver links directing users to sites to enter credentials or download malware. This tactic often allows threat actors to slip corrupted content past traditional email security and into users’ inboxes.
In the first line of the email there is verification that the message is meant for this user “To ”. Threat actors use this tactic to instill a sense of significance to the email. The body of the email directs the recipient to review the PDF in order to “apply a new Office 365 Security.”
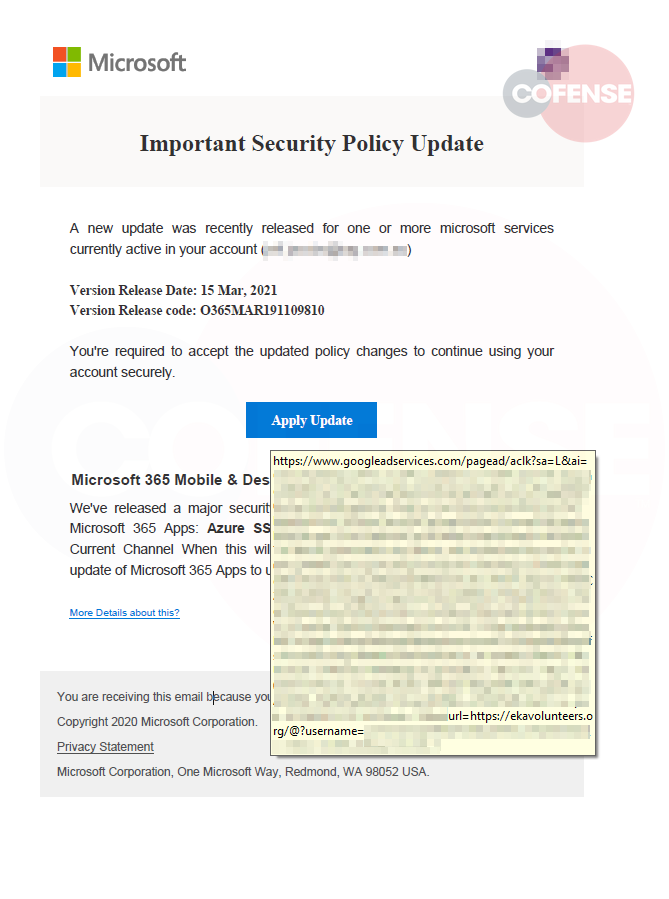 Figure 2: New-Policy.pdf
Figure 2: New-Policy.pdf
In Figure 2, we see the well-crafted document containing both the Microsoft and the recipient’s company logo. The document is detailed, listing a release date, release code and other specifics intended to make the document appear legitimate
Hovering over the “Apply Update” button, we see that this is steering the recipient to a Google Ad Services link that redirects to hxxps://ekavolunteers[.]org/.
The first part of the URL, googleadservices[.]com, is a reputable service that most organizations would not block. However, this is a common tactic many threat actors use to evade email filters and other security. They use legitimate links to mask redirects to malicious sites. By clicking on “Accept”, “More details about this?”, or ” Privacy Statement”, users are routed to hxxp://ekavolunteers[.]org. From there, another redirect sends users to the final phishing page that harvests credentials.
As seen in figure 3, the final redirect goes to the URL:
hxxp://microsoftofficeonlineservices.com[.]0-auth[.]live
On this page, users are presented with a Microsoft page with a pop up containing the “Updated Privacy Policy”.
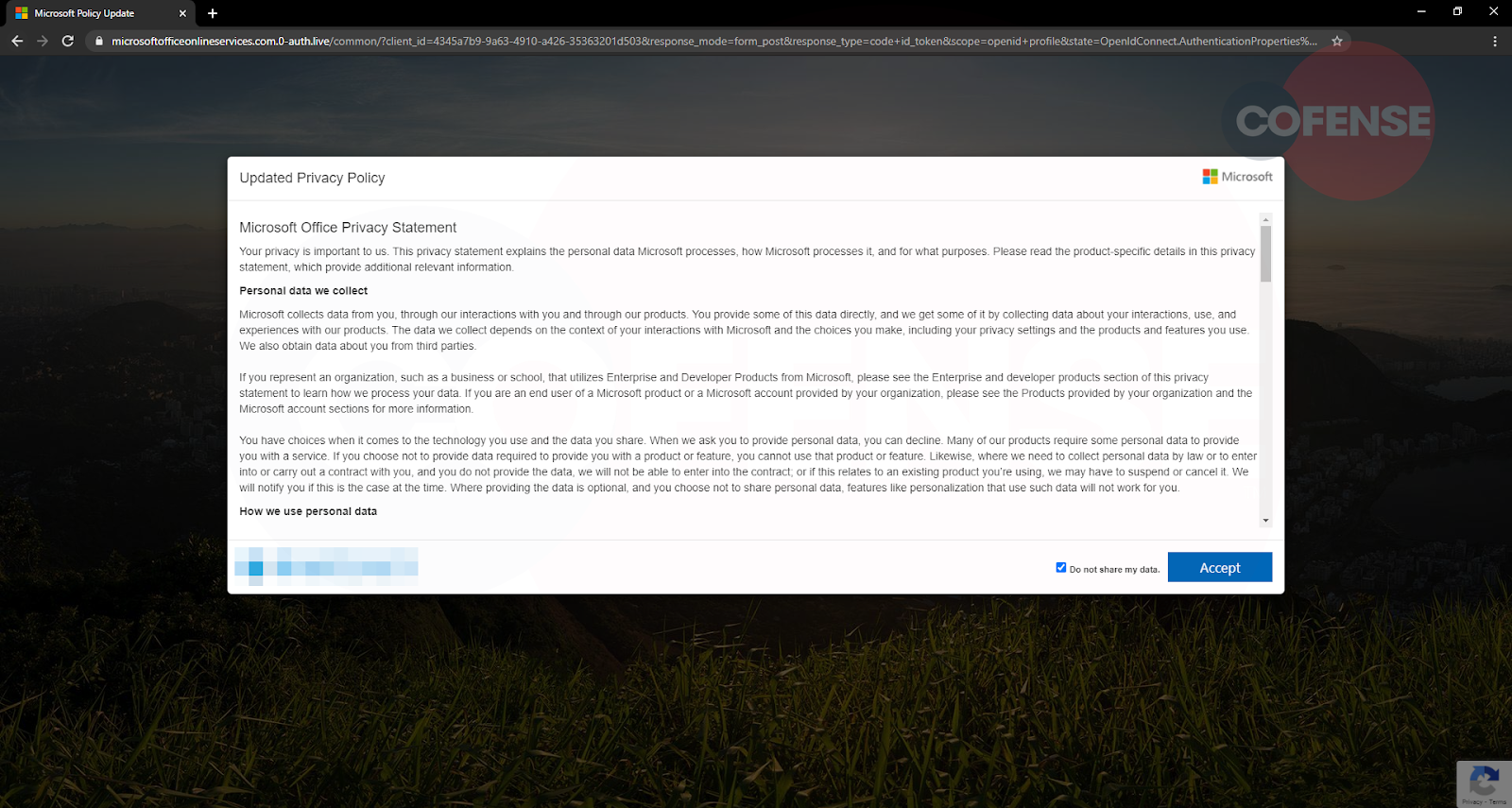 Figure 3: Phishing Page
Figure 3: Phishing Page
This page does appear to have Microsoft’s privacy policy listed along with the user’s company logo affixed at the bottom as a personalization lure.
Clicking the “Accept” button sends users to the final stage of this attack, as seen in Figures 4 and 5.
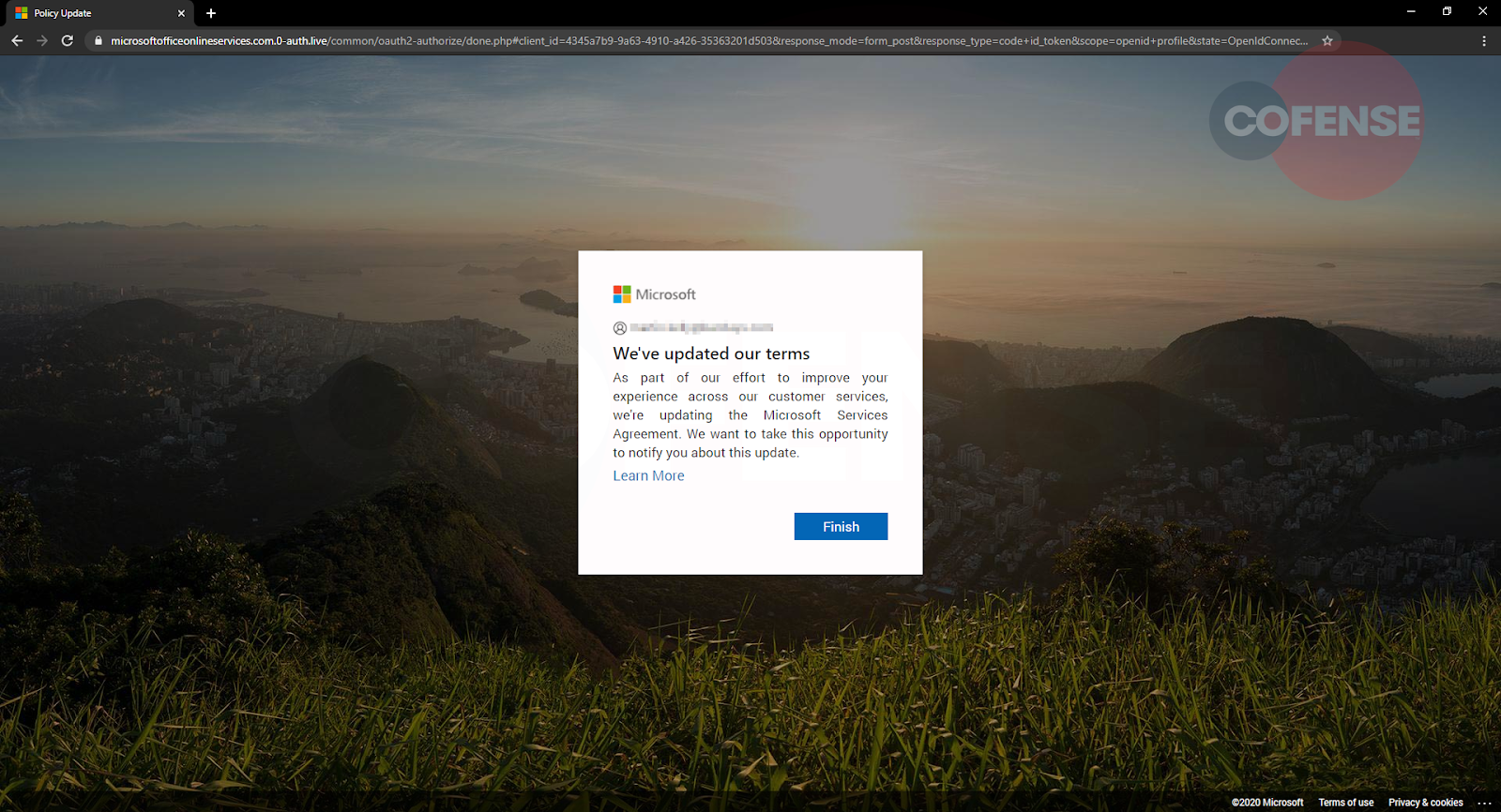
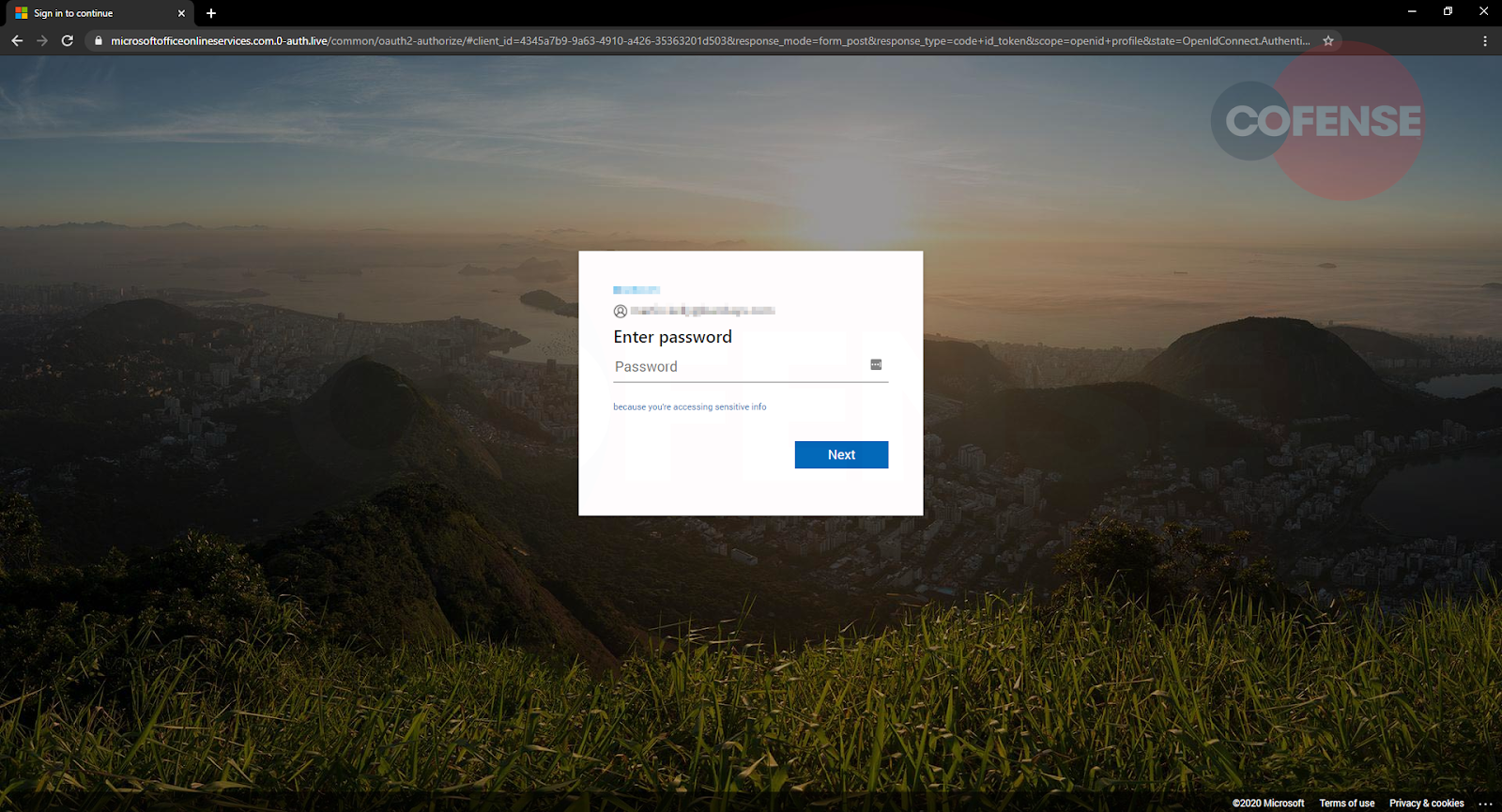
Figure 4-5: Phishing Page
Next, as shown in Figure 6, we see the login page where the user’s email address is auto-populated. Only the password remains to be provided.
After the users “log in,” they are presented with a statement advising “We’ve updated our terms” to impart a sense of logical sequence to the user’s actions. Once the “Finish” button is clicked, the user is redirected to the legitimate Microsoft Service Agreement page. This redirect is a common tactic intended to keep users in the dark, unaware that their credentials are now in the hands of cyber criminals.
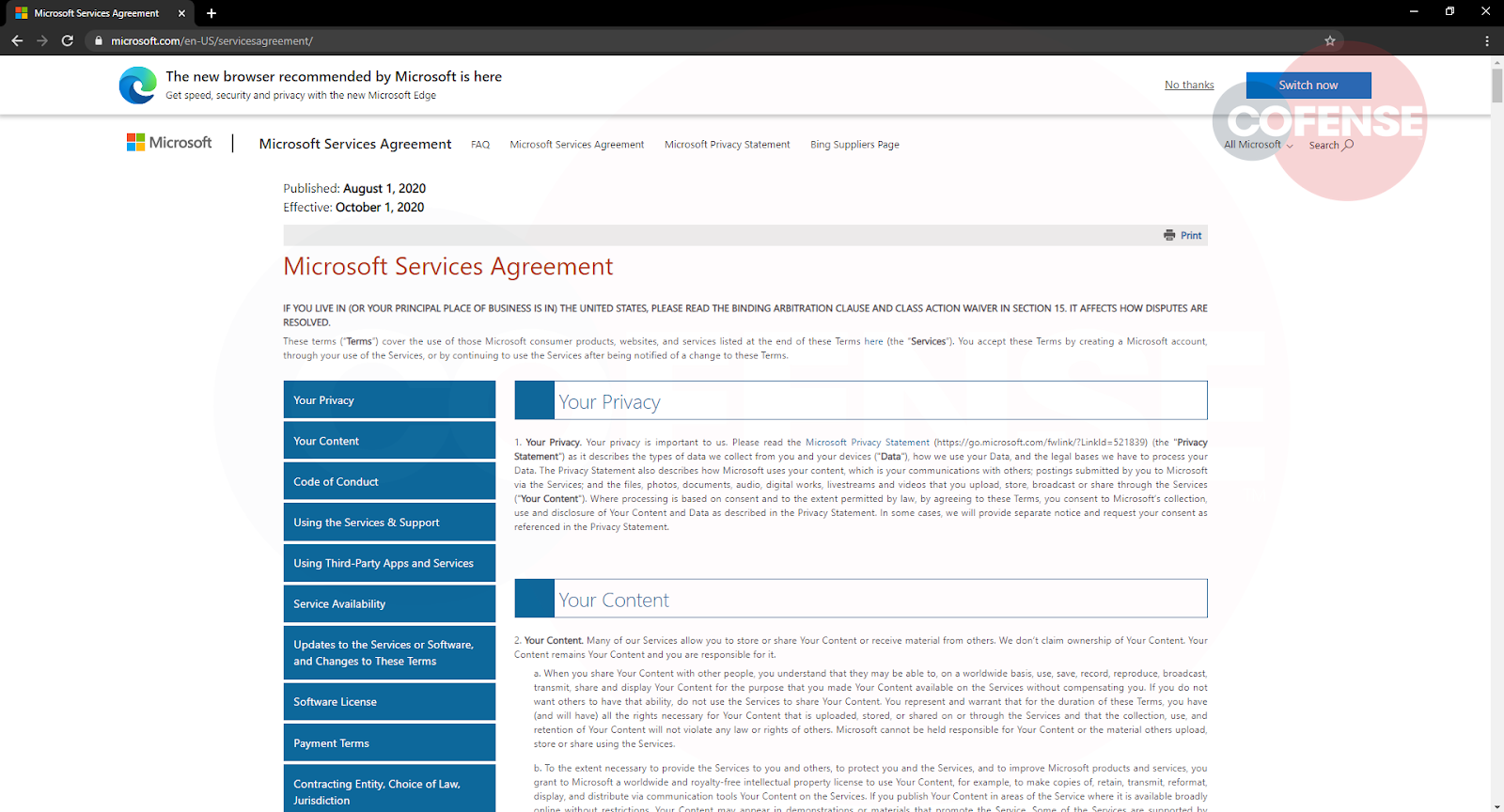 Figure 6: Final Redirect
Figure 6: Final Redirect
Campaigns like this can be headed off by conditioning users to spot threats and tactics designed to penetrate environments protected by secure email gateways (SEGs). This campaign illustrates how automated systems may fail without an additional layer of protection in the form of human sensors spotting and reporting suspicious emails that turn up in their inbox.
Cofense is uniquely positioned to stop phish. With Cofense Phishing Detection and Response, enterprises benefit from our complete view of real phishing threats. We can help you achieve zero breaches as a resulting of phishing emails. Contact us to find out how.
| Indicators of Compromise | IP |
| hXXps://www[.]googleadservices[.]com/pagead/aclk?sa=L&ai=CZCUrwkdiX puiJYCLmLAPouaG8A3Cwr-DXIfCkamHC7jaqcaoGBABIOaX1iVghIWAgNgdoAGE gOejA8gBCakCeFDgg656kT6oAwHIA8MEqgSbAk_QojPwDaxX9skc2uNHUM5 cIk8xTMe60h0f3nF1fQSxbiTIecJrlWTgXnp45S8NvTXncuqDQHdp5qRFRQflcgJ x7ZIXQZMZeSK7p3AO69bSV5qtGPNerAJHZZKMP71l78KB1Eg0SAfnftDSx UqQ9lwb_a4EUOykK9nbFDqswqTxE-S6AcqATWfvzjYd_5g2VydvIgw 5CDpok1CROXdqxd_0wNmtaNdN 5QhQGAGUsScZ8BgXQMBf62o81xBt_ITEUHxrBp5eLFRMC2BUJQ48Q h_B3eg9oCngoSnm9AvlbERNsUT5Wq8rI8tQs1cNzeKTGGiyarfmdYZMWy5S6H-vEe59kvyP96os9y9HLIGkX7myuV_DOzwUp7DjABJjT0ebfAqAGLoAH5P-YXKgHjs4bqAfVyRuoB5PYG6gHn9sbqAe6BqgH8tkbqAemvhuoB-zVG6gH89EbqAfs1RuoB8LaG9gHANIIBwiAYRABGADyCA1iaWRkZ XItNTQ1NzU2sQkc-aFWmboITIAKBJgLAcgLAQ&ae=1&num=1&pr =10:0.865137&cid=CAASEuRoBo-RPe6zJ1BGgrMR1MGsgQ&sig=AO D64_3WRWwBdf88-GXuezW4Nbs_nTshPQ&client=ca-pub-3076890012741467&nb=19&adurl=https://ekavolunteers.org/@ | 172[.]217[.]13[.]226 172[.]67[.]134[.]22 |
| hXXps://ekavolunteers[.]org/@ | 104[.]21[.]5[.]251
|
hXXps://microsoftofficeonlineservices[.]com[.]0-auth[.]live/common/oauth2-authorize/
| 23[.]94[.]70[.]100
|
All third-party trademarks referenced by Cofense whether in logo form, name form or product form, or otherwise, remain the property of their respective holders, and use of these trademarks in no way indicates any relationship between Cofense and the holders of the trademarks. Any observations contained in this blog regarding circumvention of end point protections are based on observations at a point in time based on a specific set of system configurations. Subsequent updates or different configurations may be effective at stopping these or similar threats. Past performance is not indicative of future results.
The Cofense® and PhishMe® names and logos, as well as any other Cofense product or service names or logos displayed on this blog are registered trademarks or trademarks of Cofense Inc.


