Adding another entry to the ever-growing list of encryption ransomware, the Jaff Ransomware made its debut onto the threat landscape with large sets of phishing emails on May 11, 2017 – one day before the sensational impact of the WannaCry ransomware attack. However, the risks posed by the Jaff ransomware should not be overlooked. This, too, is a robust ransomware that leverages some of the most prolifically-used delivery mechanisms in phishing email and embodies characteristics associated with other very successful malware.
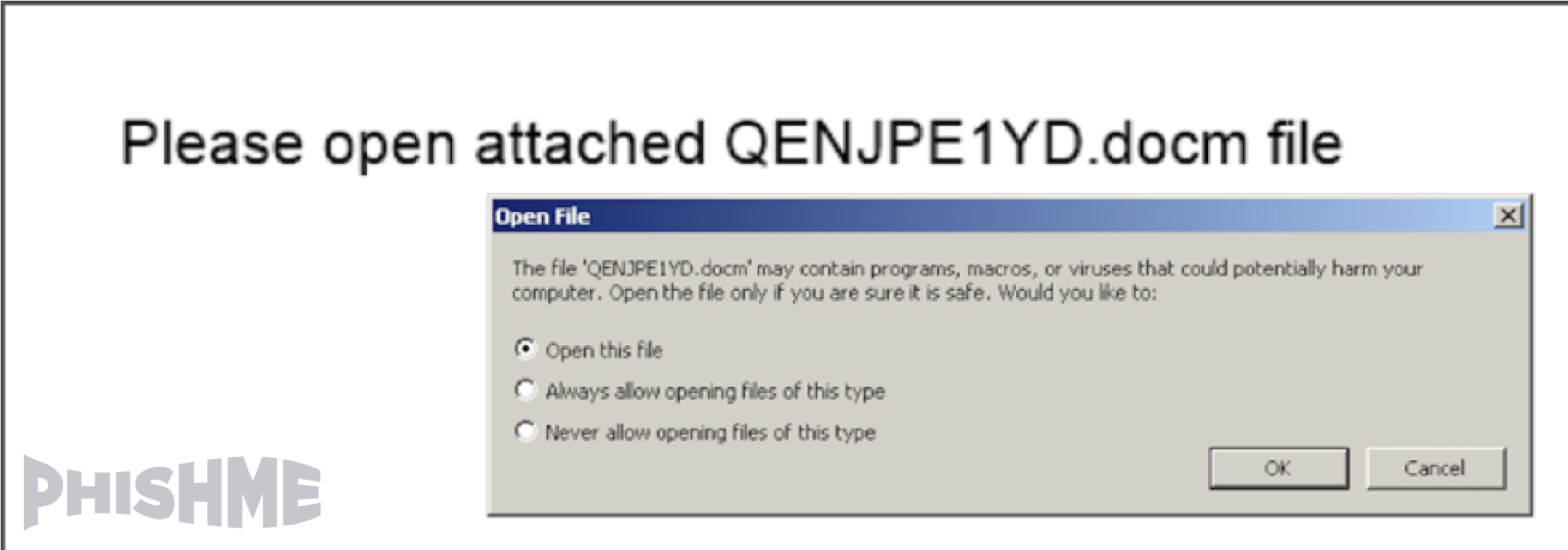
While Jaff may not have garnered the attention of WannaCry, the techniques used in its distribution put it in an exclusive club whose recent membership has included both Dridex and the Locky encryption ransomware. Like the most recent Locky and Dridex distributions, this ransomware was delivered by Microsoft Word documents containing macro scripting that were in turn delivered as an embed in PDFs attached phishing emails.
The phishing emails used to deliver the Jaff Ransomware used various subject lines implying that a receipt, scanned document, or report was attached to the email. Some phishing emails included a brief note instructing the victim to “print 2 copies” while many did not. In every case, the victim was given an attached PDF document that contained a Word document designed to deliver the Jaff ransomware.

Jaff adds another entry to the long and growing list of ransomware varieties that are attempting to carve out their share of this lucrative criminal market. Upon completing its encryption process, Jaff creates a set of “ReadMe” files with instructions on how to access the payment interface via the threat actor’s Tor-hosted web application.
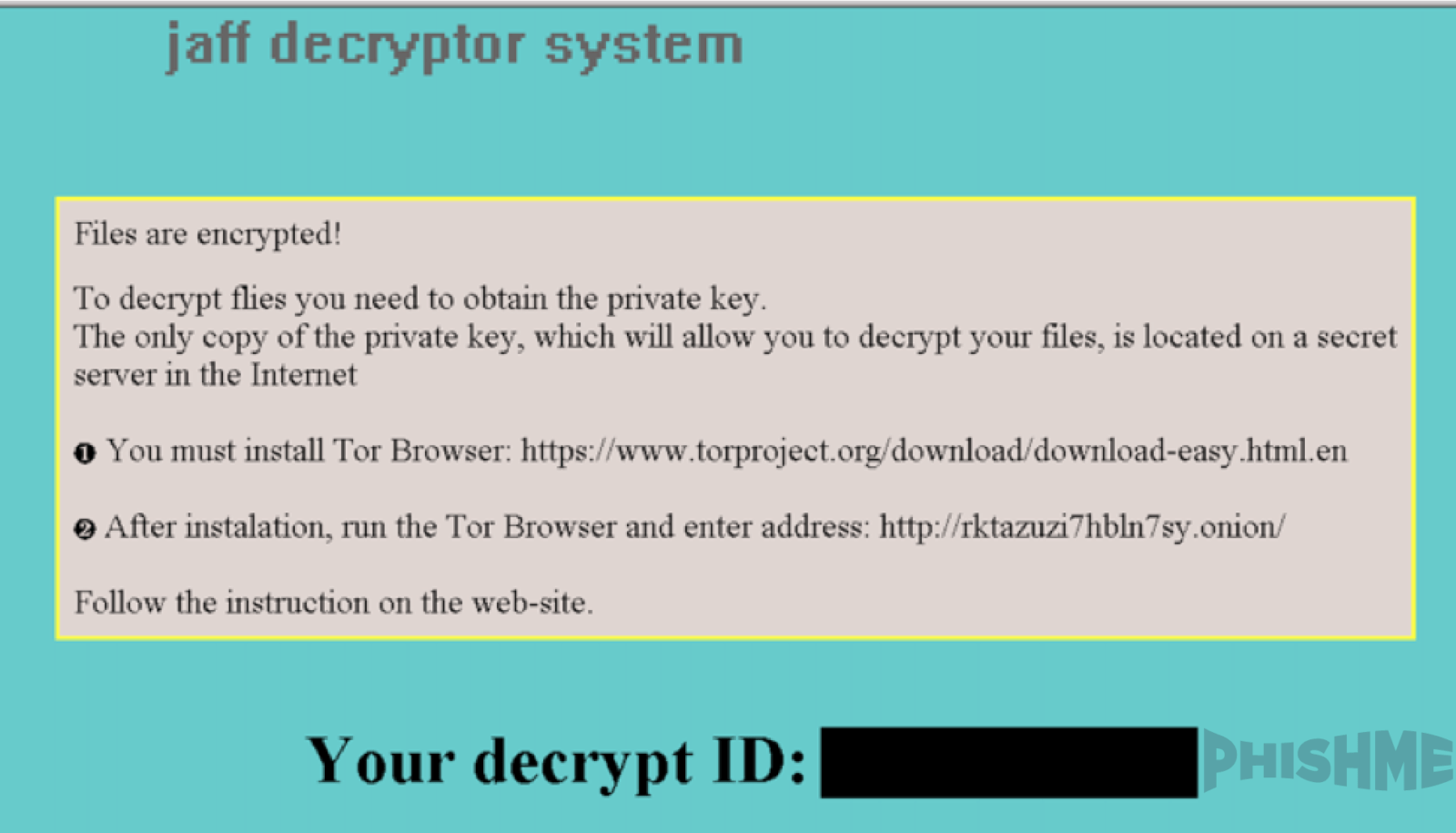
The payment interface presented to victims shares a common color scheme and overall layout with that of the Locky encryption ransomware. This demonstrates that the developers of the Jaff payment interface are likely familiar with and were inspired by Locky. Borrowing aspects of Locky’s methodology seems like a logical choice for ransomware developers since that ransomware enjoyed wild success throughout 2016 and revolutionized the ransomware business model at scale. Between this payment interface and the delivery technique selected for its initial distribution, Jaff is clearly attempting to share in Locky’s successes.
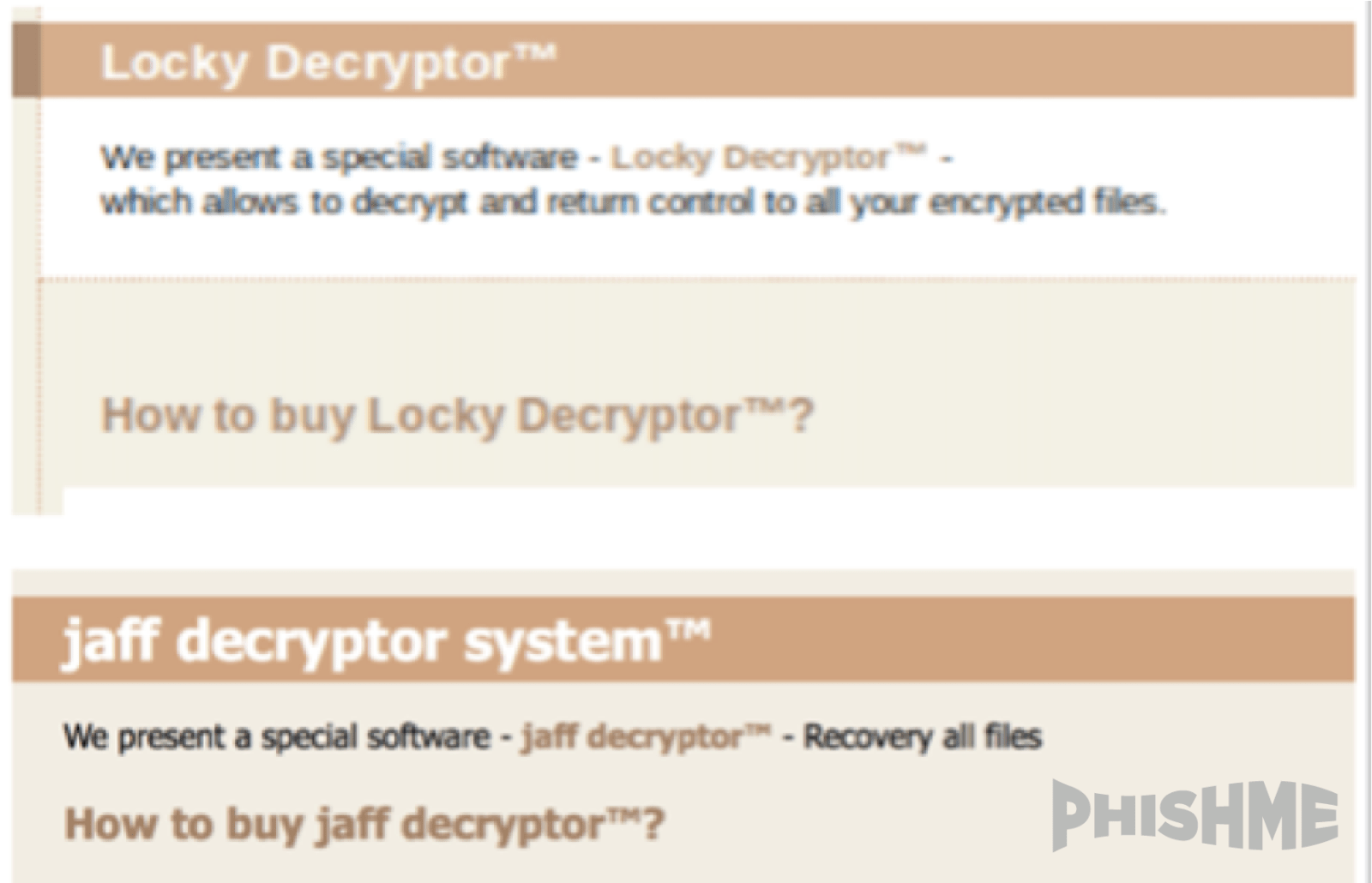
However clever Jaff’s delivery technique may be, it is still a rehash of a successful one that has been played out recently. In April 2017, Locky made a brief, yet bold resurgence using a creative delivery technique that took advantage of enterprise reliance on both the PDF and Microsoft office suite. As has been heavy-handed solutions like blocking or restricting the transport of these documents inhibits enterprises’ ability to conduct normal business. Threat actors therefore hope to secure the delivery of both PDF and Office documents so they can leverage their social engineering content to convince potential victims to open the door to the attacker’s tools.
However, this set of tactics, techniques, and procedures is now well-documented and should be part of the corpus of known threat actor methodologies for organizations. This is a crucial part of implementing a holistic phishing defense strategy. Based on knowledge that attacks like these occur, professionals tasked with defending an enterprise can very nearly anticipate the threat actors’ next moves. This anticipation can take place at three primary stages:
- Empowered users can be prepared to think critically when phishing emails arrive. Rather than playing into the threat actor’s strategy, they can recognize the techniques and report those messages to security professionals and incident responders.
- Defenders can, in turn, automate the processing of these reports and gain additional insight into which techniques are being used against their organization by leveraging robust response tools tuned to identify relevant attack vectors. This tuning can be done through the judicious application of actionable and timely threat intelligence reporting that captures not only the infrastructure but also the methodology used by threat actors.
- With these reports and categorization in hand, security professionals can appropriately expedite their response to minimize the threat actors chance at success.
The Jaff ransomware attempts to take advantage of a tried-and-true technique for securing infections. However, the WannaCry ransomware attacks of May 12 might push threat actors to innovate and step beyond their existing tactics and procedures. Jaff is a new ransomware, ready for release but there is no reason to expect its users wouldn’t seize the opportunity to learn from the lessons of WannaCry to take their tools to a new level of virulence and tenacity. This specific email template is available in PhishMe Simulator™ to use in your own scenarios.
Never miss another threat – stay on top of emerging phishing and malware threats and attacks, all delivered straight to your inbox completely free. Subscribe to PhishMe Threat Alerts today.


