By Adam Martin, Cofense Phishing Defense Center
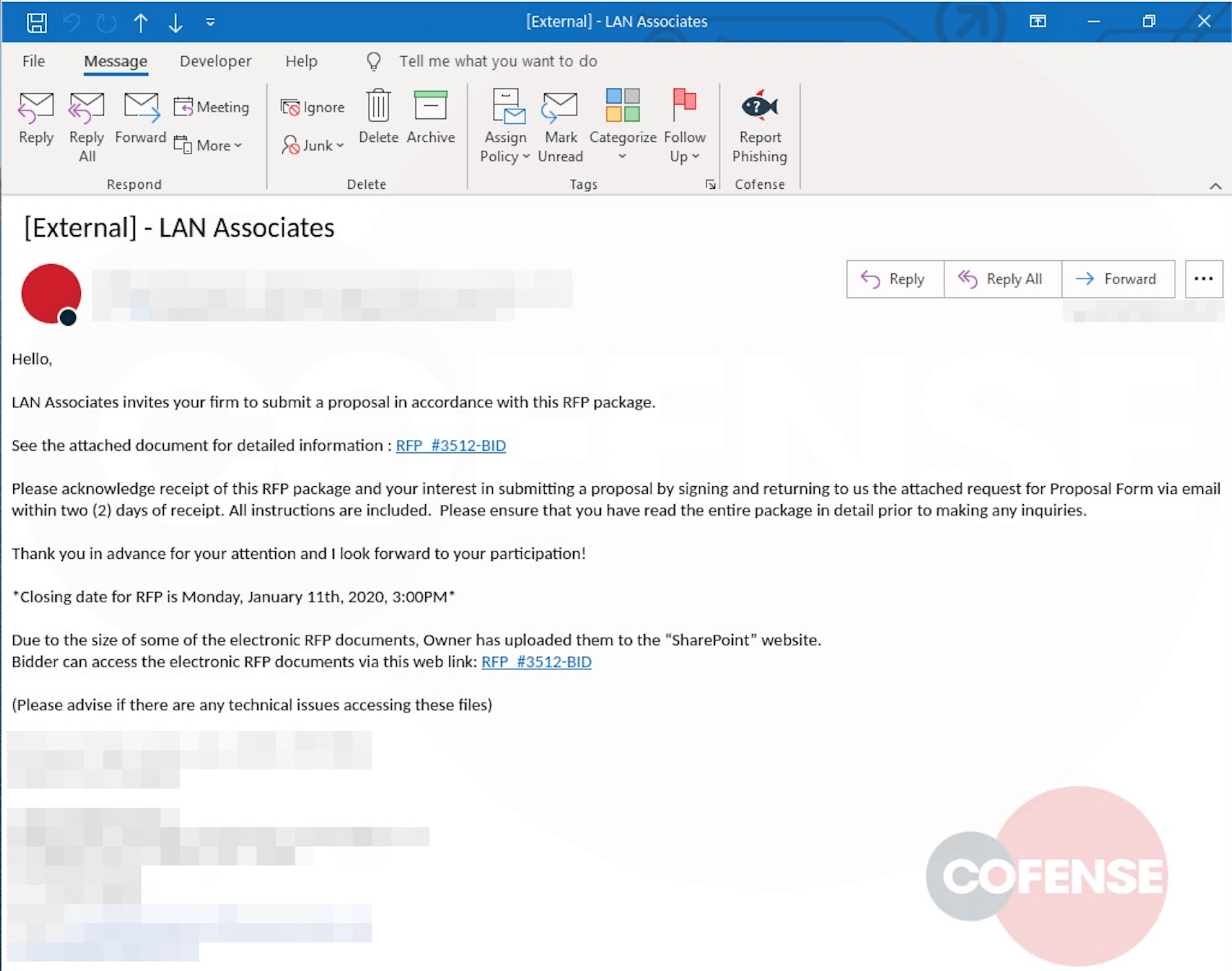
As threat actors phish for credentials, they continue to send emails in alignment with organizational business processes, such as demands for signatures or approvals for “sensitive” documents. A trend recently found by the Cofense Phishing Defense Center (PDC) team is a pre-set deadline for access to the given sensitive information. This represents a two-pronged approach to phishing. Element one is trust. Suspicions would be lowered because one would assume a threat actor would want the material accessible for as long as possible. Element two is urgency, given the deadline for viewing. Both aspects are illustrated in Figure 1.
Figure 1
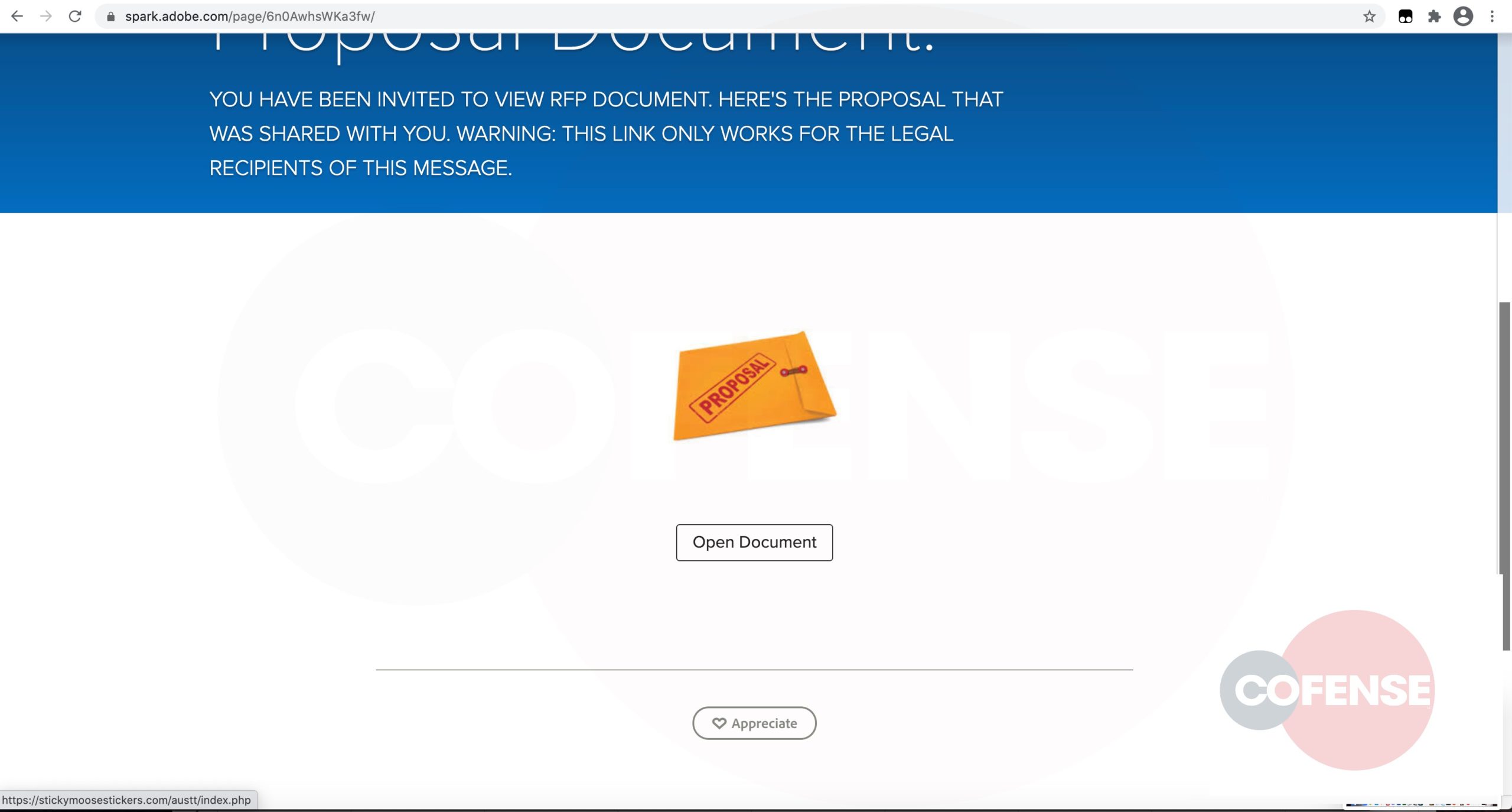
Once the provided URL is accessed, the following page is displayed. The first stage to this credential phish is a sham SharePoint page. As can be seen from the address bar, the webpage is hosted by another vendor.
Figure 2
Further down on the same landing page, an image of an envelope labeled “proposal” is seen. Another confidence-inspiring message is also found; it bears some semblance of legal legitimacy.
Figure 3
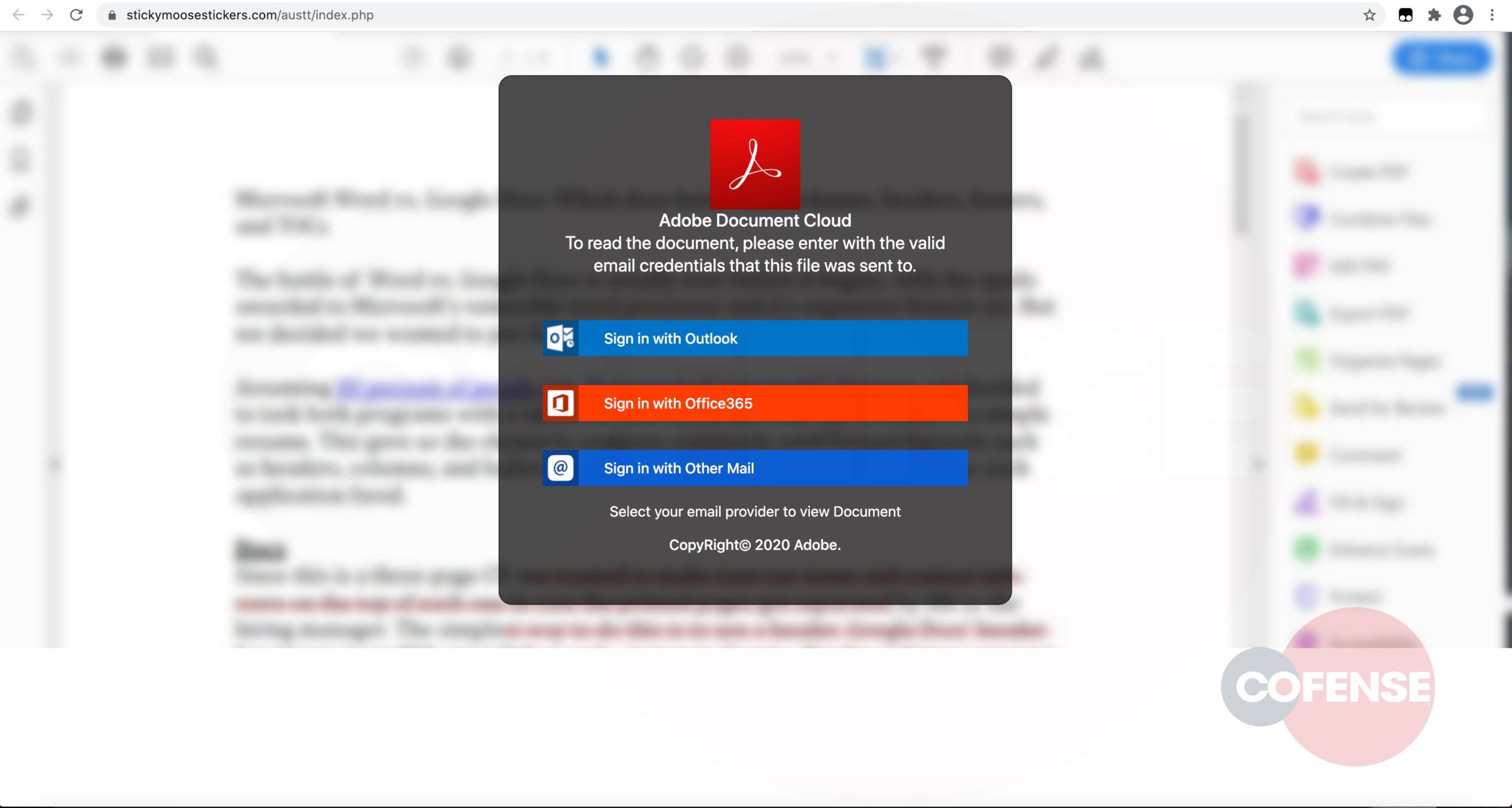
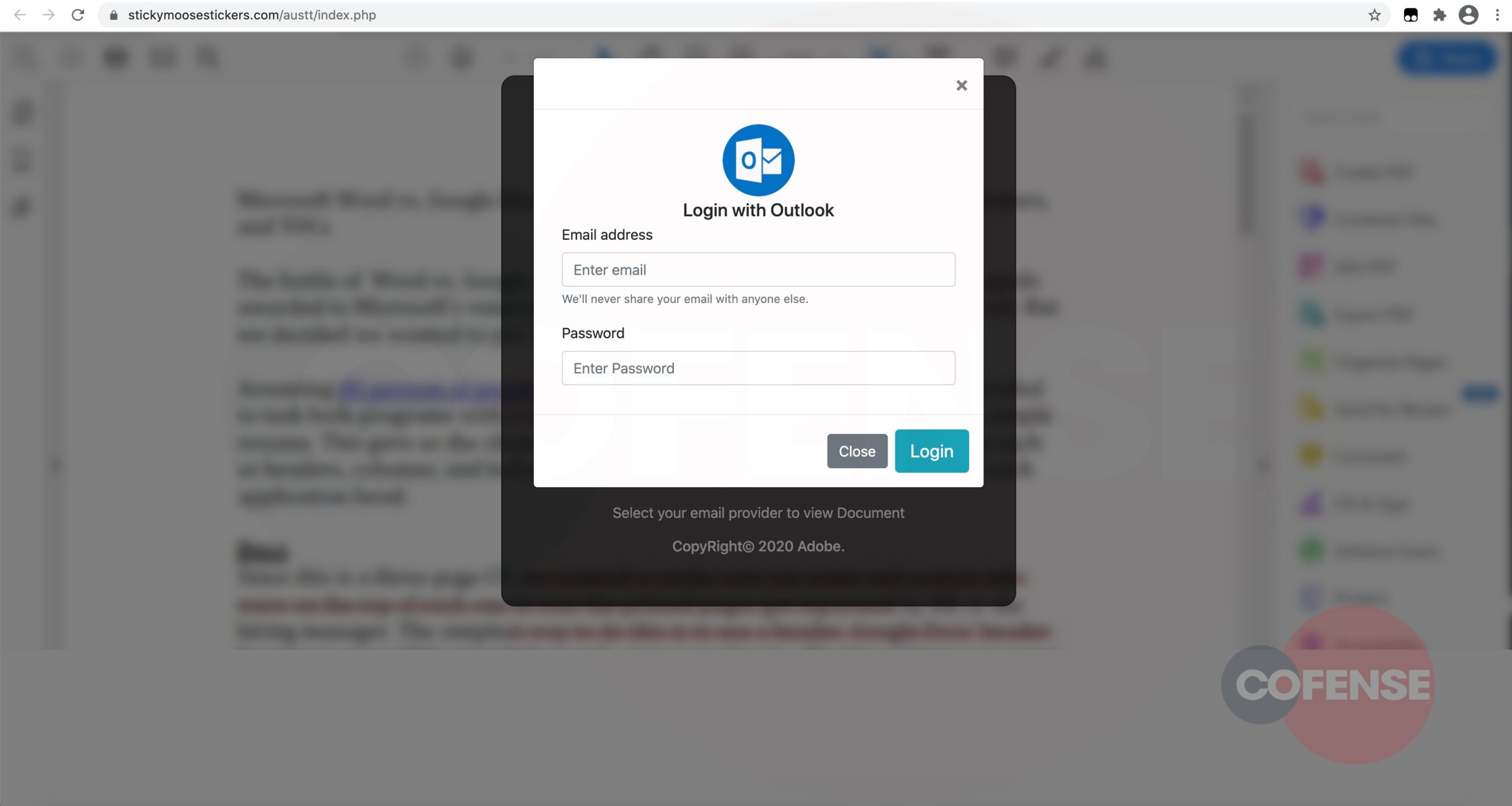
Upon accessing the link to the seemingly legally–protected document, a common tactic is employed whereby the threat actor allows the recipient to choose their email provider. This is complemented by blurred content possibly to up the temptation to access the obscured information. The base URL changes to one that has little to do with the sending company or any legitimate email provider.
Figure 4
Once the login credentials are entered, they are exfiltrated to an external server.
Figure 5
Indicators of Compromise
| hXXps://spark[.]adobe[.]com/page/6n0AwhsWKa3fw/ | 13[.]32 [.] 204 [.] 55 13 [.] 32 [.] 204 [.] 80 13 [.] 32 [.] 204 [.] 53 13 [.] 32 [.] 204 [.] 46 |
| hXXps://stickymoosestickers[.]com/austt/index.php | 199 [.] 250 [.] 201 [.] 182 |