It is interesting how paths sometimes overlap and/or converge.
In this instance, we ended up with a reported smish (an SMS-based phish). While SMS Phishing is something that is covered within Cofense’s Security Awareness training modules, it is not something that we see reported that often.
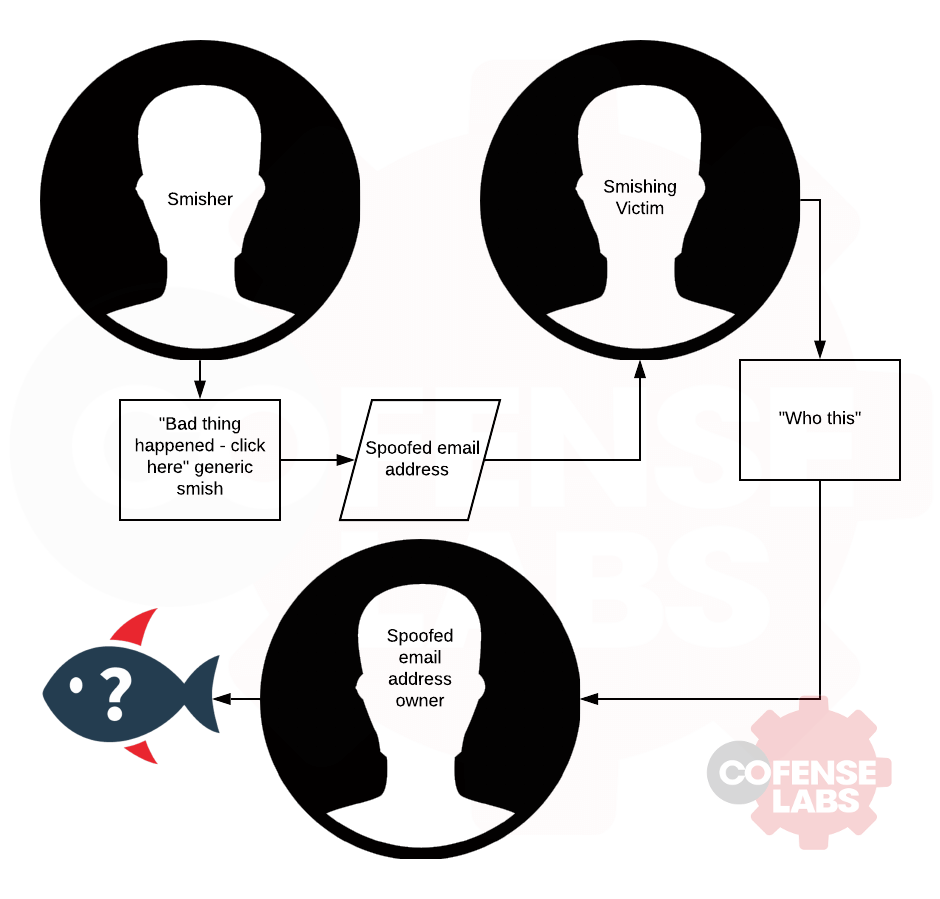
What makes this specific situation interesting is that the SMS phish was reported by the person whose email address was originally spoofed as the original sender, because the person who received it replied!
I feel like this requires a flowchart:
Smish Flowchart
What is Smishing?
Smishing is a form of phishing that targets mobile phone users through text messages. In these scenarios, the attacker tricks users into sharing personal information or downloading malicious software by pretending to be a trusted source. With the increase in smartphone usage, smishing attacks have become more frequent and sophisticated. Due to the immediate and intimate nature of text messages, recipients may feel a sense of urgency when encountering a smishing attempt. Remain cautious when receiving unsolicited text messages and never share personal information or click on links unless you are confident you trust the sender.
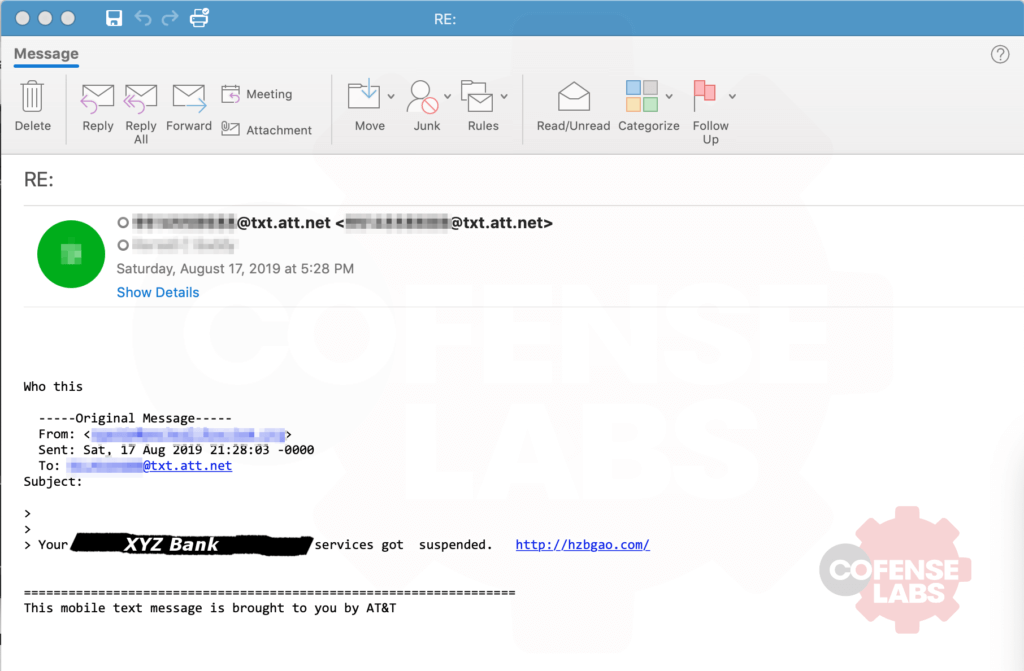
For those who do not already know, phones can receive text (SMS) and multimedia messages (MMS) via email through most carriers, and conversely depending on the carrier you can send an email to someone as a SMS or MMS. A reply to such a message most often results in an email response to the sender. Such is the case with this email, except the sender it replied to was not who actually sent the text via email. Here is the resulting email we received after the customer reported it to us.
To be fair, this wasn’t a completely generic and poorly planned smish – the ‘hzbgao’ page it points to redirects to the page which has an invalid certificate and appears to otherwise be down, however both the smish and the redirected domain are impersonating the same company, so it looks like at least a small amount of effort was put in to it. Based on the smish and the link, we can strongly assume that the resulting webpage would have been an attempt to steal the victim’s login credentials.
My hat goes off to the anonymous recipient of the phish though, with their “Who this” response. All incoming emails should be regarded in much the same way as incoming phone calls and text messages from random people and numbers.
All third-party trademarks referenced by Cofense whether in logo form, name form or product form, or otherwise, remain the property of their respective holders, and use of these trademarks in no way indicates any relationship between Cofense and the holders of the trademarks.