Since this April, Cofense Intelligence™ has observed a sustained increase in the financially motivated targeting of United Kingdom-based users with phishing lures imitating brands like Her Majesty’s Revenue & Customs (HMRC), Lloyds Bank, and HSBC Bank. The most common final payloads delivered by these campaigns are designed to compromise victims’ financial accounts and provide illicit access to financial information. This surge in targeting almost certainly represents a stage in the “whack-a-mole” strategy long employed by threat actors: expand campaigns against a segment of the vast vulnerable attack surface until those users catch on to the threat, then move to the next target.
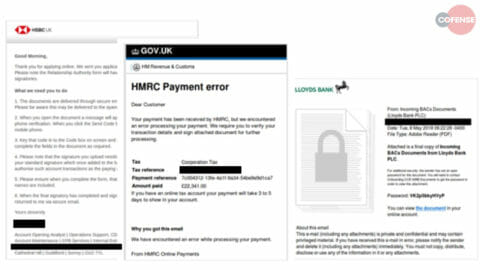
Figure 1: Examples of Phishing Lures Imitating Communications from HSBC, HMRC, and Lloyds Bank
The appearance of authenticity of the phishing emails differs among the campaigns, indicating that different groups of threat actors are likely leveraging these high-profile brands to target UK users. Almost all the emails reference supposed payments, financial advice, or account information—often for corporate accounts. However, some of the emails and campaigns demonstrate greater skill and enhanced social engineering techniques. Several emails include supposed passwords or unique identifier numbers for attachment or account access. Multiple emails were crafted with such gall that in an effort to look more credible, they included security tips like warnings against opening suspicious attachments.
Figure 2: Threat Actors Attempt to Establish Credibility with “Security Tips”
Different Malware, Same Goal
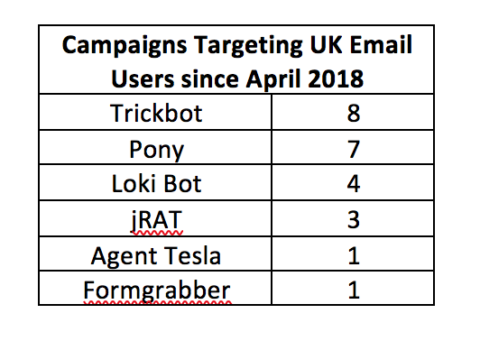
Trickbot, Pony, and Loki Bot comprised the majority of final payloads delivered in the distinct campaigns analyzed by Cofense Intelligence since April. Our readers will know that Trickbot—a banking malware that targets multiple financial institutions—has been a popular evolving feature of the phishing threat landscape over the last year, with an ever-growing suite of plugins that expands its capabilities. Pony and Loki Bot are more basic, off-the-shelf, stealer malware families that target credentials saved on multiple applications and exfiltrate cryptocurrency wallet information and password safe data.
In spite of the ostensible differences, these types of malware are almost certainly leveraged for similar objectives—to provide threat actors with financial information and access to accounts to facilitate theft. Analysis of the malware itself reveals targeting beyond accounts directly related to HMRC, HSBC, and Lloyds. For example, in a recent phishing campaign imitating HMRC, the deployed Trickbot malware contained webinjects for several prominent UK financial institution websites, as well as popular digital currency exchanges like coinbase[.]com and blockchain[.]info. The intent is to use a phishing lure that is likely to seem relevant to the target, and then gain access to as many accounts and as much financial information as possible for theft and exploitation.
What is Next?
As this target audience becomes oversaturated, increasingly aware, and appropriately responsive to the threat, these financially motivated actors will inevitably expand their focus to less prepared demographics. In order to cast the widest net, they will look to imitate the most relevant organizations and groups for the targeted region, like prominent regional financial institutions.
Threat actors constantly aim to find the sweet spot between crafting a message well-honed enough to appear legitimate to the target and reaching the maximum number of victims possible. We frequently see extremely generic phishing lures—ones that would appear suspicious to users with even the most rudimentary of phishing awareness. By crafting messages to imitate the target region’s most popular financial institutions and agencies, adversaries can more likely reach both objectives. The more actors tailor phishing emails to specific demographics, the more convincing those messages become—and the more critical effective phishing awareness and education programs become to network protection.
For a look back and a look forward at phishing and malware threats, read the 2018 Cofense™ Malware Review.
** For more details, see Threat IDs 11231, 11248, 11312, 11324, 11340, 11349, 11453, 11461, 11476, 11496, 11509, 11510, 11547, 11565, 11655, 11680, 11710, 11821, 11862, 11877, 11912, 11953, 11954, and 11968.
All third-party trademarks referenced by Cofense whether in logo form, name form or product form, or otherwise, remain the property of their respective holders, and use of these trademarks in no way indicates any relationship between Cofense and the holders of the trademarks.