SEGs Bypassed: Microsoft, Trend Micro, IronPort
By Shirish Lavania, Cofense Phishing Defense Center
In today’s world, each and every organization use email security to secure their infrastructure as email is a common entry point for attackers used for spreading phishing attacks, malwares and other types of threats. To this end, adversaries are continuously trying to bypass secure email gateways to carry out their attacks. Threat actors often disguise harmful URLs within HTML attachments, which makes it more challenging for Secure Email gateways (SEGs) to block them. The Phishing Defence Centre (PDC) analysed a phishing campaign impersonating email security provider to lure recipients into providing their user credentials via malicious HTML attachment.
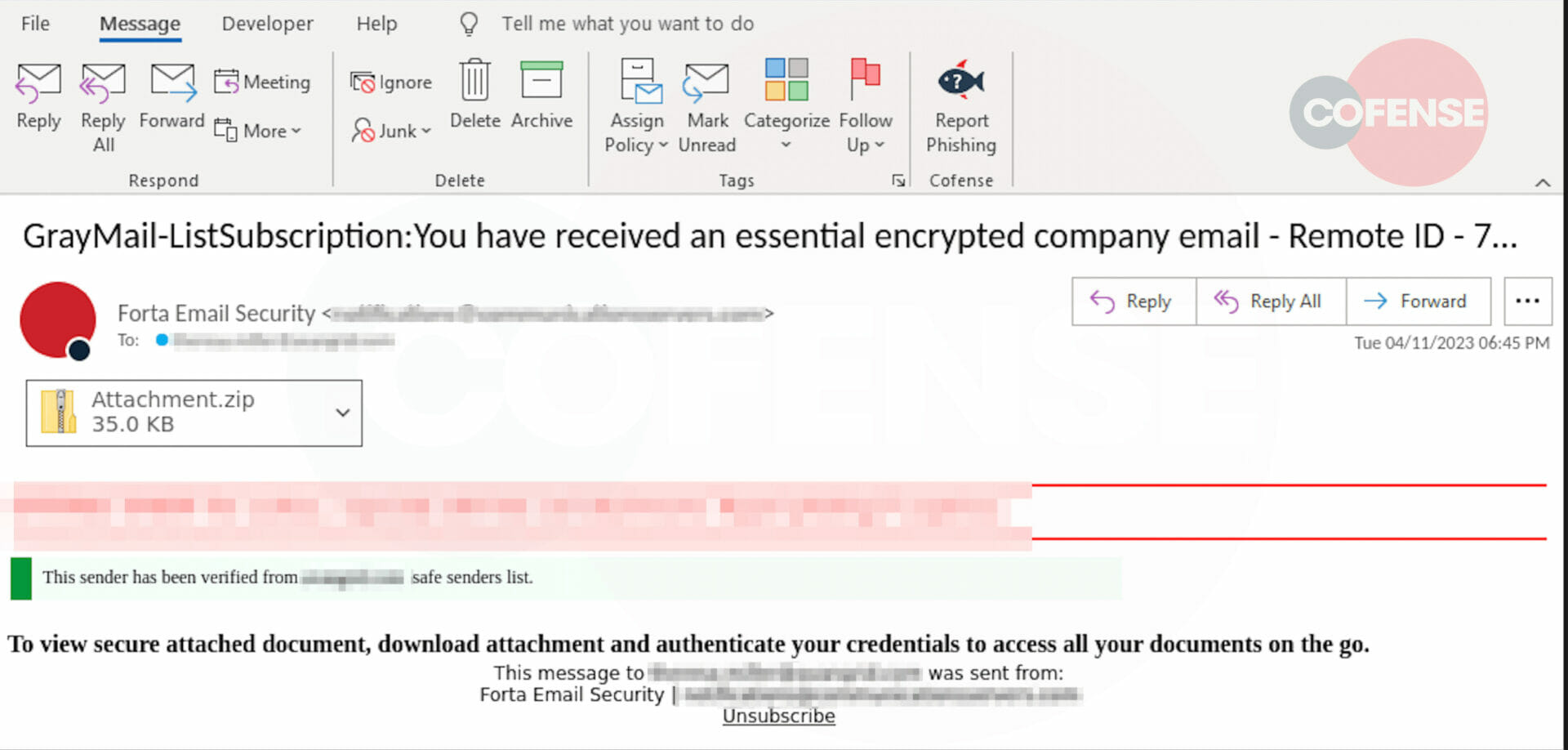
Figure 1: Email Body
Figure 1 shows the user received an email from Forta, which is likely a misspelling of Fortra. The subject mentions an “essential encrypted company email” and a fake green banner states that the “sender is verified”, in an attempt from the sender to trick the user to click on the attachment. The email instructs the user authenticate with credentials in order to view the secure attached document.
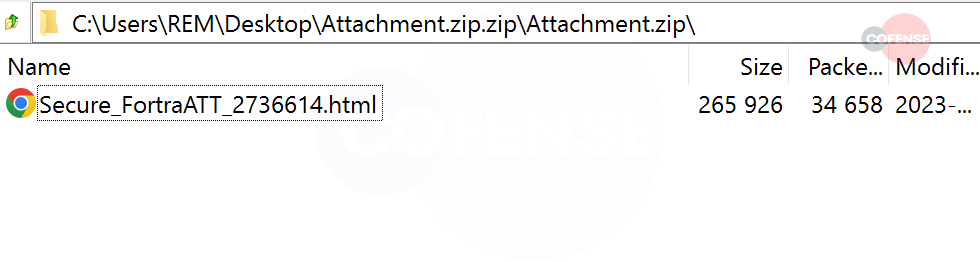
Figure 2: HTML File
The attachment in the email shows that the adversaries wanted to make it look legitimate by naming the html as “Secure_FortraATT_2736614.html” which is inside the “Attachment.zip” folder as seen in figure 2.
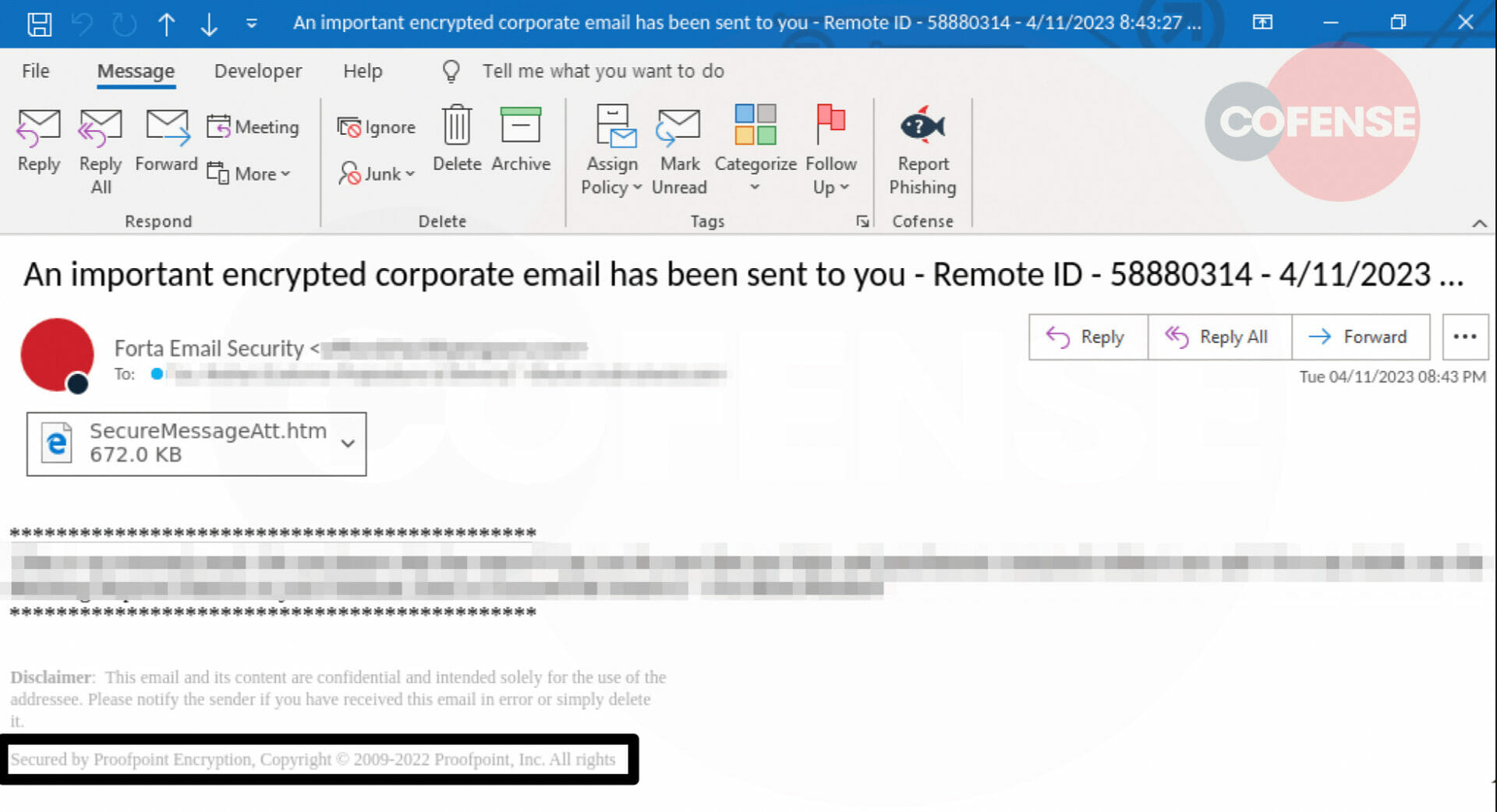
Figure 3: Email Body
In Figure 3 we see a similarly styled email that shows Fortra as the sender but makes mention of Proofpoint. The attacker tried to create a false sense of security to convince the user by including the footer “Secured by Proofpoint encryption”.
It is not uncommon for threat actors to use impersonation tactics in order to trick users into believing that an email is genuine.
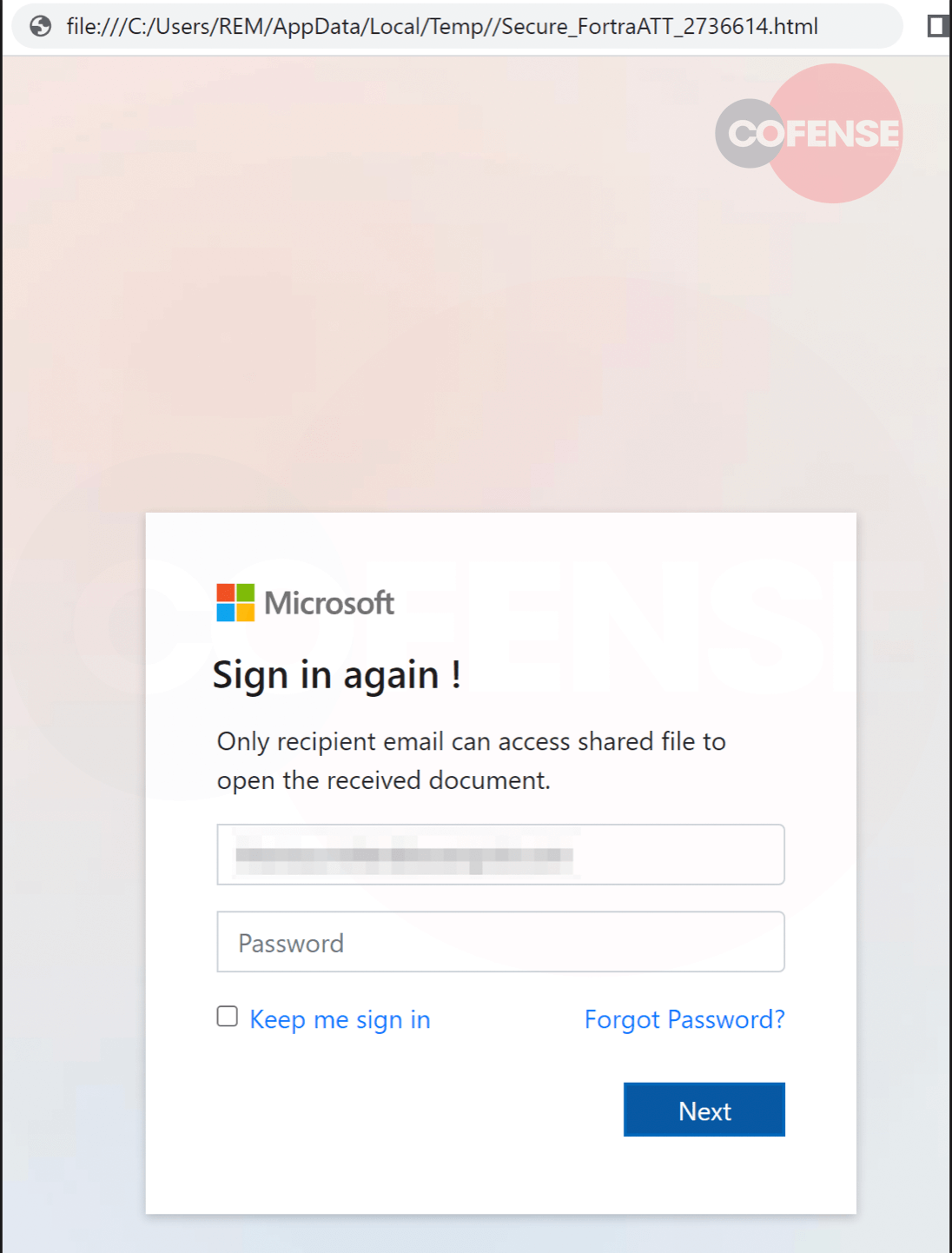
Once the user clicks on the attachment, it presents a spoofed Microsoft login page with a Microsoft logo on it to make it more familiar to the user as seen in figure 4.
Figure 4: Fake Microsoft Landing Page
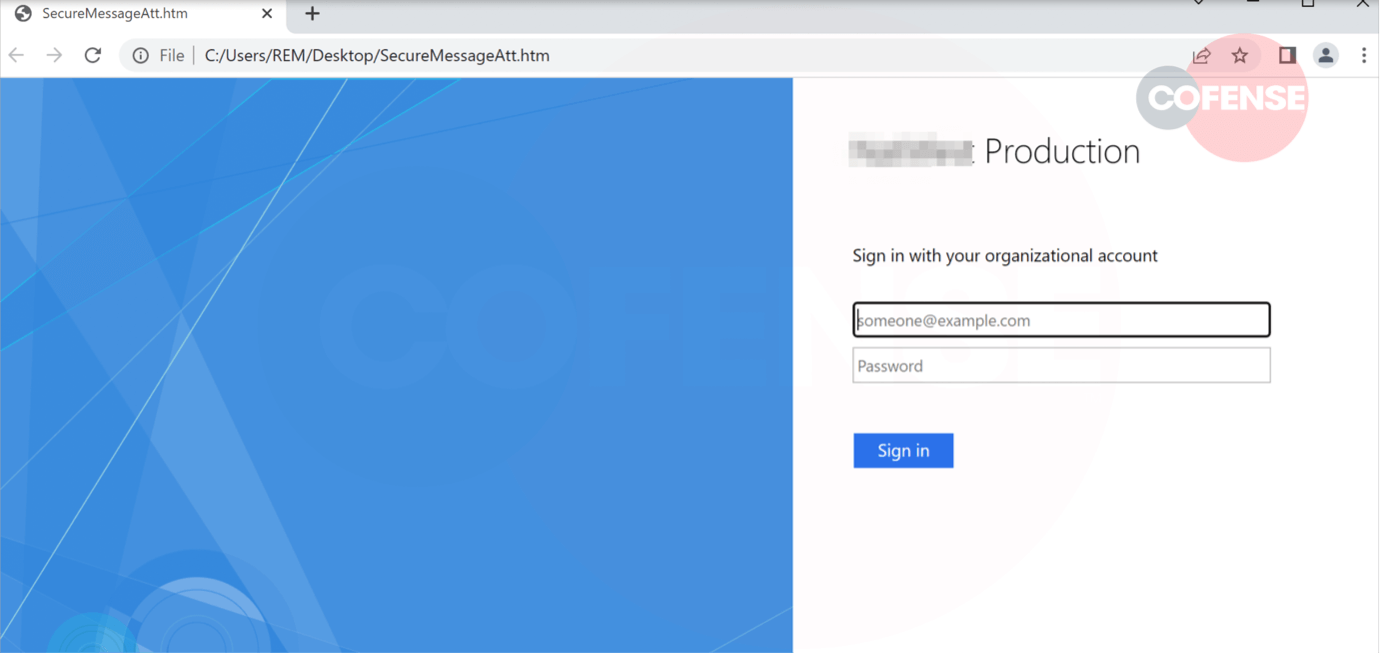
In figure 5, the threat actor styled the spoofed page as if it was a production login page.
Figure 5: Fake Production Login Page
Once the users login, the credentials are exfiltrated to the malicious URLs hxxps://office[.]topexecs[.]info/ for figure 4 and hxxps//library-query[.]info/login[.]php for figure 5.
This campaign unveils that the attackers are constantly improving their techniques to lure users and bypass security measures in order to steal useful information. Unfortunately, security solutions such as SEGs may not always be effective in stopping attachment threats and users end up opening them. An attentive user with the help of Cofense Reporter alerted us about this campaign upon realizing that this phishing email is asking for sensitive information.
| Indicators of Compromise | IP |
|---|---|
| hxxps//library-query[.]info/login[.]php | 138.201.134.162 |
| hxxps://office[.]topexecs[.]info/ | 84.247.51.110 74.119.239.234 |