Update 2016-11-11:
It is important to PhishMe to avoid hyperbolic conclusions whenever possible. In the interest of clarifying some conclusions that have been drawn from this blog post, it is important to keep in mind the nature of Locky distribution and how this malware is delivered to victims. We consider it a serious responsibility to report on very real threats in a way that lends itself to our credibility as well that the credibility of all information security professionals.
PhishMe has no reason to believe that this set of emails was delivered only to victims of the OPM incident nor to government employees as part of a spear phishing attack.
The email addresses associated with the OPM breach have not been actively circulated. As such, it is incredibly unlikely that the threat actors have any detailed knowledge of who will be receiving these emails. Furthermore, PhishMe has not received any confirmation that anyone impacted by the OPM incident has received a copy of these emails. Many people who were not affected by the OPM incident and are not affiliated with the U.S. government also received copies of these messages and are also put at a very real risk by this ransomware.
***
A continuing truth about the Locky encryption ransomware is that its users will take advantage of any avenue that they believe will secure them a higher infection rate but still utilize predictable themes. This time, the threat actors have chosen to impersonate the US Office of Personnel Management in one of their latest attempts to infect people with this ransomware. As we have noted in previous reporting, Locky has set the tone for 2016 with its outstanding success as an encryption ransomware utility. As we approach the end of the year, this ransomware continues to be a fixture on the phishing threat landscape.
One key example of this malware’s phishing narratives is a set of emails analyzed by PhishMe Intelligence this morning that cite the purported detection of “suspicious movements” in the victim’s bank account that were detected by the US Office of Personnel Management.
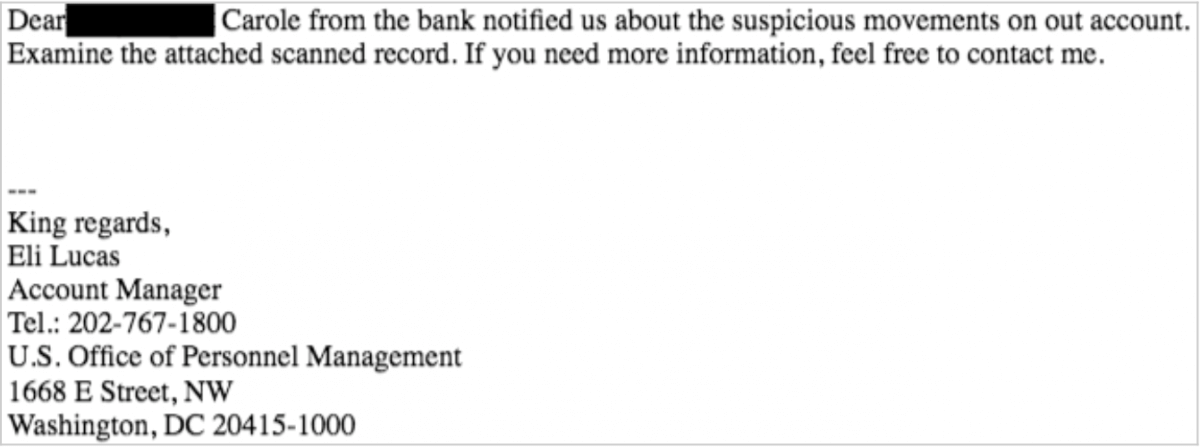
The ZIP archives attached to these messages contains a hostile JavaScript application used to download and run a sample of the Locky encryption ransomware.
This phishing narrative comes with a few notable implications. First, emails that are designed to appear as if they were sent by the OPM and the threat actors hope that these are more likely to appeal to government workers and employees of government contractors. Secondly, the threat actors may also how that these messages are also more likely to appeal to individuals who have been subject to a loss of personal information as a result of the high-profile OPM breach.
If either of these implications bear any truth, the Locky threat actors once again demonstrate their unscrupulous nature and willingness to exploit the misfortune of others at any step in their delivery and infection process. However, absent the reference to the Office of Personnel management, this set of emails would be just another set of phishing emails delivering Locky featuring strange word choice such as “suspicious movements” and “out account”.
These emails reinforce the fact that overcoming the phishing threat and the ransomware it delivers is not some insurmountable task. Instead, user education and the bolstering of incident response practices can give organizations the edge over threat actors.
Indicators of compromise related to this set of Locky emails are verbose—323 unique JavaScript application attachments were identified with the capability to download obfuscated Locky payloads from 78 distinct payload locations. These locations are listed below.
hxxp://cgrs168[.]com/xmej0mc
hxxp://acrilion[.]ru/84m9t
hxxp://geethikabedcollege[.]com/766epkuj
hxxp://thisnspeel[.]com/766epkuj
hxxp://thisnspeel[.]com/3ypojyl
hxxp://flurrbinh[.]net/7wi66hp
hxxp://vexerrais[.]net/6sbdh
hxxp://3-50-90[.]ru/u4y5t
hxxp://corinnenewton[.]ca/ctlt8b
hxxp://agorarestaurant[.]ro/cg06f
hxxp://abercrombiesales[.]com/nmuch
hxxp://flurrbinh[.]net/3nrgpb
hxxp://dmamart[.]com/c5l2p
hxxp://codanuscorp[.]com/ay5v52r
hxxp://cafedelrey[.]es/snby1c
hxxp://vexerrais[.]net/84fwijj
hxxp://dessde[.]com/zcwaya
hxxp://villaamericana[.]net/84fwijj
hxxp://ayurvedic[.]by/b9kk9k
hxxp://dowfrecap[.]net/3muv
hxxp://odinmanto[.]com/57evyr
hxxp://centinel[.]ca/wkr1j6n
hxxp://berrysbarber[.]com/q6qsnfpf
hxxp://antivirus[.]co[.]th/jukwebgk
hxxp://odinmanto[.]com/7gplz
hxxp://www[.]cutillas[.]fr/lmc80sdb
hxxp://365aiwu[.]net/hbdo
hxxp://comovan[.]t5[.]com[.]br/byev5nd
hxxp://alpermetalsanayi[.]com/vuvls
hxxp://bielpak[.]pl/a79a64h
hxxp://dowfrecap[.]net/7qd7rck
hxxp://babuandanji[.]jp/lq9kay
hxxp://pastelesallegro[.]mx/ex67ri
hxxp://archmod[.]com/sapma
hxxp://drkitchen[.]ca/y5jllxe
hxxp://earthboundpermaculture[.]org/okez95b
hxxp://eroger[.]be/918p2q
hxxp://avon2you[.]ru/ayz1waqm
hxxp://handsomegroup[.]com/ae2y1hr
hxxp://vexerrais[.]net/3nx3w
hxxp://cosmobalance[.]com/jsqlt0g
hxxp://assetcomputers[.]com[.]au/lkfpyww
hxxp://odinmanto[.]com/2rw
hxxp://dinglihn[.]com/zg3pnsj
hxxp://thisnspeel[.]com/2qrn06f
hxxp://adriandomini[.]com[.]ar/bq62dx
hxxp://inzt[.]net/lbrisge
hxxp://elektronstore[.]it/z298ejb
hxxp://donrigsby[.]com/nts0mk
hxxp://bjshicheng[.]com/blewwab
hxxp://ck[.]co[.]th/r2k6i
hxxp://abclala[.]com/r2kvg
hxxp://lashouli[.]com/rq4xoq
hxxp://flurrbinh[.]net/0nbir
hxxp://competc[.]ca/qrc9n
hxxp://dowfrecap[.]net/6f9tho
hxxp://chaturk[.]com/mxaxemv
hxxp://odinmanto[.]com/0cz2zwz
hxxp://dowfrecap[.]net/0d08tp
hxxp://dekoral[.]eu/twnyr1s
hxxp://chandrphen[.]com/h4b1k
hxxp://drmulchandani[.]com/d6ymtf
hxxp://edrian[.]com/dfc33k
hxxp://fibrotek[.]com/deoq
hxxp://vexerrais[.]net/1jk8n
hxxp://accenti[.]mx/nryojp
hxxp://cheedellahousing[.]com/h24ph
hxxp://elleart[.]nl/gn3pim
hxxp://edubit[.]eu/b6ye94wv
hxxp://bst[.]tw/gnjeebt
hxxp://85[.]92[.]144[.]157/y8giadzn
hxxp://thisnspeel[.]com/04u77s
hxxp://dunyam[.]ru/jge1b3e
hxxp://flurrbinh[.]net/6mz3c5q
hxxp://eldamennska[.]is/h4yim
hxxp://bepxep[.]com/mo05j
hxxp://dwcell[.]com/dph861ws
hxxp://apidesign[.]ca/ijau8q2z
However, only four hardcoded command and control hosts were found to be supporting this Locky instance. They are listed below.
hxxp://195.123.211[.]229/message[.]php
hxxp://188.65.211[.]181/message[.]php
hxxp://185.102.136[.]127/message[.]php
hxxp://185.67.0[.]102/message[.]php
Furthermore, a single payment site where the ransomware victim can pay the Bitcoin ransom in exchange for a purported decryption application was identified.
mwddgguaa5rj7b54[.]onion
The full PhishMe Intelligence report on this Locky analysis is available to PhishMe Intelligence clients here.
Never miss another phishing threat! Sign up for our complimentary Threat Alerts subscription service today.
Learn more about Locky and other ransomware threats at PhishMe’s Global Ransomware Resource Center.


