Proofpoint
Microsoft 365 EOP
By Chris Hall, Professional Services
There are plenty of websites offering URL scanning for malicious links. Their tools are a quick and easy way to analyze a URL without visiting the site in a sandboxed environment. Widely used, these tools are accurate to a point.
But in today’s phishing landscape, where attacks are increasingly sophisticated, such tools are becoming less and less reliable. We in the Cofense Phishing Defense CenterTM (PDC) believe they are ineffective against more advanced phishing websites.
Phishing Sites Are Using Redirect Methods to Avoid Detection
Let start with this example:
An attacker can easily set up a new domain and host a phishing site with a legit SSL certificate from most established certificate authorities for free. The attacker then can configure the server or webpage to redirect all connections that are not from the organization’s IP to an external safe site such as google.com.
If a security analyst then submits the URL to a third-party lookup tool, for example VirusTotal, the tool will only detect the site google.com and not the actual phishing site. At this point, the analyst can submit the URL to another URL scanning tool, but the results will all come back the same.
In the Cofense PDC, we are seeing an increase of phishing sites that are using redirect methods to avoid detection from URL scanners and unaware security analysts.
Here is another example with browser detection phishing websites:
This phishing link below redirected users depending on which browser they used. If users use Firefox as their default browser, they will get the actual payload, while a Chrome default browser will get a redirect to MSN.
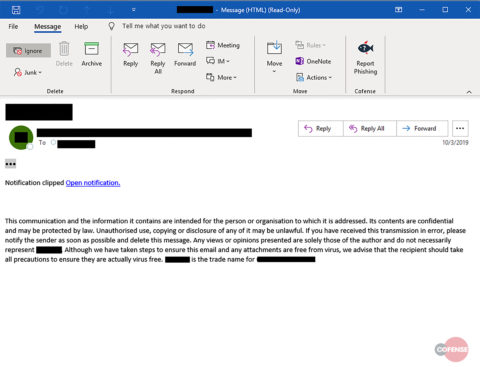
Figure 1: Original Phishing Email
When recipients click the ‘Open Notification’ link in the email message above, they are directed to the website below.
URL: hxxp://web-mobile-mail.inboxinboxqjua[.]host/midspaces/pseudo-canadian.html?minor=nailer-
When someone clicks the URL, the experience can vary depending on the default browser, Firefox vs. Chrome.
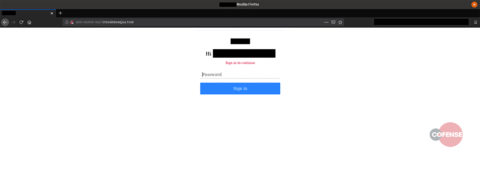
The real phish site using Firefox:
Figure 2: Actual Phishing Site
Using Chrome:
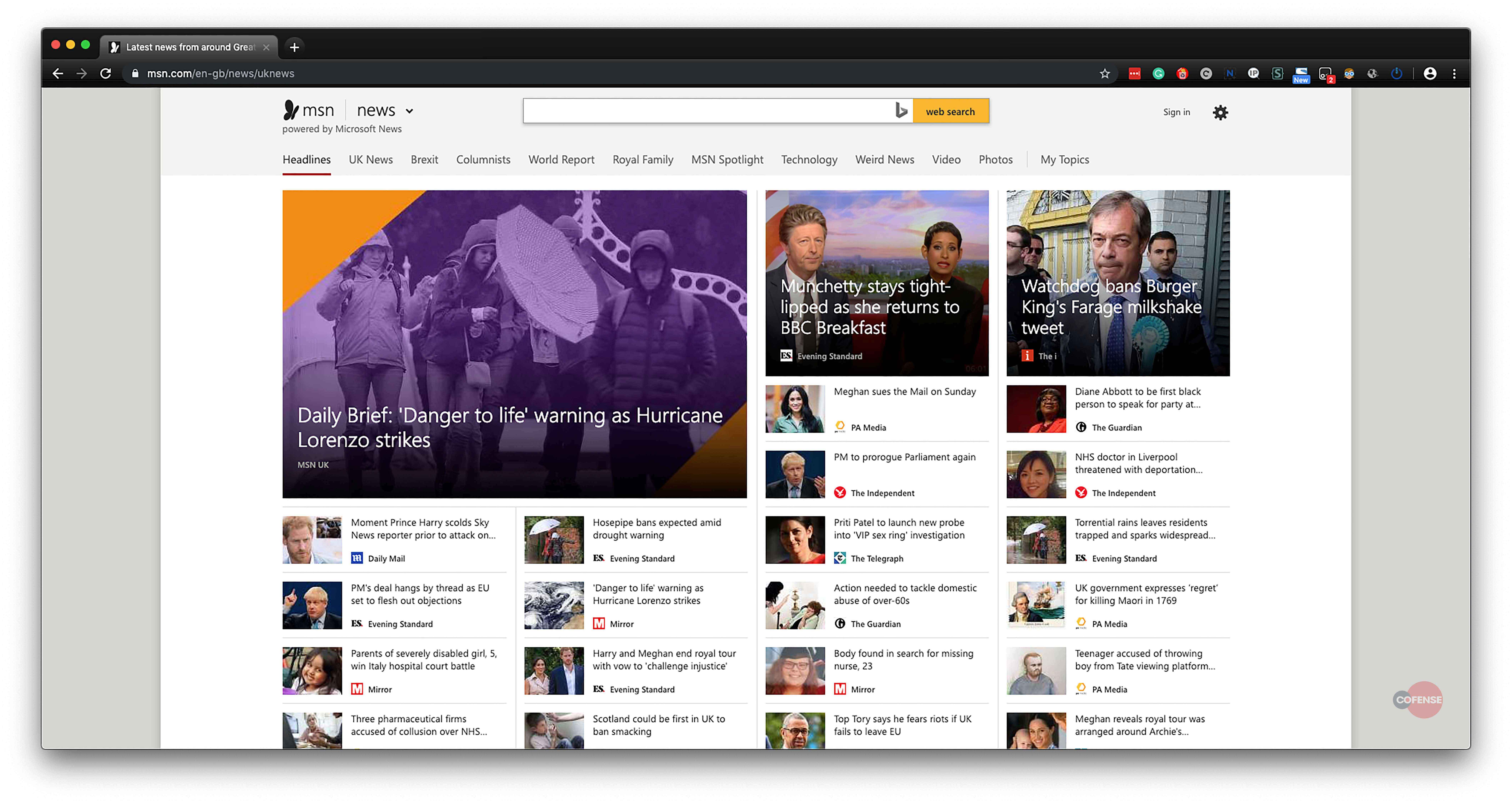
Regardless of the user’s geolocation, the URL redirect will go to the UK page. URL: https://www.msn.com/en-gb/news/uknews
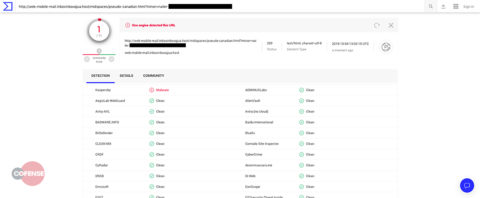
Now let’s put the same URL in a popular URL scanner and see the results:
Figure 4: Virus Total Results of the Reported URL
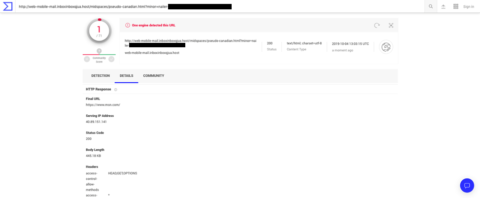
The search results show that one of the vendors has detected the phishing site as malware. However, this is not the case. Let’s look at the Details tab.
Figure 5: VirusTotal Details of the Reported URL
In the results it states that the final URL is to msn.com. We still do not know what the actual phishing site looks like, what the site is doing, or even if the phishing site is active at all.
There’s a Better Way to Check for Malicious Links
Organizations must ask if these URL scanners are providing enough information to analysts so they can complete their investigations. Is the scanner testing the suspicious link with multiple user agents or querying the site with different source IP addresses? While the URL scanning services are useful, they lack the basic dynamic analysis that most analysts will perform on a malicious website.
What if I told you that it is quick, easy, and more accurate by far to analyze URL based phishing attacks manually, using various tools such as User-agent switcher or with a VPN and proxy servers while in a dedicated virtual machine? Remember that if a phishing email bypassed those same scanners to reach your users’ inboxes, it’s an undiscovered phishing attack and will require human analysis.
To better equip your analysts, we came up with a list that your security team can use to detect these types of attacks.
- Create an isolated proxy server that can reach out to the phishing site without restrictions.
– If your company has locations in different countries, use additional proxy servers in those countries or use proxy services like Tor or a third-party VPN service.
– Acquiring a VPN service with multiple locations is another option.
– Create a “dirty” network to browse malicious sites that can also be used to analyze malware samples.
- Create a VM for URL analysis.
– This VM should be isolated from the organization’s network.
– VMs such as Remnux will have tools built-in to assist in URL and file analysis.
- Use Firefox for visiting the site
– Based on the vast amounts of customization, Firefox may be the best browser suited to URL analysis
– Add-ons such as User-agent switcher, FoxyProxy, and HTTP Header Live are essential.
– You can also use the browser’s developer tools to track requests, detect redirects, and alter elements on the page.
URL scanning services are useful to a point. These tools will alert you to some suspicious URLs, but often lack the details need for escalations and blocking the threat. More often than not, the tools will be a point of failure for your organization’s security due to the high amount of risk they introduce. So take a couple of minutes to look at that suspicious URL in a safe environment and see what it really does. It may save you lots of money and time cleaning up an incident.
HOW COFENSE SOLUTIONS CAN HELP
Easily consume phishing-specific threat intelligence to proactively defend your organization against evolving threats with Cofense IntelligenceTM
90% of phishing threats observed by the Cofense Phishing Defense Center bypassed secure email gateways. Condition users to be resilient to evolving phishing attacks with Cofense PhishMeTM and remove the blind spot with Cofense ReporterTM.
Quickly turn user reported emails into actionable intelligence with Cofense TriageTM. Reduce exposure time by rapidly quarantining threats with Cofense VisionTM.
Thanks to our unique perspective, no one knows more about REAL phishing threats than Cofense. To understand them better, read the 2019 Phishing Threat & Malware Review.
All third-party trademarks referenced by Cofense whether in logo form, name form or product form, or otherwise, remain the property of their respective holders, and use of these trademarks in no way indicates any relationship between Cofense and the holders of the trademarks. Any observations contained in this blog regarding circumvention of end point protections are based on observations at a point in time based on a specific set of system configurations. Subsequent updates or different configurations may be effective at stopping these or similar threats.