URL shorteners are a great tool to share a web address without a lot of typing. PhishMe Intelligence™ recently observed malicious actors using these services to evade security controls. They use these services to conceal the actual URL and bypass controls put in place to block known malicious domains.
Just this week, employees of enterprises using PhishMe® reported phishing messages that contain links that use these URL shortening services:
- bit.ly
- goo.gl
- ow.ly
- s.id
- smarturl.it
- tiny.pl
- tinyurl.com
- x.co
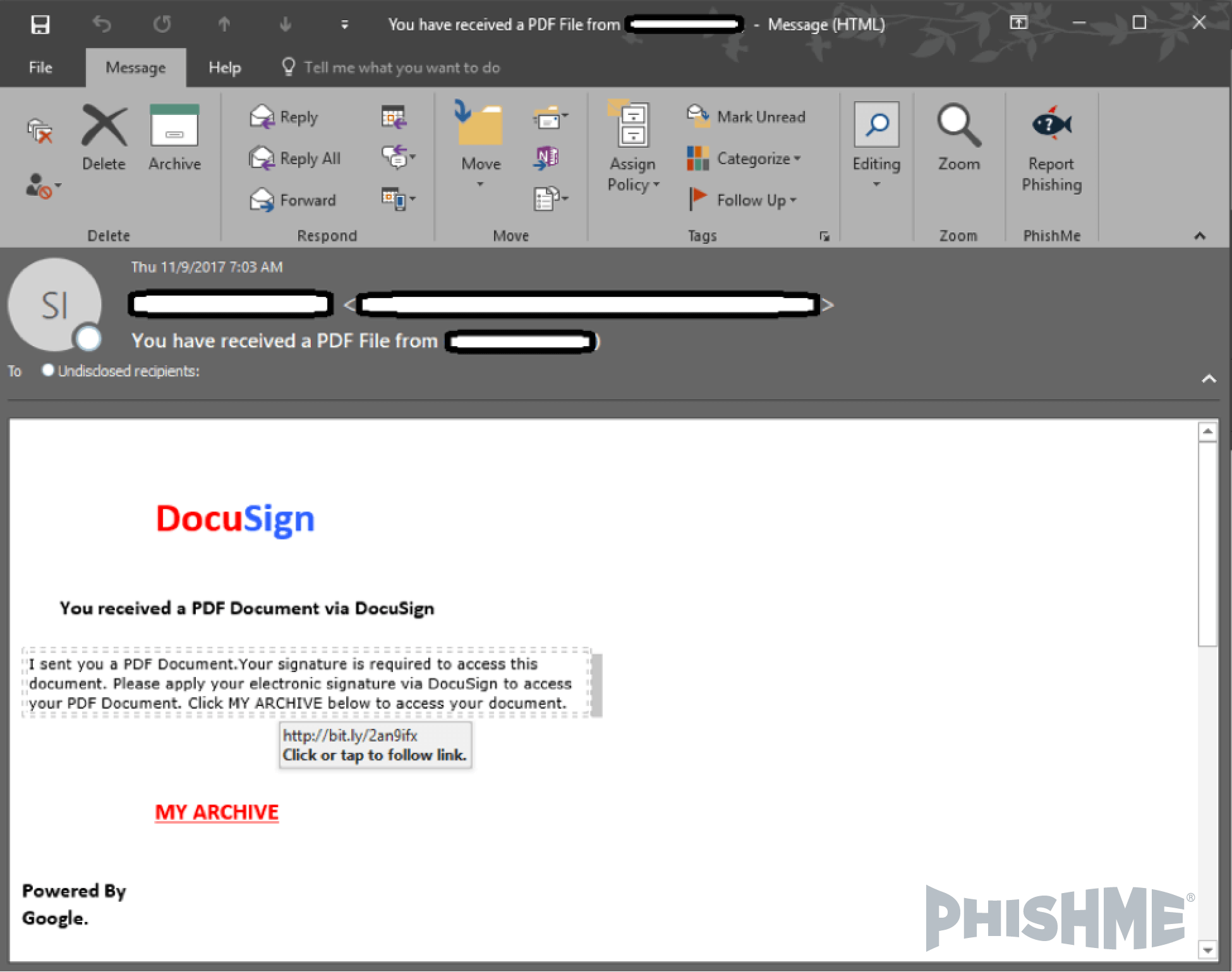
While some end users have been trained to hover their mouse over the link in a suspicious message to see the true destination of the link, this strategy does not work when the scammer uses a URL shortener link. As seen in figure 1 below, you can see that hovering over the “MY ARCHIVE” link revealed only a URL hosted on a URL shortening service.
Figure 1 – Phishing message delivering a shortened URL to a DocuSign phishing page
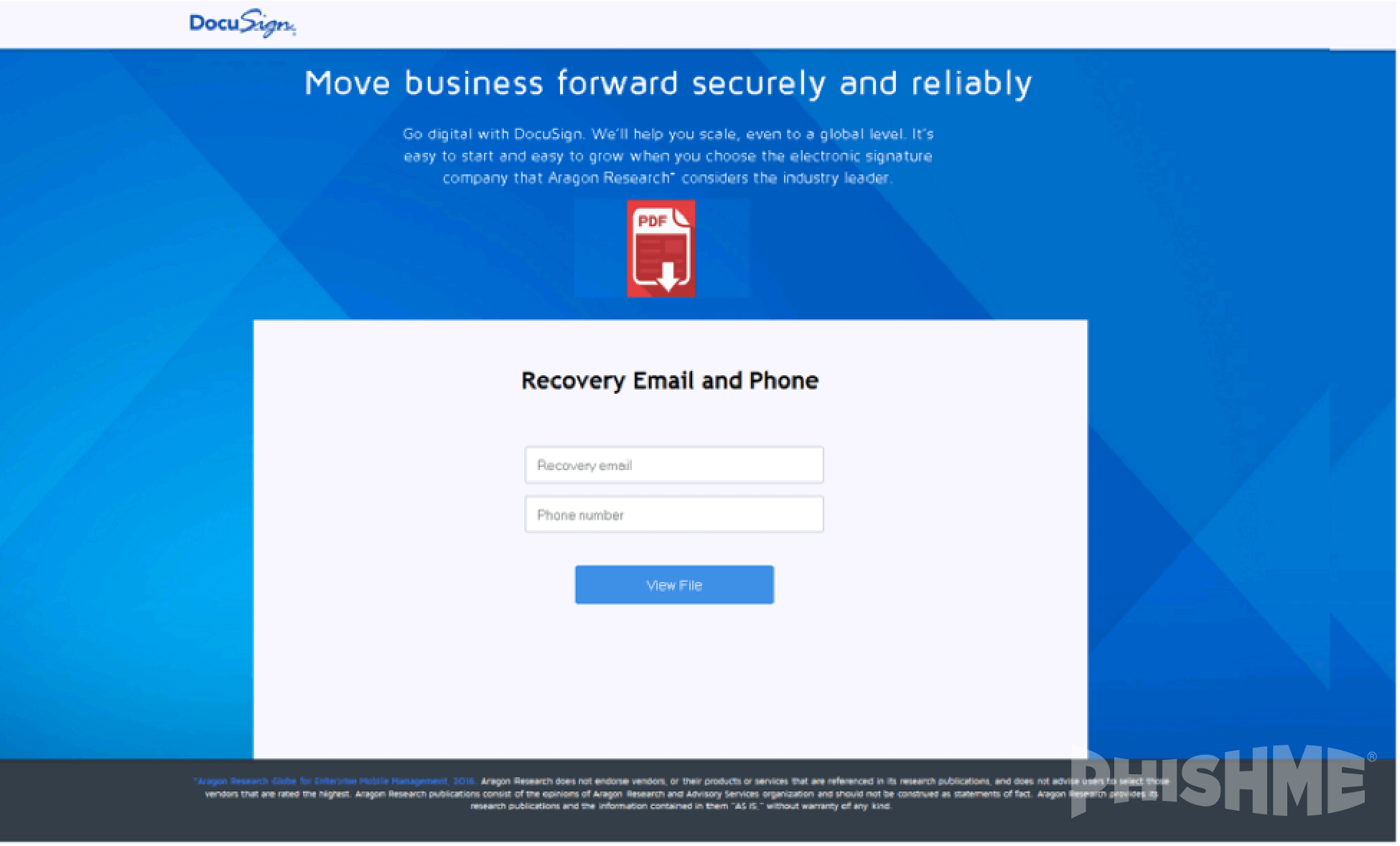
After clicking the link, the user is redirected to a page, as seen in figure 2, that spoofs DocuSign with the goal of collecting the end users email password. In this case they are targeting any email providers with a focus on AOL, Yahoo!, Gmail, Outlook and Office 365.
Interestingly, a subsequent step of the attack collects the victims’ recovery email account and phone number, as seen in Figure 3 below. These additional pieces of information can be very valuable for a bad actor. Even after the user provides all this information, the user does not receive the PDF file download.
Figure 3 – Step 2 of phishing attack, seen at hxxp://avantysimmo[.]com/tht/dokin/recova.php
PhishMe Intelligence is a service that is designed to inform our customers about phishing threats. PhishMe distributes intelligence about those threats via the PhishMe Intelligence API as machine readable threat intelligence (MRTI). The MRTI includes the shortened URL parsed from the suspicious message and the associated landing page URL. PhishMe Intelligence also identifies the “Action URL”, which represents the path to the script that handles the delivery of credentials stolen in the attack. Often these Action URLs are on a third host and must also be recognized as indicators of compromise in an enterprise environment.
When our investigators drill into the details of URL shorteners, they also see that quite often the phisher will use more than one redirection from the initial link. For example, the initial link may be on bit.ly, but that link may point to a URL on ow.ly which then points to another ow.ly link that finally points to a phishing landing page hosted on a compromised domain, a fraudulent domain, or a customized subdomain arranged on a free-hosting site. Each of these steps of the attack are captured by PhishMe in the Web Components list in the PhishMe Intelligence portal for investigators. All of the components are also available for download from the portal.
Don’t ever miss another threat – sign up for PhishMe® Threat Alerts today and receive updates on new and emerging phishing and malware threats, completely free.