By Aaron Riley
Not even the halls of justice are immune from scammers. A new phishing campaign spoofing the UK Ministry of Justice has successfully targeted users with a subpoena-themed email delivering Predator the Thief, a publicly available information-stealing malware.
Cofense IntelligenceTM has observed employees in insurance and retail companies receiving these emails. The phishing email states that the recipient has been subpoenaed and is asked to click on a link to see more details about the case. The enclosed link uses trusted sources—namely Google Docs and Microsoft OneDrive—for the infection chain. The initial Google Docs link contains a redirect chain that eventually leads to a malicious macro-laden Microsoft Word file. The macro, upon execution, downloads the malware via PowerShell, which is a sample of the Predator the Thief information stealer.
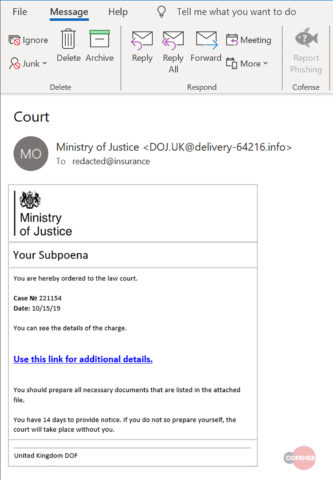
The email body, shown in Figure 1 below, contains a warning that the recipient has 14 days to comply with the subpoena notice, a scare tactic designed to panic users into clicking. The link within the email leads to a Google Docs page and is benign, unlike the embedded URL within the Docs page that features a tailored redirection link pointing to a direct Microsoft OneDrive download. The Google Docs page is themed to fool a user into thinking the service is conducting security checks.
Figure 1: Sample Phishing Campaign Delivering Predator the Thief
Organizations defending against this multi-faceted threat have four options.
- While a basic email security stack would likely misread the Google Docs URL as legitimate and allow the email to pass inspection—in fact, this campaign has passed through FireEye’s Secure Email Gateway (SEG) solution and may be overlooked by others—scanning the ensuing links at the network security level should reveal nefarious intent, at which point the security solutions should block further traversal.
- Disabling Microsoft macros by default and monitoring PowerShell execution alongside educating users on the dangers of enabling macros is a safeguard against this threat.
- Employing endpoint protection solutions that conduct memory analysis can spot the payload execution, thwarting an intrusion at the last step of the infection chain.
- Having a highly tuned network security stack that monitors for exfiltrated data and suspicious HTTP POST packets can help spot an intrusion or block its exfiltration route.
Technical Findings
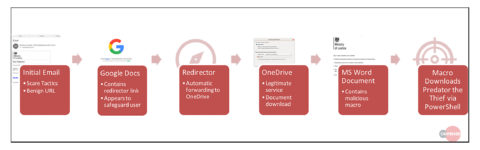
The email contains a link that leads to a trusted source, in which another link leads to yet another trusted source through a tailored redirecting URL in the middle. A macro-laden document is retrieved and used as a first stage downloader to execute a sample of Predator the Thief. The malware then infects the endpoint and attempts to exfiltrate sensitive data. At each step of this infection chain (outlined in Figure 2), correctly configured technology could have prevented successful execution, and a properly educated end user could have negated the entire scenario.
Figure 2: Infection Chain
Predator the Thief has all the basic capabilities of most information stealers. One of the unique things about this malware is its range of web browsers targeted, meaning a less popular web browser may still be affected. The authors disseminate their product via a Telegram channel that is also used as a customer support channel. Although Predator the Thief claims to have Anti-VM capabilities, older versions can be easily detected by automated AV scanning. A newer version can be quickly spotted in a sandbox once the binary has unpacked itself into memory. The execution of the binary on the endpoint is an additional focal point for defense within the endpoint protection program or product.
Predator the Thief targets cryptocurrency wallets, browser information, FTP, and email credentials. It can also take a screenshot of the infected machine. The information is stored in a file named “information.log” and sent to the Command and Control (C2) server via an HTTP POST to a network endpoint “gate.get” by default. The data in this file contains machine and user fingerprint data, stolen credentials, and network configurations. Once the information is gathered and the sample has successfully exfiltrated the data to the C2, the binary then cleans up parts of the infection and self-terminates. This infection clean-up process makes it much harder for endpoint forensic investigations that do not leverage verbose event logs and an endpoint detection system.
Indicators of Compromise
| IOC Appendix | Description |
| PM_Intel_PredatorThief_31571 | Cofense Intelligence YARA Rule |
| hxxp://comrade696[.]xyz/api/gate[.]get | C2 Network Endpoint |
| hxxp://bit[.]do/fcMEx | “Legitimate” URL Shortener Service For Payload |
| hxxp://193[.]0[.]178[.]46/m2Dj5W | Tailored Redirector |
| 31[.]184[.]196[.]176 | Macro Payload Host |
| comrade696[.]xyz | C2 Address |
| hxxp://comrade696[.]xyz/api/check[.]get | C2 Network Endpoint |
| hxxp://31[.]184[.]196[.]176/file8[.]exe | Predator the Thief Payload |
| 193[.]0[.]178[.]46 | Tailored Redirector |
| hxxps://de5qqw[.]sn[.]files[.]1drv[.]com/details[.]doc | Microsoft OneDrive Direct Word Document Download |
| hxxp://docs[.]google[.]com/document/d/e/2PACX-1vR2ShicgBwEhJsMeJF-ho3xmeGvs4h3lpp33DGuVYXa0J7nDHSayHNnUqAuy8RgE1V6DN3rgEamM_l6/pub | Google Docs Lure |
| hxxp://docs[.]google[.]com/document/d/e/2PACX-1vTJwmMgl4cycKB1H3DLqE6hO7hBtIZV_R8vetvNk2hoHNvQrOQu6guqESe4ongHOe2qeuZl_hcwtpFi/pub | Google Docs Lure |
| hxxp://docs[.]google[.]com/document/d/e/2PACX-1vSC7TE8Jw2rj5mFmdo7SNhhVhYI5_chETx0Um8phyExpH2ok1_BYqbFBCmvu5SNE8USRHFQxAAdSUbe/pub | Google Docs Lure |
| hxxp://docs[.]google[.]com/document/d/e/2PACX-1vRHdNziiJLKswksr50gCvUFKGZPoB7aJ2X_u09dUvpXauv5zqPi6BRxmNlhpdQ3VoJnyDd-7UWe0eq4/pub | Google Docs Lure |
| hxxp://docs[.]google[.]com/document/d/e/2PACX-1vTDBKHYpJMHsTmAPu8Q3q41G3Sfq0398Mwe1bUth_4gbi9Q9X1uvjJ8Qpt1jfiDjkOvlrV3EGbn4pIH/pub | Google Docs Lure |
| hxxp://docs[.]google[.]com/document/d/e/2PACX-1vQYPpaggmpXxbXvzYbcuCFnVbVGFiprq8WT3U0cackWI9z6ECOKGQ75Zxi38IIAcR6U2mWRN-I91RJs/pub | Google Docs Lure |
| hxxps://www[.]google[.]com/url?q=hxxp://193[.]0[.]178[.]46/m2Dj5W&sa=D&ust=1572032929507000 | Google Docs Lure |
| hxxp://docs[.]google[.]com/document/d/e/2PACX-1vSpWb2Y8awd5BhJGCiiscMOhddh3Pf53q_E76aMV-H4L1Sy50O8V7wXJG8lLILi_woj35v22P2o0GZo/pub | Google Docs Lure |
| hxxp://docs[.]google[.]com/document/d/e/2PACX-1vSw-6rt5QaRo630a6nWVkraLUHH1HLP23pfkdYYxe3NS73ITrhzme_r_K0h67RQjrUjYgrVPDDNt9Yn/pub | Google Docs Lure |
| hxxp://docs[.]google[.]com/document/d/e/2PACX-1vTMEq8o1xfYAGRQqTnV_YP4IpoYFLRV0x3yagV4J8TC2vPAevx5y6UobCv9Oa9d1W-KzWbintL_fj2w/pub | Google Docs Lure |
| hxxp://docs[.]google[.]com/document/d/e/2PACX-1vRJh78bDJcfBuwt_yV7nhNRuboEHUyfET1yhta2B-_toyEPBl7OwADQHm9t28gfVQymkltq69smXgYw/pub | Google Docs Lure |
| hxxp://docs[.]google[.]com/document/d/e/2PACX-1vRZG0aGBmvWRzXhT-a68tBJcy1PSPA4blZ51daX_-OqtXwj-GeuEp-0RBbhazOBKi_Z2bE1AO8ejfTP/pub | Google Docs Lure |
HOW COFENSE CAN HELP
The Cofense Phishing Defense CenterTM finds that 89% of phishing threats that deliver malware have bypassed email gateways. Condition users to be resilient to phishing with Cofense PhishMeTM and remove the blind spot with Cofense Reporter TM. Cofense PhishMe offers a simulation template, “UK Ministry of Justice Subpoena – Office Macro”,” to educate users on the campaign described in today’s blog.
Quickly turn user reported emails into actionable intelligence with Cofense TriageTM. Reduce exposure time by rapidly quarantining threats with Cofense VisionTM.
Easily consume phishing-specific threat intelligence to proactively defend your organization against evolving threats with Cofense IntelligenceTM.
Thanks to our unique perspective, no one knows more about REAL phishing threats than CofenseTM. To understand them better, read the 2019 Phishing Threat & Malware Review.
All third-party trademarks referenced by Cofense whether in logo form, name form or product form, or otherwise, remain the property of their respective holders, and use of these trademarks in no way indicates any relationship between Cofense and the holders of the trademarks. Any observations contained in this blog regarding circumvention of end point protections are based on observations at a point in time based on a specific set of system configurations. Subsequent updates or different configurations may be effective at stopping these or similar threats.