The Cofense Phishing Defense Center (PDC) employs expert Threat Analysts to analyze emails on behalf of enterprise customers across the globe, in various industries, who are dealing daily with phishing attacks delivering malware. To help keep up with evolving tactics and top ongoing threats affecting real customers, the PDC has created a breakdown of the top five malware families we have seen across the Managed Phishing Detection and Response (MPDR) customer base over the past thirty days. If you have any interest in learning more about how your organization can be protected by our expert Cofense Threat Analysts, please contact us for additional information.
Top Malware Families in January:
1. Banload – The Banload Banking Trojan is typically used for stealing credentials from Brazilian online banking websites. After checking the geo-location of the device and system information such as the keyboard layout, the next stage payload is downloaded. A recent campaign was observed utilizing a batch script to execute PowerShell commands to drop a PE file.
- Subject: Most deliveries of Banload that we have seen this month have been made to appear as though they are boleto from Brazilian banks.
- Attachment: Most deliveries of Banload this month were seen delivered as a PDF file.
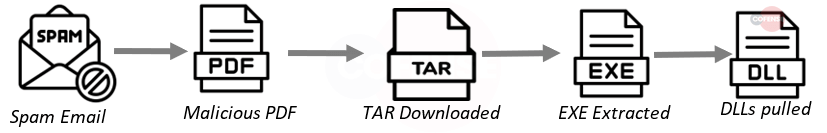
- Behavior: PDF attachment contains link to download a .tar archive. Archive contains the stage 2 .exe which pulls DLLs that make the malware function.
- Infection Chain:
2. Agent Tesla – This keylogger is known for checking browser activity to steal banking information and will send the data through various methods. The most recent variants will use SMTP to send data through Tor, Telegram, and email addresses under the control of the threat actor.
- Subject: Subjects were varied and in many languages, however, most of them allude to RFQs or POs made to look like they are coming from reputable companies. Some were using fake companies which were said to be from Ukraine.
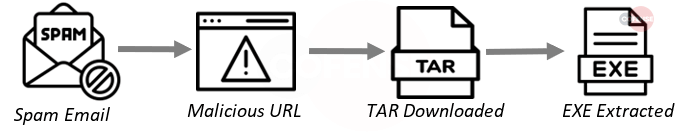
- Attachment: Typically, Agent tesla is delivered VIA an infection URL and not an attachment.
- Behavior: URL delivery of an exe which nests runs in the background and acts as a keylogger.
- Infection Chain:
3. Mekotio– This trojan targets South American users and will download its payload using various methods. The current campaign has a focus on Spain and will download a ZIP file. After running, it will download a ZIP file which contains JS, DLL, and an AHK file. The JS will use AutoHotKey (AHK) to run the DLL which is the main Mekotio payload. A new variant of Mekotio is utilizing a DLL side-loading technique where DLLs related to legitimate applications are ran, which then load in Mekotio.
- Subject: Emails delivering Mekotio this month were seen to be mainly spoofs of electronic invoices. The companies they come from were varied but many were made to look like Vivo invoices and predominantly delivered in Portuguese.
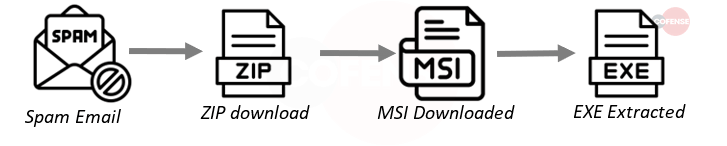
- Attachment: Mekotio is delivered using an infection URL instead of an attached file.
- Behavior: After the URL is clicked, the victim downloads the ZIP containing an MSI that contains the stage 2 exe.
- Infection Chain:
4. Remcos – Remcos was originally a remote desktop connection tool that has since been repurposed as a remote access trojan capable of taking control of a user’s system. Its chief capabilities include key logging, information stealing, and audio/visual monitoring.
- Subject: Subject lines delivering Remcos this month were mostly in Spanish and had a variety of topics from Judicial summons to money transfers in attempts to get clicks.
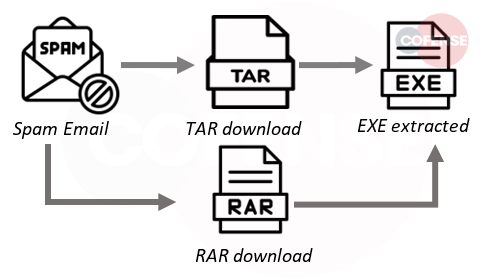
- Attachment: Most deliveries of Remcos contained no attachments this month and were instead delivered by VIA infection URL.
- Behavior: Once the archive (either .tar or .rar) is downloaded and the .exe inside clicked, then the malware sits in processes.
- Infection Chain:
5. Netsupport Manager RAT – This remote administration tool (RAT) is a legitimate tool being used maliciously by threat actors. Its functionality includes the ability to log keystrokes, steal sensitive information, record audio, and execute commands remotely; essentially giving complete control over an infected machine.
- Subject: Subjects were about purchase reminders or invoices for products that come alongside an attached .html file.
- Attachment: Netsupport Manager RAT was seen mostly being delivered using an .html attachment.
- Behavior: Email contains an attached .html file which will pull a malicious JavaScript containing the malware.
- Infection Chain:
Summary
This month the PDC saw a significant rise in Banload malware as Qakbot fell off the list of top malware families identified within the PDC. Banload is a Brazilian banking trojan used to steal credentials and continues the trend we have seen of South American based malware being a popular tool for threat actors. Agent Tesla, Remcos, and Mekotio all continued to maintain consistency throughout January as they did in December. The rise of NETSupport Manager RAT on our list marks a comeback with the beginning of the new year for a malware family that has been popular in the past.
All third-party trademarks referenced by Cofense whether in logo form, name form or product form, or otherwise, remain the property of their respective holders, and use of these trademarks in no way indicates any relationship between Cofense and the holders of the trademarks. Any observations contained in this blog regarding circumvention of end point protections are based on observations at a point in time based on a specific set of system configurations. Subsequent updates or different configurations may be effective at stopping these or similar threats. Past performance is not indicative of future results.
The Cofense® and PhishMe® names and logos, as well as any other Cofense product or service names or logos displayed on this blog are registered trademarks or trademarks of Cofense Inc.