Thus far in 2018, PhishMe Intelligence™ has observed a lull in multiple malware families that were prominent throughout 2017. There are several possible reasons for this hiatus.
Why so quiet?
It is likely that some malware families have petered out and will not return in widespread campaigns. In sharp contrast to January of 2017, PhishMe Intelligence did not identify any samples of ransomware last month. In January 2017, we noted several small Locky ransomware campaigns, Cerber ransomware distributions, and the debut of Sage and Spora ransomware.
Alternatively, some malware authors and operators may be retooling their infrastructure to aid in further advancements of anti-analysis techniques, sandbox evasion, or implementation of unique delivery methods.
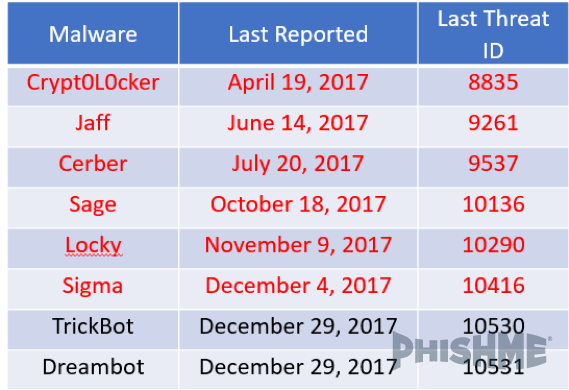
Several of last year’s prominent malware families that have yet to appear in 2018 include Locky ransomware, TrickBot, and Dreambot. PhishMe Intelligence last analyzed TrickBot and Dreambot in December 2017, while Locky has not been observed since early November 2017.
One likely reason for the silence of TrickBot and Locky is the Necurs botnet, which has been integral in recent TrickBot and Locky distribution campaigns and has been less active this year. This downturn in activity is recent, as PhishMe observed Necurs’ spamming of Scarab and Sigma ransomware as recently as December 2017.
Figure 1: Common Malware Yet Unseen in 2018
(Red notes ransomware family)
Not all is quiet on the malware front. Zeus Panda continues its steadfast distribution rates and Dridex has re-emerged after a December hiatus. Dridex proves that it is too soon to count out every yet-to-be-seen malware only one month into the year.
No matter what, remain vigilant.
However, the rapid turnover in ransomware between 2016 and 2017 suggests that the recently quiet ransomware families may be less likely to return at all. This specific type of malware may have higher turnover rates due to law enforcement, other infrastructure disruption or an industry-driven need to evolve quickly to overcome prioritized network defense technologies.
The decrease in known malware activity could signal a shift toward unidentified tools, with yet unknown indicators of compromise. Security researchers and incident responders must maintain awareness of new tactics, techniques, and procedures, and devise a response strategy to defend against such attacks.
If this lull indicates that new tools are being used in place of these common malware families, it increases the likelihood of malware breaching defenses and entering users’ inboxes. In turn, this again demonstrates the importance of empowering and training computer users to identify and report phishing emails.
Sign up for free threat alerts from PhishMe Intelligence and PhishMe® Research.