CISO Summary
Cofense IntelligenceTM reports that threat actors have spoofed a CDC email—this one warns of a flu epidemic—to deliver an updated variant of GandCrab ransomware. Besides competing for a new low in predatory cyber-crime, the phishing campaign follows the public release of a decryptor tool for infections of recent GandCrab versions, through version 5.1. The fake CDC email contained version 5.2, which renders the decryptor tool ineffective.
Though ransomware has dropped off over the past year, the authors of GandCrab are still pushing out frequent, powerful updates. GandCrab is the last of the infamous “ransomware as a service” threats. The extent to which its creators make upgrades, parrying and thrusting with security researchers, shows it’s still a very real weapon for revenue-hungry criminals.
Full Details
Recent updates to GandCrab Ransomware demonstrate that its operators remain committed to the malware’s effectiveness and are prepared to make urgent changes to overcome disruptions. Shortly after a coordinated public release of a decryptor tool for infections of GandCrab versions 5.0.4 through 5.1, Cofense Intelligence observed GandCrab v5.2 campaigns that rendered the tool ineffective. In a recent phishing email delivering GandCrab, a fabricated flu epidemic alert from the Center for Disease Control (CDC) was crafted to terrify recipients into opening an attached document. Far from receiving potentially life-saving instructions, the Office document was laden with macros, coded to download and execute a copy of—you guessed it— GandCrab v5.2.
Natural disasters, global geopolitical events, and pandemics are perfect narrative drivers for threat actors seemingly devoid of conscience, tact, or taste. Self-preservation is a human imperative, and such narratives that evoke fear and urgency are potentially more effective than those exploiting greed, empathy, or curiosity, other typical phishing narratives.
Coughs and Splutters
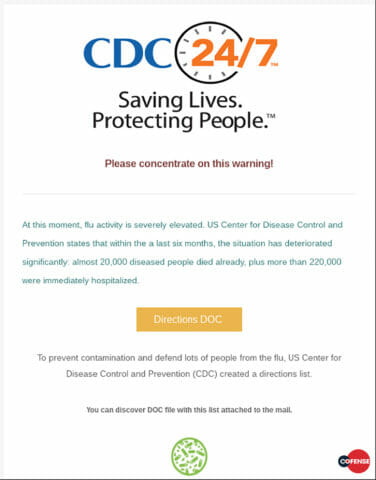
Despite leveraging a powerful concept, the execution of the observed campaign leaves much to be desired. Figure 1 shows the body of a typical message from this campaign.
Figure 1: a typical message observed during this campaign
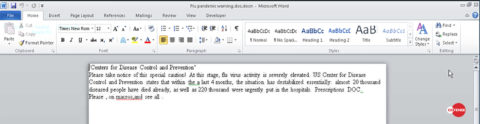
Ostensibly, the message is well-structured, somewhat professional and believable. However, a closer read would note the grammatical errors and unusual statements. The content of the attached document continues this trend, with such preposterously low effort as compared to the effort put into the phishing email. Figure 2 shows the content of the document, displayed to the user while the macros are busy downloading and executing GandCrab.
Figure 2: the content of the document, typically deployed as a decoy.
In scenarios that leverage weaponized documents as the attack vector, threat actors often disseminate believable content to distract the user while whatever required background processes run.
Where’s Trik?
A noticeable deviation from the recent standard GandCrab protocol is the absence of an intermediate loader. Since Feb 2019, all phishing campaigns that ultimately served GandCrab did so via Trik, a spambot with pretentions of data-stealer. Certainly not a wholly unique occurrence, it does reverse a trend that had been forming.
Despite ransomware becoming less and less lucrative, the actors behind GandCrab continue to push out extremely frequent and pertinent updates. On February 19th 2019, Bitdefender released a decryption tool for GandCrab V5.1. Later that same day, it came to light v5.2 – a version for which no available decryption utility would work – had already been released, seemingly in direct response to the decryption utility.
GandCrab is the last great bastion of the ransomware-as-a-service world. Its frequent updates, active engagement with security researchers, and novel abuse of vulnerabilities and weaknesses makes it a very real, and potentially very devastating, threat. By appealing to fear and self-preservation, this campaign highlights to what lengths threat actors will go to generate revenue.
To stay ahead of emerging phishing and malware trends, sign up for free Cofense Threat Alerts.
IoCs
Flu pandemic warning.doc 054607600b11e09fa74aa39c790357d6
perdaliche.exe b47b281a8d1f227d6a7f48f73192e7ed
hxxp://gandcrabmfe6mnef[.]onion/
hxxps://www[.]kakaocorp[.]link/data/images/kadeheme[.]jpg
hxxp://www[.]kakaocorp[.]link/news/image/kazuzu[.]bmp
hxxp://210[.]16[.]102[.]43/perdaliche[.]exe
All third-party trademarks referenced by Cofense whether in logo form, name form or product form, or otherwise, remain the property of their respective holders, and use of these trademarks in no way indicates any relationship between Cofense and the holders of the trademarks.