Educational Resources
Check out our resource library of solution content, whitepapers, videos and more.
Resources
Email Threats Your SEG is Missing
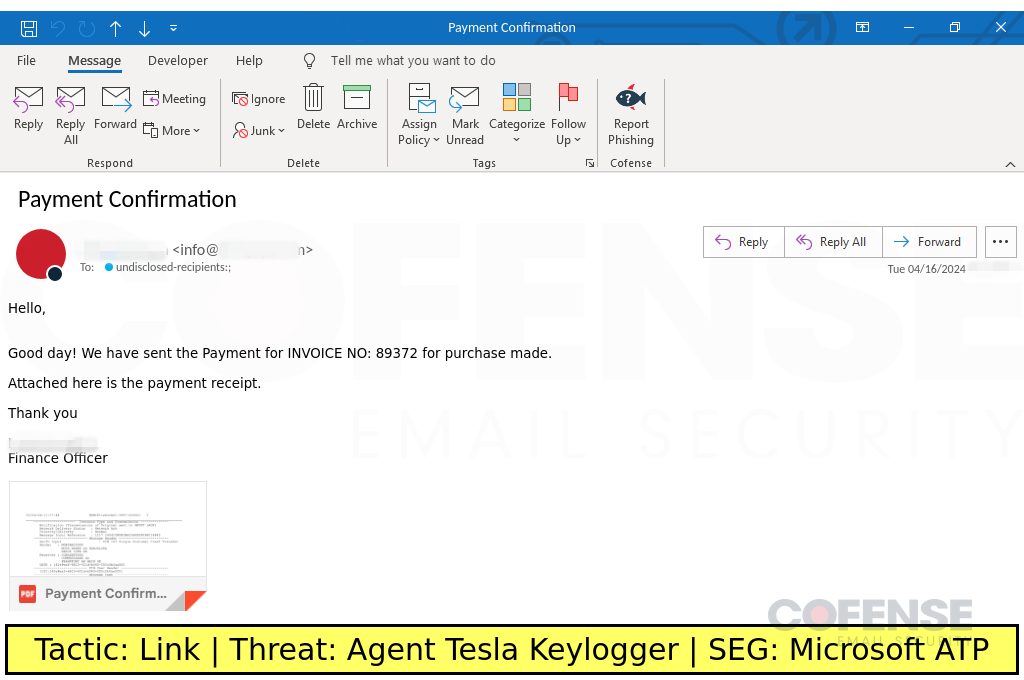
Agent Tesla Keylogger
Microsoft ATP
Posted on: 04/17/2024
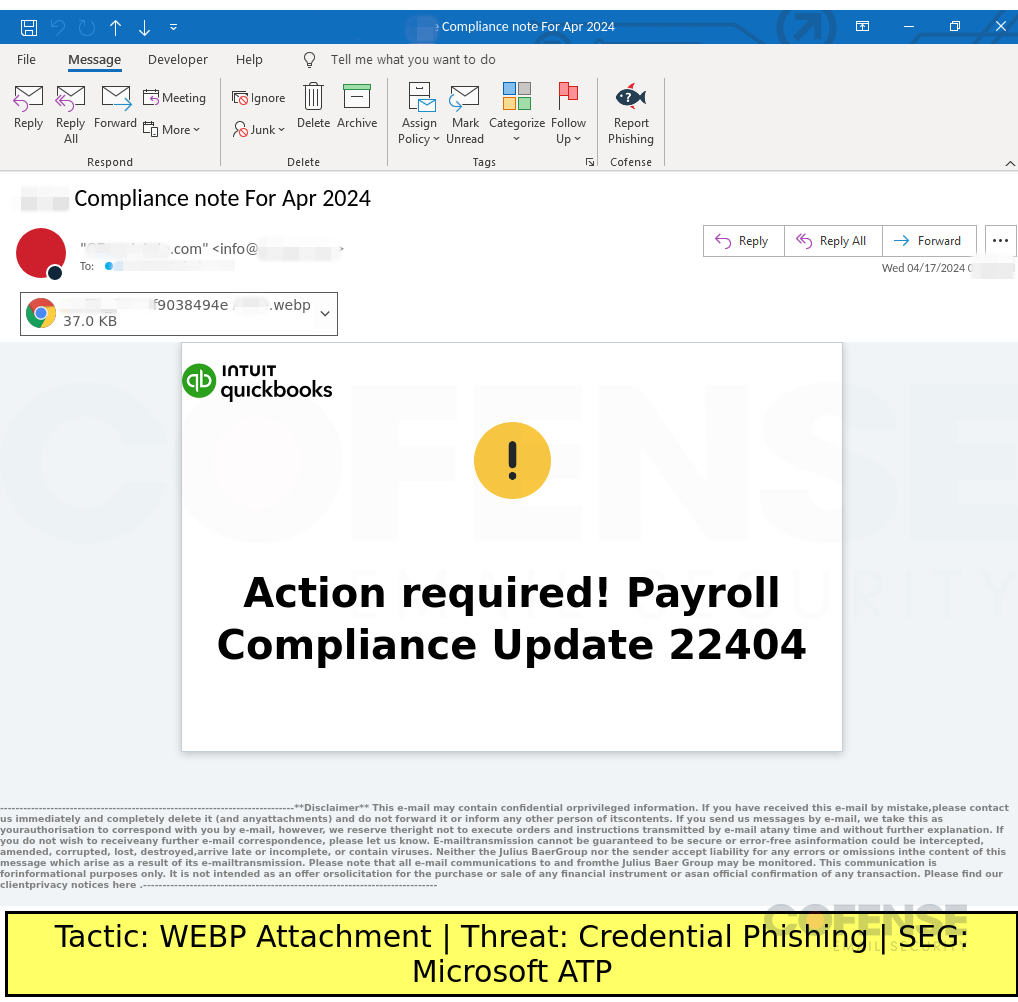
Credential Phishing
Microsoft ATP
Posted on: 04/16/2024
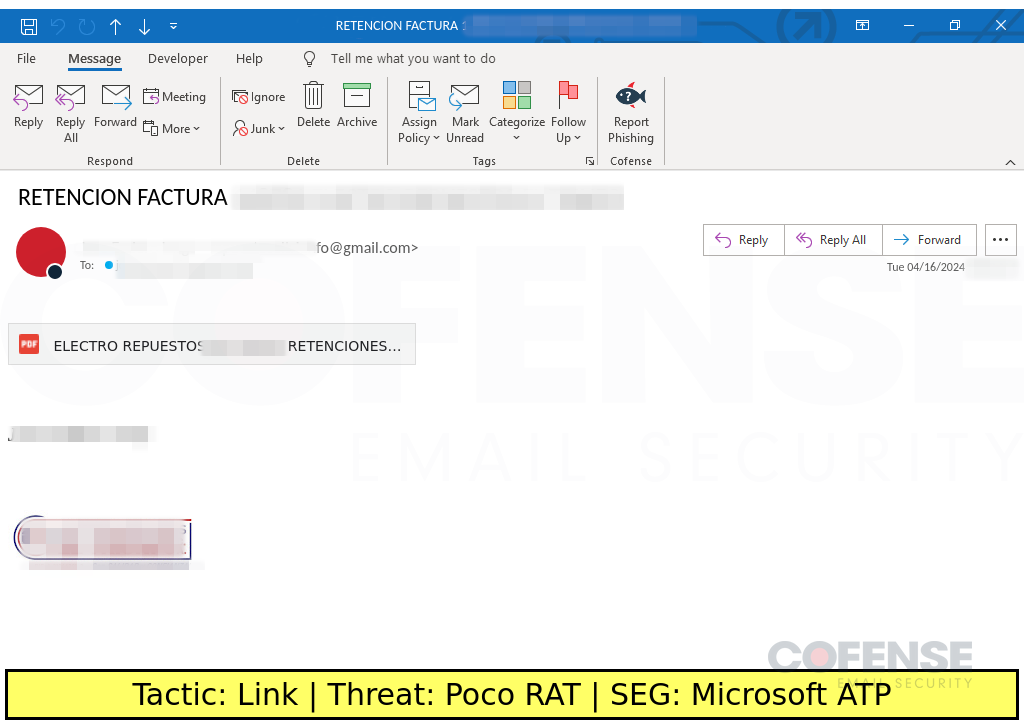
Poco RAT
Microsoft ATP
Posted on: 04/16/2024
Cofense Blogs
Recently Updated Rhadamanthys Stealer Delivered in Federal Bureau of Transportation Campaign
April 3, 2024
Midnight Blizzard APT Group’s Attack on Microsoft and What It Means for Email Security
March 20, 2024





