CISO Summary
Reaching deep into their bag of tricks to avoid detection, phishing emails and threat actors are using an oldie but goodie— packing image files (think tropical beach scenes) with malicious executables, usually a .jpg. The technique allows attackers to avoid detection by some anti-virus programs that merely recognize a file as an image, but don’t check its full contents.
This vintage tactic works—threat actors still use it a lot. Anti-virus systems rely on file headers to detect malware. Tuning systems to rely less on file headers is difficult and sometimes impossible. One counter-measure that does work: educate employees not to fall for phishing emails and encourage them to report any they find suspicious.
Full Details
Cofense Intelligence™ has been tracking the ongoing usage of image files to disguise malicious executables, a technique that can easily bypass network security measures. Threat actors will use a first stage malware downloader to retrieve an image file, most often a .jpg. The malware downloader then extracts a malicious executable that is embedded within the image. Finally, the malware runs the extracted binary in memory to avoid dropping an additional executable to disk. By using this technique to download the second binary, threat actors are able to avoid detection by some anti-virus (AV) programs that can determine the downloaded file to be an image but do not check the rest of the file contents.
Delivery
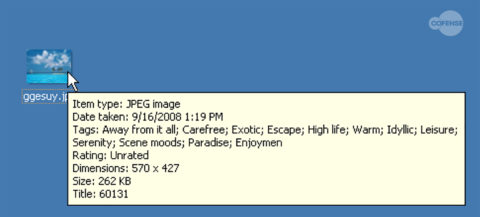
The malware downloader often used to deliver these types of files is an executable using the .NET framework. From May 2018 to April 2019, Cofense Intelligence saw images with embedded executables comprising more than 70% of the binaries downloaded by .NET executables. The images can be anything from famous actors to server rooms, but one of the more common ones can be seen in Figure 1.
Figure 1: Commonly seen image
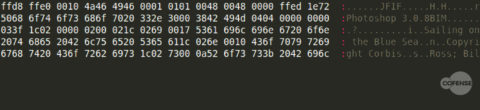
The images used not only display correctly but often have additional “metadata,” an example of which can be seen in Figure 2. This metadata is not present in all cases and may be an artifact from the original image before it was modified.
Figure 2: Additional meta data included in the image
Contents
The downloaded files are treated as images because of their file header and to a lesser degree, their file extension. File headers help the operating system determine how to interpret the contents of the file and can indicate several factors, such as whether a file is an image or an executable. Figure 3 illustrates that images with the .jpg extension, also known as JPEG images, will have the characters “JFIF” near the start of the file.
Figure 3: JPEG image file header
This header is also used by most AVs to determine the file type, as it is much more reliable than a file extension. When a “JFIF” header is read by most AVs the rest of the file will be ignored as long as the image is not broken or incomplete. The subterfuge of using an image file header also enables threat actors to bypass most network security measures which, like local AV, will treat the file as an image and ignore its content. By including an image that will properly display, threat actors are able to satisfy all of the conditions required for their malicious content to be ignored by security measures and “safely” delivered to the endpoint. This also ensures that if a file is manually downloaded and opened it will appear legitimate to the end user.
Extracting
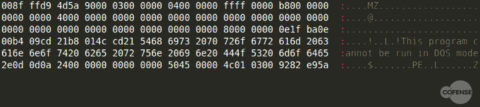
Creating an image file that meets these requirements also ensures that the operating system does not recognize the file as an executable and will not execute the file, regardless of the program used to open it. This fact requires a downloader, such as a .NET executable, to “extract” the malicious executable from the image file. This can be easily done by searching the file contents for the file header representing an executable, “MZ,” as shown in Figure 4.
Figure 4: Embedded executable header
Once this header is found, the executable content is carved out and loaded into memory rather than executing a file dropped to disk. Because the content is executed in memory rather than from an actual executable file, it is less likely to be recognized by AV as malicious. Most AV solutions do not monitor the memory of a process already running, which allows the malware to perform most of its activities without being noticed.
Staging
The fact that both a downloader and an image file are required to complete the infection is an important part of the infection strategy. If an image file is run by itself in an automated environment, it will simply display an image, with the only possibility of detection relying on the image file content having suspicious text. If only the downloader is executed and the image payload is unavailable, then it may be detected as suspicious, but on its own would not provide defenders with enough information to fully combat the threat. This requirement of having both stages together helps hide from defenders using automated analysis systems that are focused on individual files.
Why It Matters
Although not a new technique, the consistent popularity and utility of this approach to malware delivery merits attention. Threat actors abuse of operating system and AV reliance on file header recognition has been and will continue to be a problem. An example of threat actors abusing this reliance to trick AV systems as well as analysts was also recently covered by CofenseTM. Tuning AV systems to detect malware without relying on file headers is difficult and, in some cases, impossible. To properly recognize threats, it is important to have a full picture of the different components involved in an attack rather than attempting to organize individual and possibly incomplete analysis. To avoid this pitfall and better protect their network environments, organizations need to ensure that employees are trained to not fall victim to the phishing emails and that defenders are ready should an incident happen.
To stay ahead of emerging phishing and malware trends, sign up for free Cofense™ Threat Alerts.
All third-party trademarks referenced by Cofense whether in logo form, name form or product form, or otherwise, remain the property of their respective holders, and use of these trademarks in no way indicates any relationship between Cofense and the holders of the trademarks.