Voted the best overall enterprise email security 2023

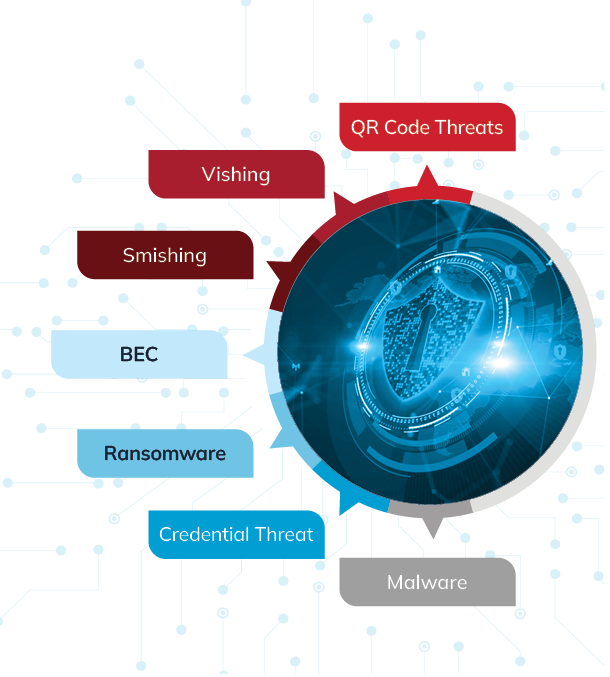
Vishing is a credible threat to your business.
Don't settle for
"good enough" email security
It only takes one breach to
What's most important to you?
Effective email security starts with Cofense.
Powered by the world's largest global network of 35M+ human reporters, we see and stop threats that others miss.
IDENTIFY
Train employees to spot & report threats with world-class Security Awareness Training (SAT).
DETECT
Leverage human intelligence, AI & email threat intelligence to identify real threats.
RESPOND
Automatically analyze, quarantine & eliminate email attacks in real-time.
The world's biggest brands trust Cofense.











Your SEG is missing these threats.
Protect your business with Cofense.
108SECONDS
We detect a malicious email bypassing one of our customer's standard email security solutions every 108 seconds.
99%
Cofense provides analysis on phishing threats with a 99.996% accuracy rate.
94%
Reduction in volume of threats to be manually investigated, easing your SOC workload.
Compliance standards you can trust.
Cofense maintains a group of compliances to ensure the integrity of our products and our internal operating procedures. We’re proud to continuously achieve ISO 27001, SOC 2 and FedRAMP Moderate as a display of our commitment to best practices and transparency.
See it in action today






