For a long time, attackers have used .zip files in order to carry their bad stuff to organizations. Typically attackers include the malware in an .exe or screensaver file in the .zip , but we’ve noticed attackers trying to tell a different story in a recent wave of attacks. Here’s a screenshot of one of the emails:

Once opened, the user is prompted to download a .zip file. We can see this in the iframe of the html file inside, as well as the .zip file that is downloaded.
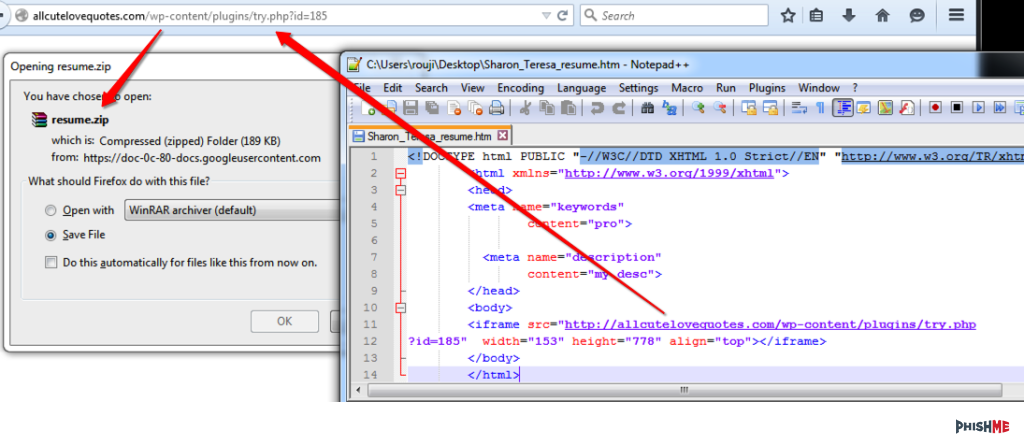
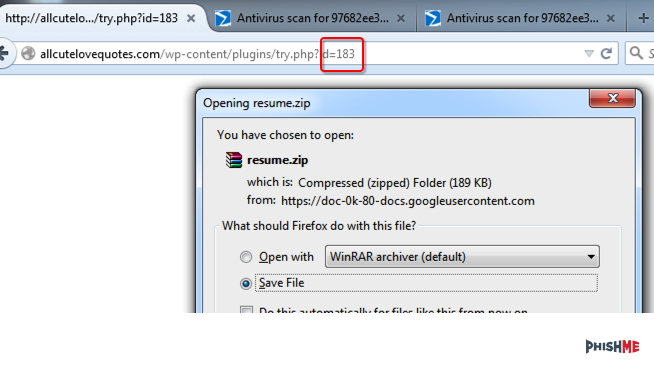
There are a few things to note here. In the original email, we were given the ID of 185 which gives us a possible 184 other recipients, not including others which may be higher. Testing ID 183 shows that there are other links to .zip files.
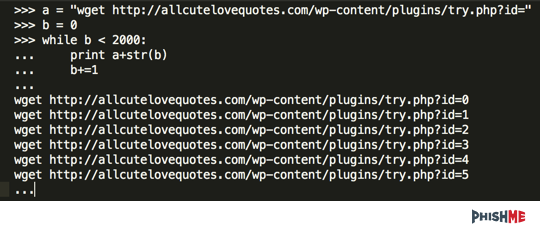
With python and a little wget, we can generate 2,000 links or so to see if there are other variants, since these seem to be hosted on Google Drive.
Looking at the file sizes, we can confirm that there are some differences and possibly different data. (Figure 5.)
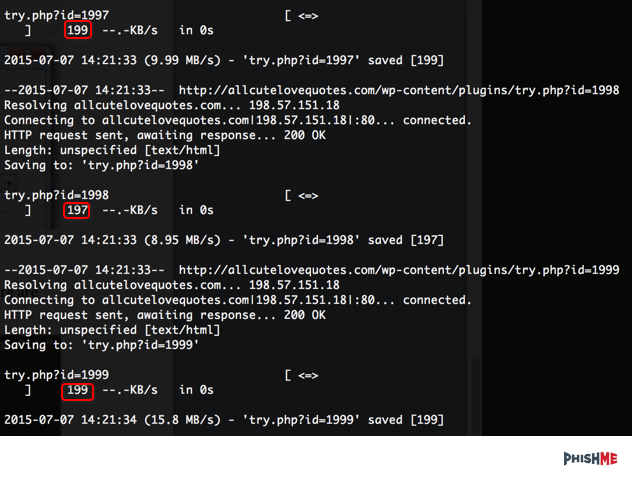
By looking at the one which has a different file size, we can see that there is a link to Google drive.
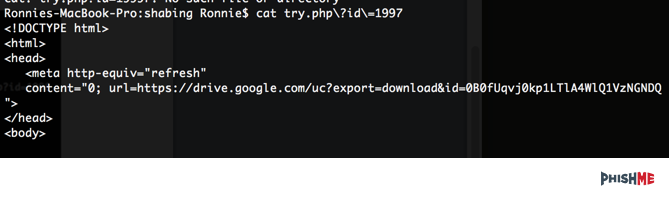
By looking at the contents and grepping the contents for drive.google.com, we can see that there are in fact other files present. There are a few duplicates, so we’ll have to clean them up.
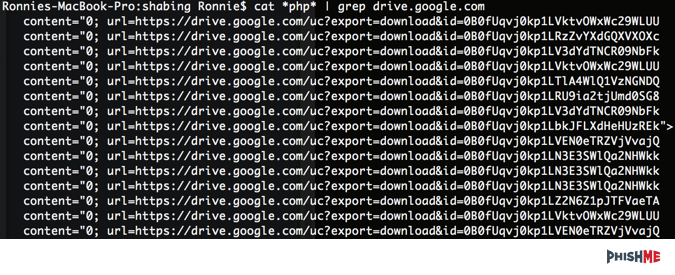
By using a little command-line kungfu, we can get down to the 10 links the attackers are trying to send.
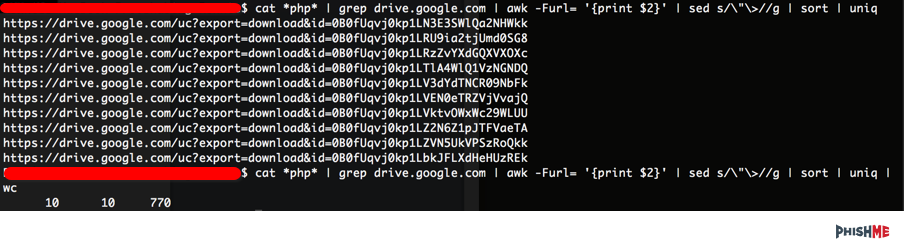
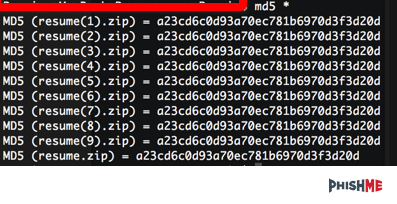
By downloading the 10 files, one would hope the attackers would make it difficult to analyze all 10 samples… but alas, it’s just the same file uploaded 10 times.
Once the malware is executed, we are presented with a familiar screen…CryptoWall 3.0!
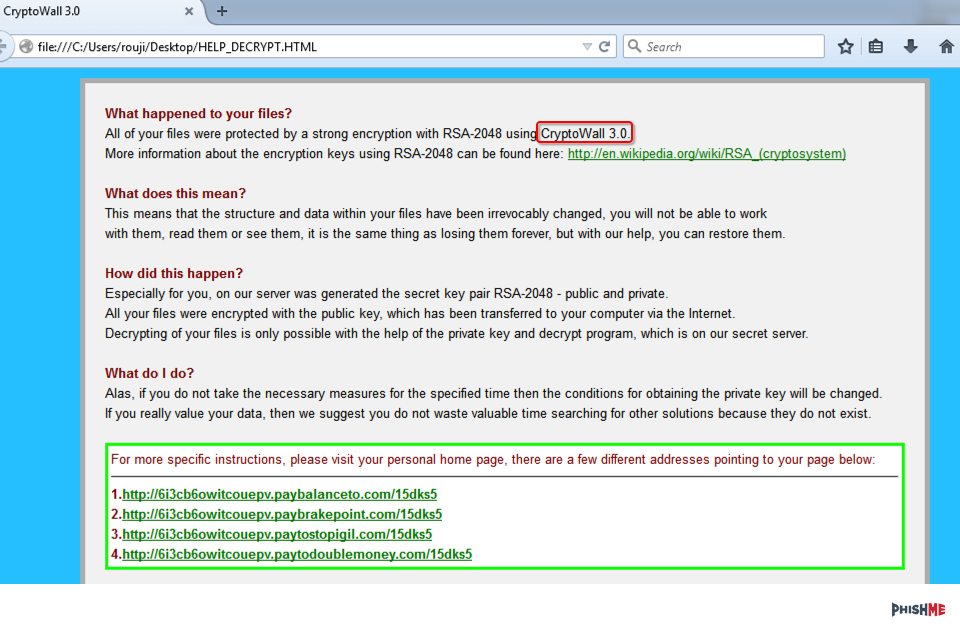
We’ve analyzed CryptoWall before and this variant shows nothing has really changed. For finding this in your network, one of the first requests is for mpc4u.couk, which appears to be a compromised domain.
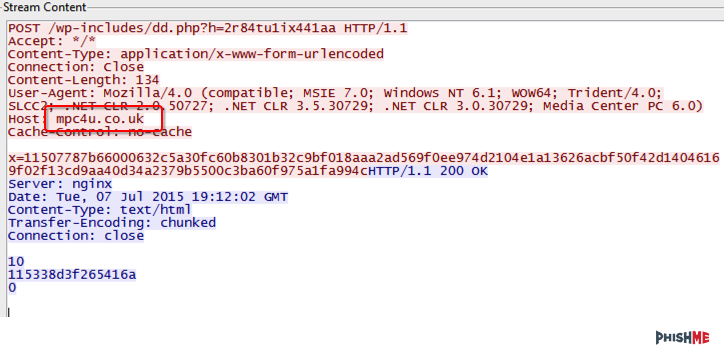
Next, the following domains should be search at the TLD:
http://6i3cb6owitcouepv.paybalancetocom/15dks5
http://6i3cb6owitcouepv.paybrakepointcom/15dks5
http://6i3cb6owitcouepv.paytostopigilcom/15dks5
http://6i3cb6owitcouepv.paytodoublemoneycom/15dks5
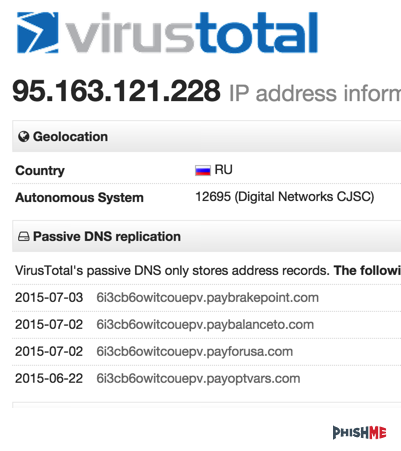
By using passive DNS built into VirusTotal, we’re able to look at the IP address to see what other things have resolved to the IP address of 95.163.121.228.
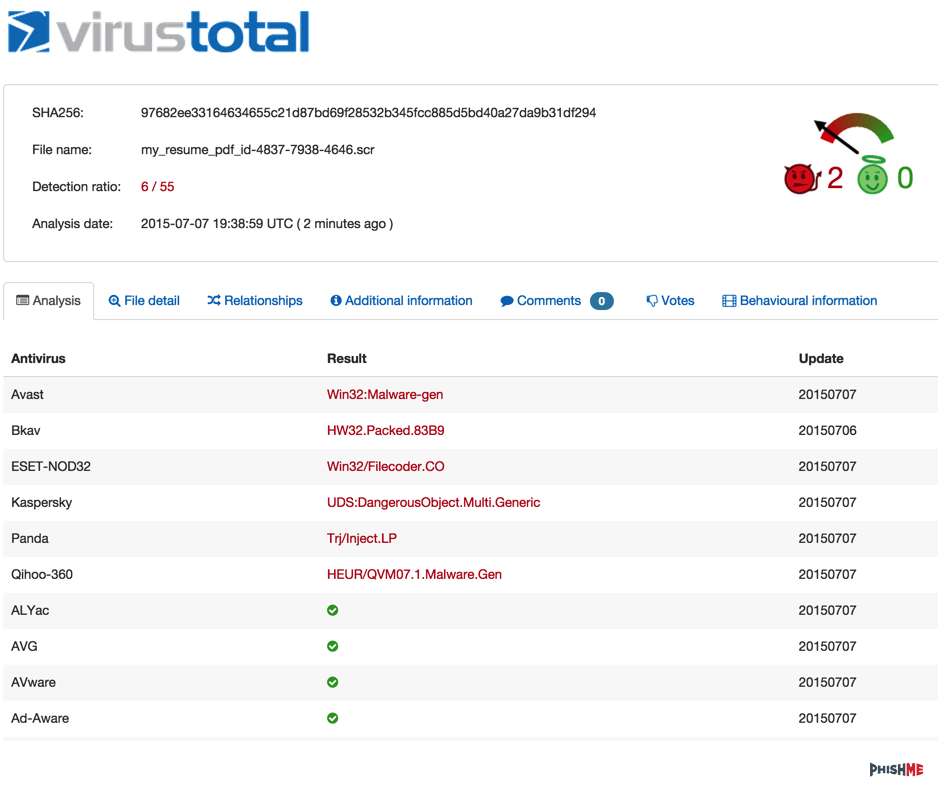
And as with most AV hits, we’re seeing a very low (6/55) detection rate.
While attackers are trying to get smarter, they are still trying to tell the same story to convince someone to click on an attachment. By using an html in a .zip file, this gives the attackers one more way to land in users’ inboxes, enticing them to click.


