Proofpoint
By Tej Tulachan
The Cofense Phishing Defense CenterTM (PDC) has prevented a phishing attack that attempts to steal users’ Office365 credentials by luring them with a fake payment order attachment. Hiding a malicious re-direct within a html file, threat actors bypassed the Proofpoint secure email gateway to try and steal users’ credentials.
Here’s how it works:
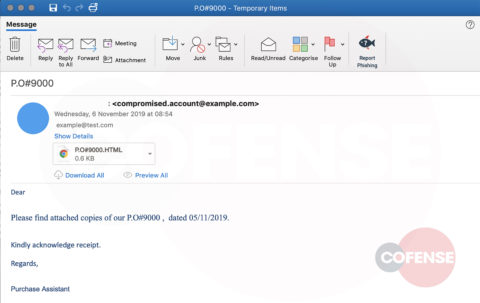
At first glance, the email appears to be a genuine communication originating from the accounts team of a relatively well-known company. The message body informs the recipient there is a payment order that requires processing. The message simply says, “Please find attached copies of our P.O#9000, dated 05/11/2019,” with the attachment to the email as a html file labelled “P.O#9000.” The html phishing email doesn’t specifically ask the user to open the attachment, however it does instruct the user to acknowledge receipt of the email. Any vigilant accountant would be inclined to check the contents of the bill as part of their workflow or processing procedures.
Malicious Attachment
If we take a deeper look into the source code of the html file, we can see that it only contains three lines of html code. The code takes advantage of the http-equiv attribute, used to trigger a page refresh of the user’s web browser and then load new content, which in this case is a URL to a phishing page. This happens almost instantly when the user opens the attachment.
Fig 2: Malicious URL
Phishing Page
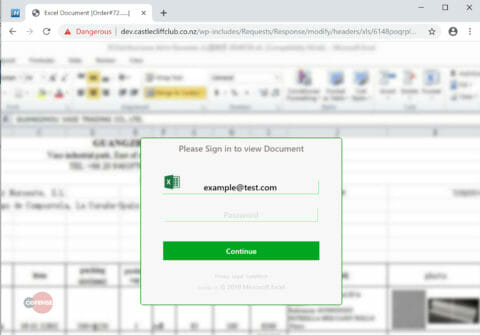
Once the attachment is opened the user is redirected to the phishing page as seen below in fig.3. The malicious page attempts to disguise itself as a genuine Microsoft Online Excel document, which most users would expect to see if they are editing documents on SharePoint. In the background we can see a blurred-out Excel spreadsheet with an authentication box obscuring the file contents. The user’s email address is auto populated in the dialog box, which asks the user to authenticate with his or her password.
Fig 3: Phishing Page
75% of threats reported to the Cofense Phishing Defense Center are credential phish. Protect the keys to your kingdom—condition end users to be resilient to credential harvesting attacks with Cofense PhishMeTM.
Over 91% of credential harvesting attacks bypassed secure email gateways. Remove the blind spot—get visibility of attacks with Cofense ReporterTM.
Quickly turn user-reported emails into actionable intelligence with Cofense TriageTM. Reduce exposure time by rapidly quarantining threats with Cofense VisionTM.
Attackers do their research. Every SaaS platform you use is an opportunity for attackers to exploit it. Understand what SaaS applications are configured for your domains—do YOUR research with Cofense CloudSeekerTM.
Thanks to our unique perspective, no one knows more about the REAL phishing threats than CofenseTM. To understand them better, read the 2019 Phishing Threat & Malware Review.
All third-party trademarks referenced by Cofense whether in logo form, name form or product form, or otherwise, remain the property of their respective holders, and use of these trademarks in no way indicates any relationship between Cofense and the holders of the trademarks. Any observations contained in this blog regarding circumvention of end point protections are based on observations at a point in time based on a specific set of system configurations. Subsequent updates or different configurations may be effective at stopping these or similar threats.